Note
The root flag can be found in the non-default location, C:\Users\Admin\Desktop.
Enum
- Portscan
$ export IP=10.129.73.15
$ rustscan --ulimit 10000 -a $IP -- -sCTV -Pn
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to https://10.129.73.15/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-10-23 17:54:49Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Hercules Corp
| ssl-cert: Subject: commonName=hercules.htb
| Subject Alternative Name: DNS:hercules.htb
| Issuer: commonName=hercules.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-04T01:34:56
| Not valid after: 2034-12-04T01:44:56
| MD5: 5f2d:5a1e:ddb2:3380:c69b:f57b:c5dc:3b03
| SHA-1: e7d6:740f:7eb5:4f00:3037:4bf9:6eb6:dad5:ed84:656b
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: hercules.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.hercules.htb
| Subject Alternative Name: DNS:dc.hercules.htb, DNS:hercules.htb, DNS:HERCULES
| Issuer: commonName=CA-HERCULES/domainComponent=hercules
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-04T01:34:52
| Not valid after: 2034-12-02T01:34:52
| MD5: 4555:8812:ecf9:9677:afc2:1897:9f20:766b
| SHA-1: eed0:eb69:2903:5bf6:a32a:5f5b:58a0:7b86:1868:6035
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
5986/tcp open ssl/http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=dc.hercules.htb
| Subject Alternative Name: DNS:dc.hercules.htb, DNS:hercules.htb, DNS:HERCULES
| Issuer: commonName=CA-HERCULES/domainComponent=hercules
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-04T01:34:52
| Not valid after: 2034-12-02T01:34:52
| MD5: 4555:8812:ecf9:9677:afc2:1897:9f20:766b
| SHA-1: eed0:eb69:2903:5bf6:a32a:5f5b:58a0:7b86:1868:6035
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
9389/tcp open mc-nmf syn-ack .NET Message Framing
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
52741/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
52751/tcp open msrpc syn-ack Microsoft Windows RPC
58958/tcp open msrpc syn-ack Microsoft Windows RPC
58967/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 64466/tcp): CLEAN (Timeout)
| Check 2 (port 42289/tcp): CLEAN (Timeout)
| Check 3 (port 32272/udp): CLEAN (Timeout)
| Check 4 (port 51402/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-10-23T17:55:49
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -17s- Update
/etc/hosts
echo "$IP hercules.htb dc.hercules.htb" | sudo tee -a /etc/hosts
10.129.73.15 hercules.htb dc.hercules.htb
- Visit https://hercules.htb/
- Note it is HTTPS
- Seems like a bunch of dead links and comical tidbits
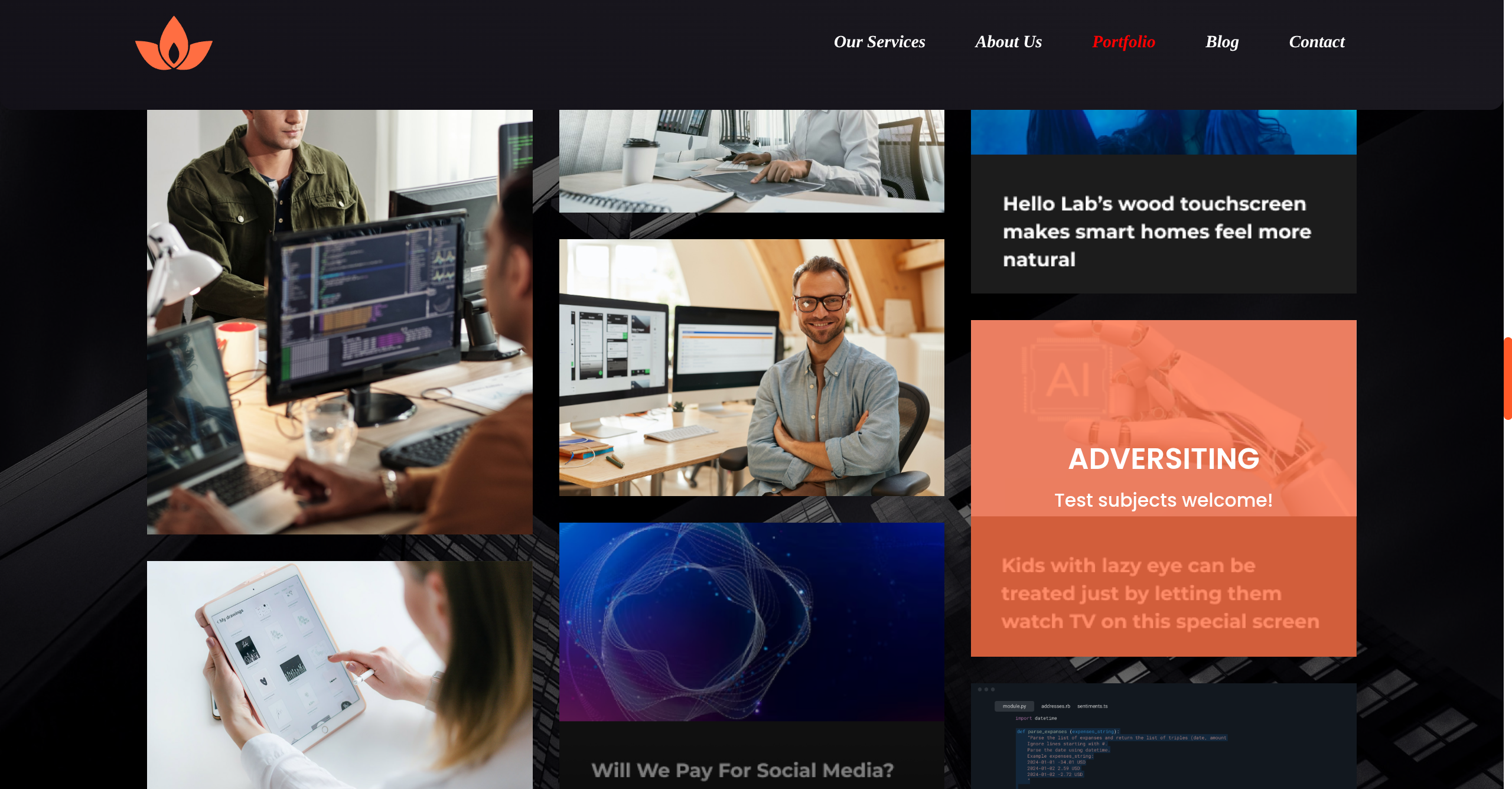
- We can try to find more endpoints via
gobuster - Need
-k -rflags in order to compensate for HTTPS
$ gobuster dir -u http://hercules.htb -w /usr/share/wordlists/dirb/common.txt -r -k
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://hercules.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/content (Status: 403) [Size: 0]
/Content (Status: 403) [Size: 0]
/Default (Status: 200) [Size: 27342]
/default (Status: 200) [Size: 27342]
/home (Status: 200) [Size: 3231]
/Home (Status: 200) [Size: 3231]
/index (Status: 200) [Size: 27342]
/Index (Status: 200) [Size: 27342]
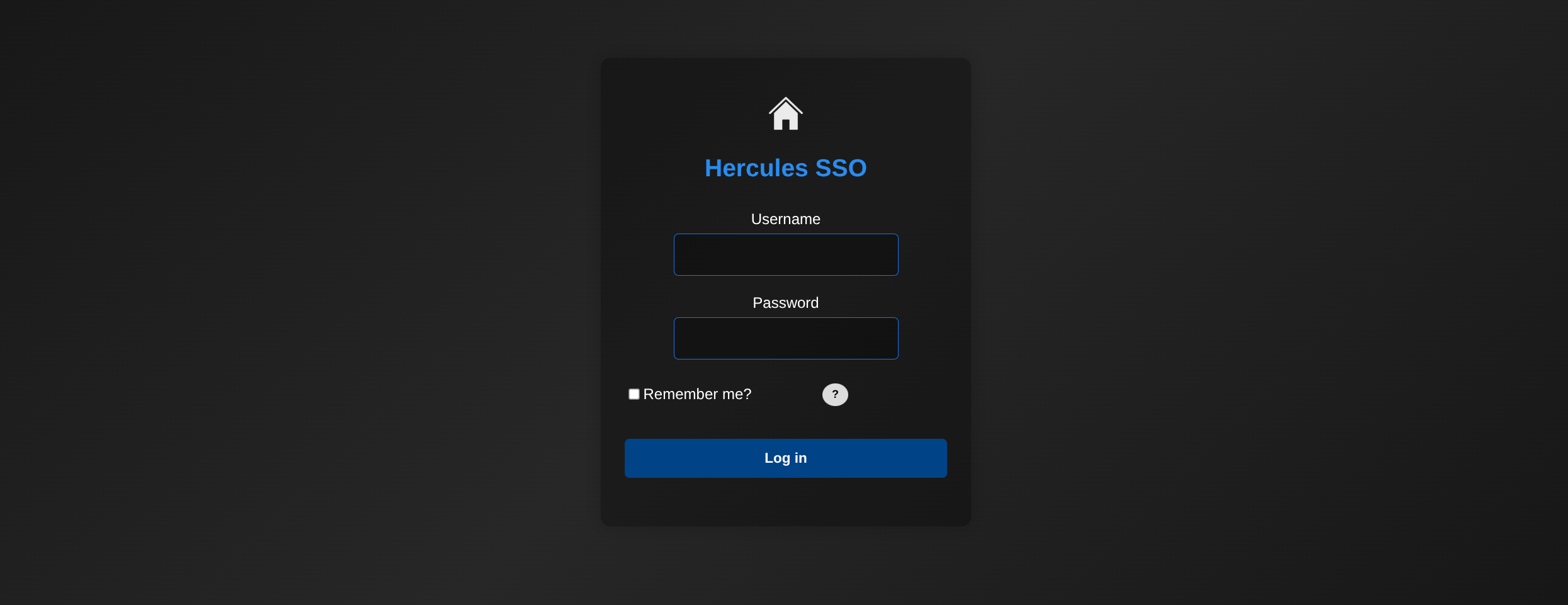
/login (Status: 200) [Size: 3213]
/Login (Status: 200) [Size: 3213]
Progress: 4613 / 4613 (100.00%)
===============================================================
Finished
===============================================================
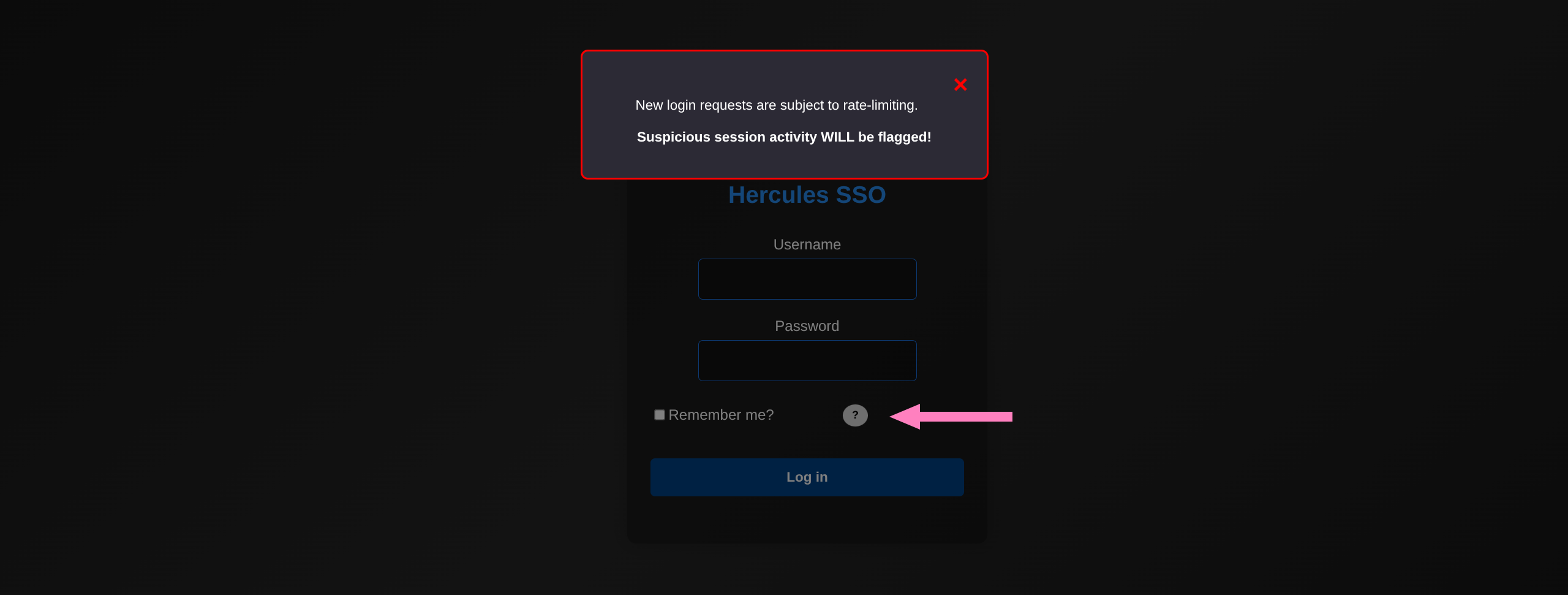
- Warns us that directly brute forcing the login fields will result in rate limiting